RansomHub: A New Ransomware Threat Targeting Windows, ESXi, Linux, and FreeBSD Systems
The RansomHub ransomware group has emerged as one of the most prolific cybercrime syndicates of 2024–2025. The group has expanded its arsenal to target Windows, VMware ESXi, Linux, and FreeBSD systems, employing advanced evasion techniques, cross-platform encryption, and exploiting vulnerabilities in enterprise infrastructure. Group-IB analysts have discovered that RansomHub has compromised over 600 organizations, including sectors such as healthcare, finance, and critical infrastructure RansomHub.
RansomHub Evolves To Attack Windows, ESXi, Linux and FreeBSD Operating Systems

Multi-OS Encryption Capabilities
RansomHub’s ransomware variants are tailored for diverse environments, featuring unique command-line arguments and encryption methods per platform. The following command illustrates how RansomHub operates:
RansomHub.exe -pass -fast -disable-net -skip-vm "VM1"
A JSON configuration file, decrypted at runtime, specifies whitelisted directories, kill lists for processes/services, and credentials for lateral movement. The ESXi encryptor disrupts virtual machines using vim-cmd commands, encrypting VM files (.vmdk, .vmx) with ChaCha20 and Curve25519 algorithms. A flaw in the /tmp/app.pid check allows defenders to prevent encryption by writing -1 to the file, forcing an infinite loop.
// Code snippet from ESXi encryptor if (access("/tmp/app.pid", F_OK) == 0) { pid_t pid = read_pid(); if (kill(pid, 0) == 0) { kill(pid, SIGKILL); exit(0); } }
The Linux variant uses intermittent encryption (1 MB chunks) and terminates services like syslog to hinder detection. The FreeBSD version, detected as Ransom.FreeBSD.INTERLOCK.THJBBBD, avoids critical directories and appends .interlock to files. RansomHub affiliates exploit vulnerabilities such as CVE-2024-3400 (Palo Alto firewalls) and CVE-2021-42278/CVE-2020-1472 (Active Directory) for initial access. 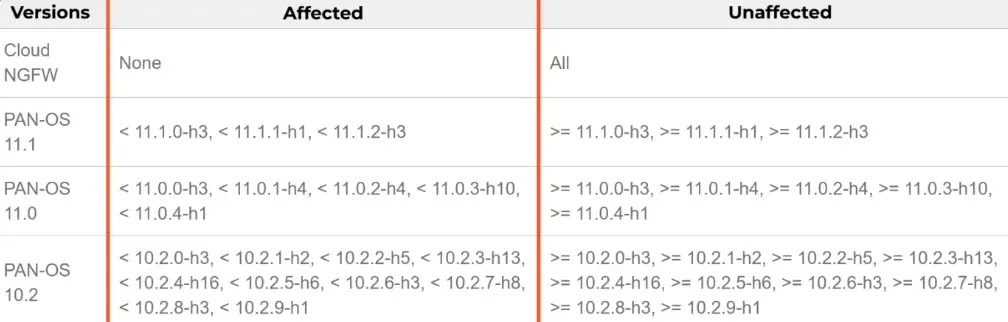
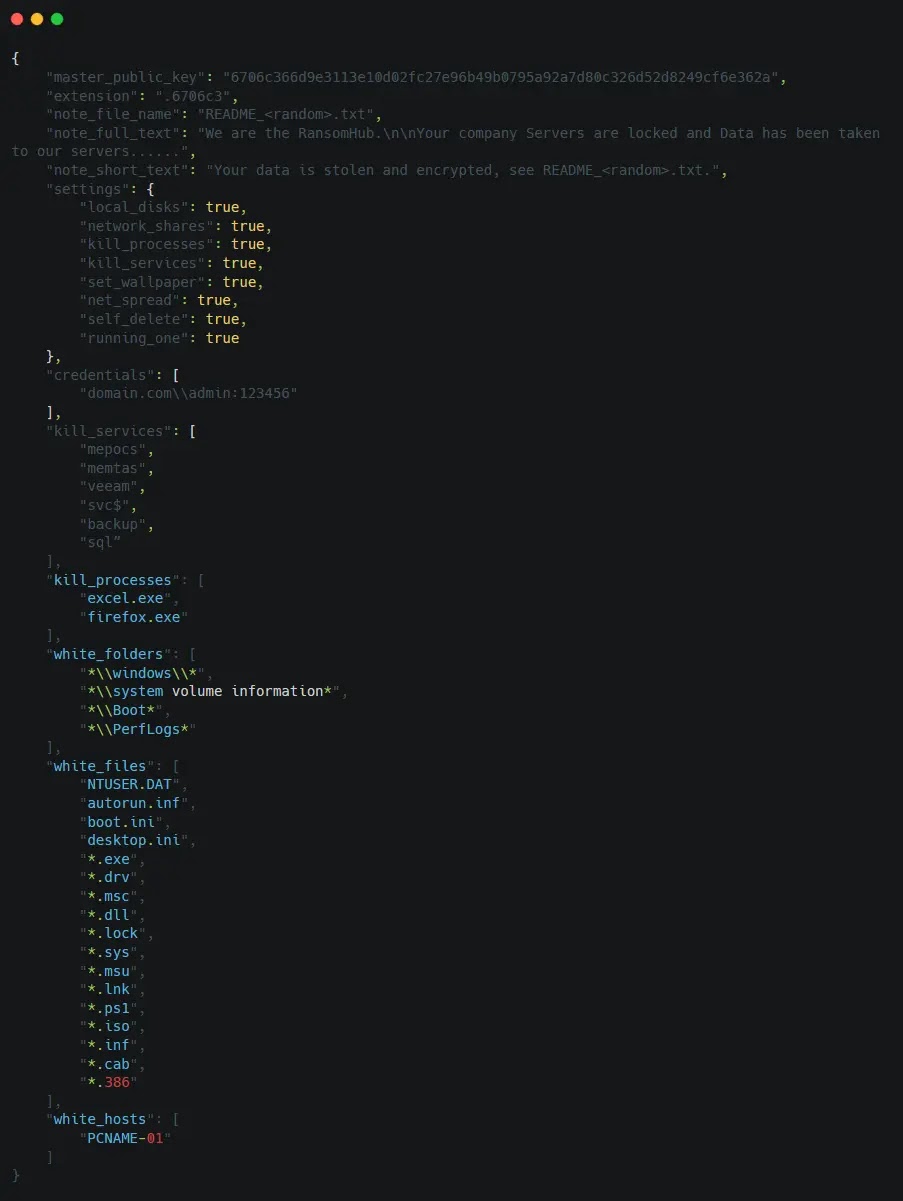 .webp) The group threatens victims with regulatory reporting (PDPL violations) to pressure payments, utilizing a decrypted configuration that includes details such as the master public key and processes to be killed.
.webp) The group threatens victims with regulatory reporting (PDPL violations) to pressure payments, utilizing a decrypted configuration that includes details such as the master public key and processes to be killed.
// Decrypted configuration snippet { "master_public_key": "a1b2c3...", "extension": ".6706c3", "note_file_name": "README.txt", "kill_processes": ["MsMpEng.exe", "TaniumCX.exe"] }
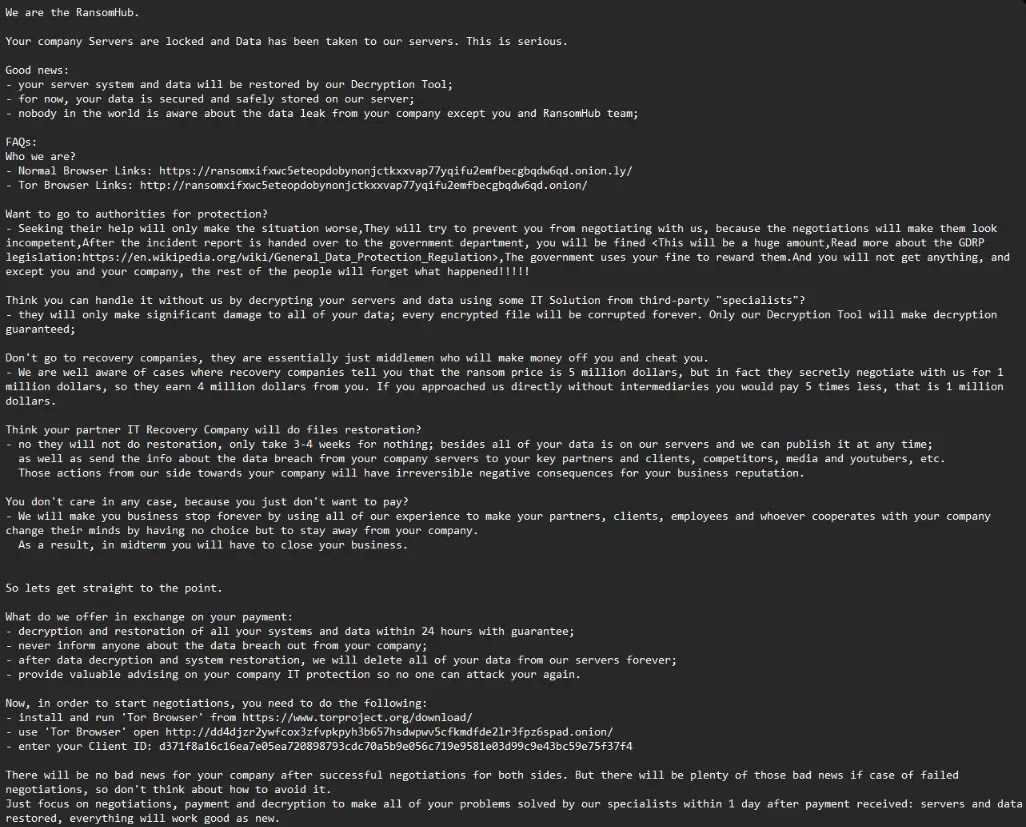
Play Ransomware Group’s New Linux Variant Targets ESXi
Trend Micro threat hunters have noted the emergence of a new Linux variant of the Play ransomware group that targets ESXi environments. The Play ransomware group is recognized for its double-extortion tactics and has expanded its attacks on Linux platforms. This variant is designed to verify if it runs on an ESXi environment before executing its malicious routines. The Play ransomware variant's infection routine mirrors that of its Windows counterpart, accepting command-line arguments for encrypting drives and files. It runs ESXi-related commands to scan and power off all VMs found in the environment. Once executed, the ransomware encrypts VM files, appending the extension “.PLAY” to the encrypted files. After the encryption process, a ransom note is dropped in the root directory, also displayed in the ESXi client login portal.
Exploring the Connection Between Prolific Puma and Play Ransomware
The analysis of the suspicious IP address associated with Play ransomware indicates a potential collaboration with Prolific Puma, a group known for generating domain names using a random destination generator algorithm. This relationship suggests that the Play ransomware group may be utilizing Prolific Puma's infrastructure and services to enhance its capabilities. To mitigate ransomware attacks, especially in ESXi environments, organizations should adopt best practices, including regular patching, strong access controls, and maintaining offline backups. VMware provides guidelines and best practices for securing ESXi environments.





