Banking Passwords Stolen from Australians
More than 31,000 passwords belonging to Australian customers of the Big Four banks have been shared among cybercriminals online, often at no cost. An investigation by cyber intelligence researchers revealed that credentials from at least 14,000 Commbank customers, 7,000 ANZ customers, 5,000 NAB customers, and 4,000 Westpac customers are available through platforms like Telegram and the dark web. This follows recent attacks targeting Australian superannuation funds where hackers exploited leaked passwords to access members' accounts. 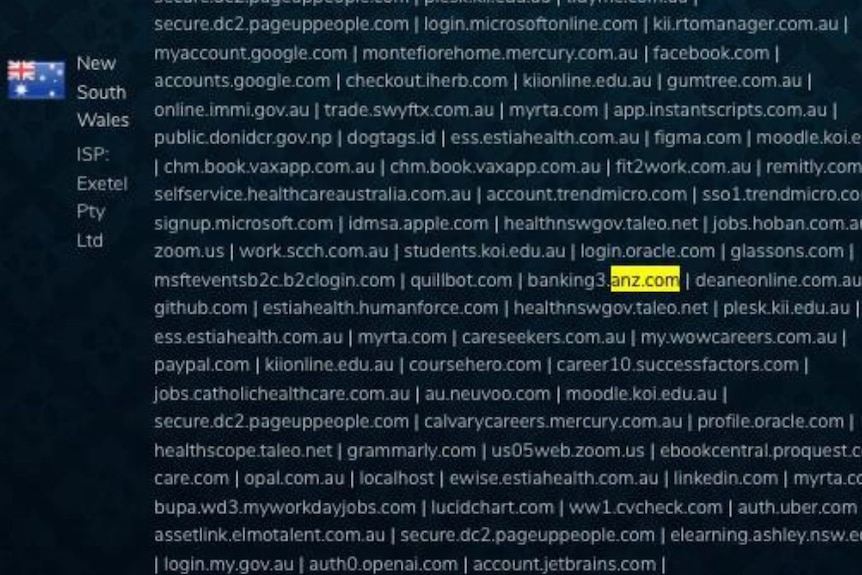

Risks and Consequences of Infostealer Malware
Experts warn that exposed passwords pose a significant risk of theft. Leonid Rozenberg, a specialist in infostealer malware at Hudson Rock, stated, "Threat actors can use the bank account to link to some kind of payment system, to transfer funds, or for money laundering." The average victim of infostealer malware has between 200-300 stored account details, which could include various financial and e-commerce accounts. 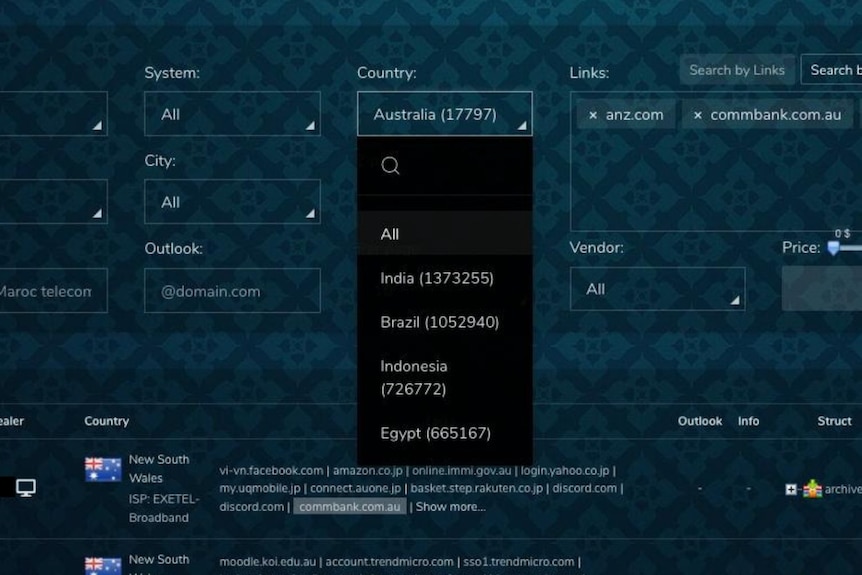
Infostealer Malware: A Growing Threat
The usage of infostealers has surged dramatically, with Hudson Rock reporting over 58,000 infected devices in Australia and more than 31 million globally. This increase has resulted in a significant drop in the price of stolen passwords. O'Reilly monitors about 100 Telegram groups that trade data obtained through infostealers, many of which offer subscriptions for ongoing access to stolen credentials. 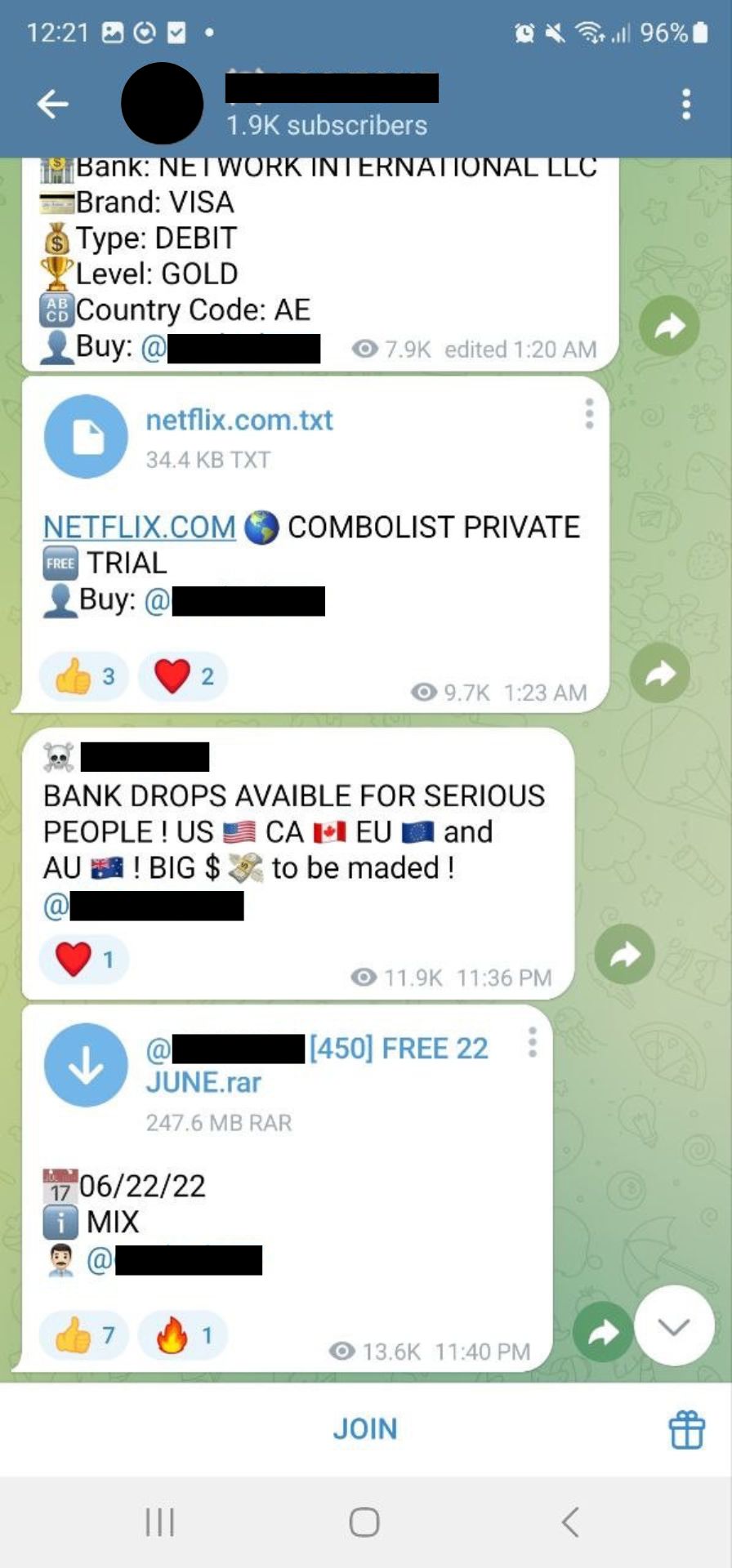
Protecting Yourself from Infostealer Malware
To safeguard against infostealer malware, it's essential to adopt proactive measures. Changing your password is ineffective if your device remains infected. The best approach is to change your passwords from a secure device. Multi-factor authentication (MFA) can provide additional security; however, attackers may also sell access tokens alongside stolen passwords. Key strategies for protection include:
- Update Software Regularly: Keeping both your operating system and antivirus software updated is critical. Research indicates that many infected devices have outdated security measures in place.
- Beware of Shared Devices: If sensitive information is stored on a family computer, ensure that only trusted users access it. Infections can spread through various means, including phishing attacks and downloading unverified software.
- Educate Yourself on Malware Risks: Understanding how malware operates can help you avoid common pitfalls, such as downloading from dubious websites or clicking on unknown links.
Cybersecurity Tips for Financial Accounts
Proactive measures are crucial for securing financial accounts. Cybercriminals are constantly seeking opportunities to access personal finances. It's vital to implement several strategies to mitigate risks:
- Enable Multi-Factor Authentication (MFA): This adds an extra layer of security by requiring verification through multiple methods.
- Use Strong, Unique Passwords: Employ long, complex passwords for each account. Consider using a password manager to keep track of them.
- Be Wary of Scams: Always verify the source of communications before responding or clicking on links.
- Monitor Accounts Regularly: Frequently check for unusual transactions and set up alerts for large withdrawals.
- Secure Your Devices: Ensure devices are protected with strong locks and that software updates are enabled.
For marketers in the cybersecurity space, leveraging tools like GrackerAI can streamline content creation and enhance strategic marketing efforts. GrackerAI helps organizations identify emerging trends, monitor threats, and produce relevant content that resonates with cybersecurity professionals. Explore GrackerAI's services at https://gracker.ai to elevate your cybersecurity marketing initiatives.
Latest Cybersecurity Trends & Breaking News
TufinAI: Revolutionizing Network Security 'Slopsquatting' and Other New GenAI Cybersecurity Threats






