New PAN-OS Authentication Bypass Vulnerability Exploited by Hackers
Alto Networks has released a patch for a high-severity authentication bypass vulnerability, identified as CVE-2025-0108, affecting their PAN-OS software. GreyNoise has observed active exploitation attempts targeting this vulnerability.
PAN-OS Authentication Bypass Vulnerability CVE-2025-0108
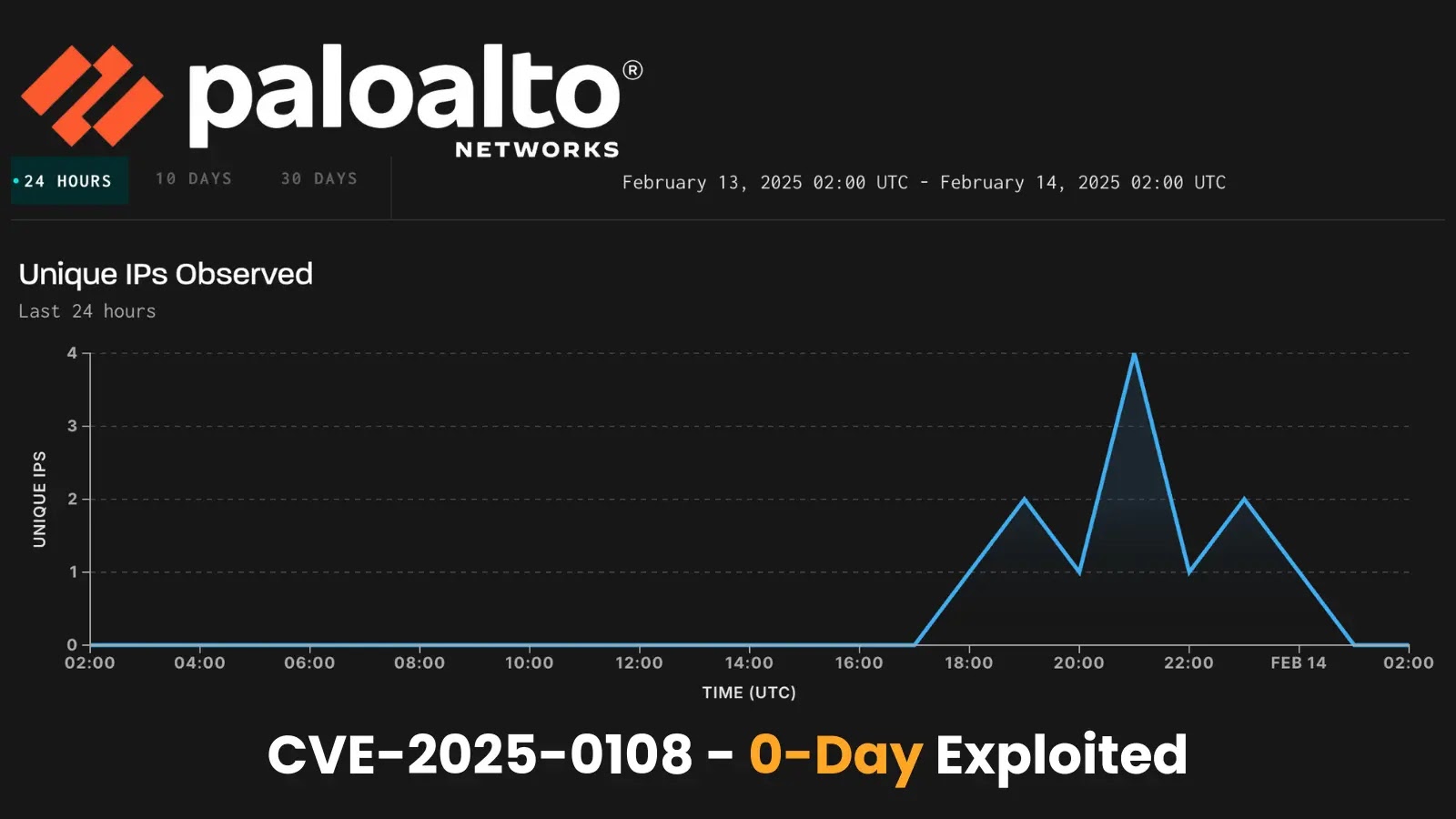
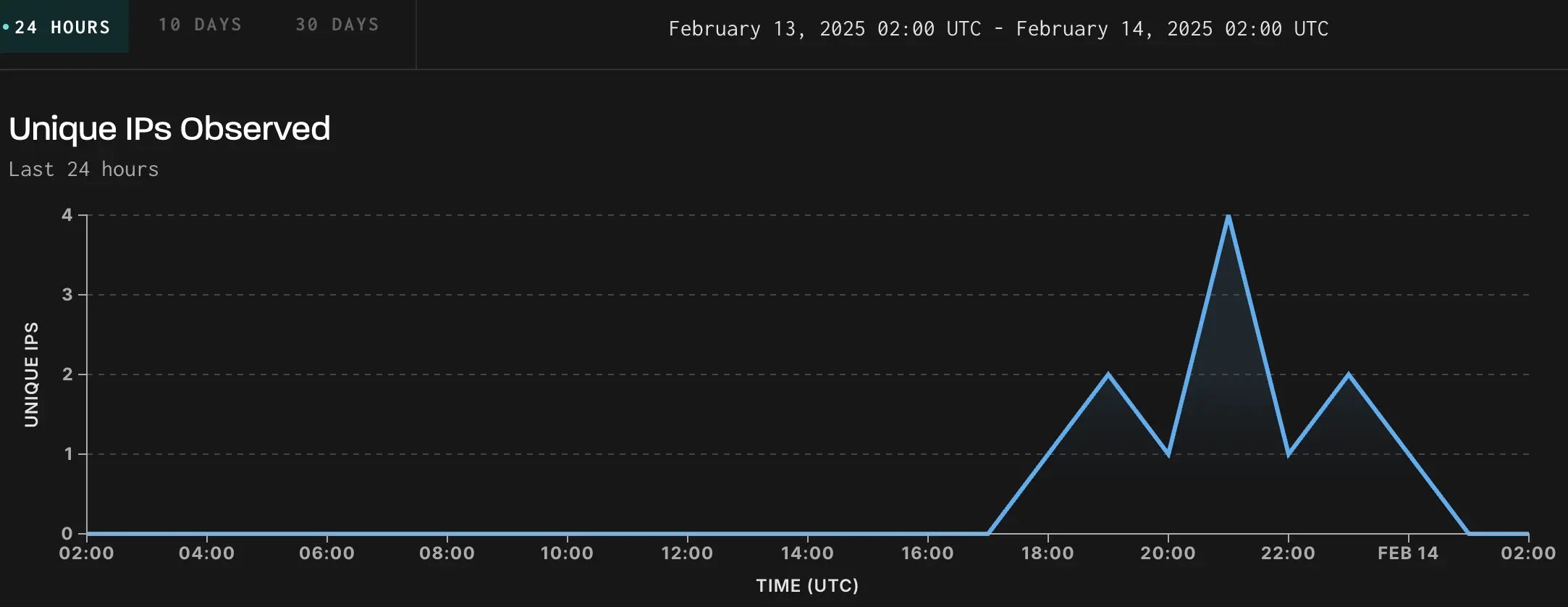
PAN-OS Authentication Bypass CVE-2025-0108 Details
The vulnerability, with a CVSS score of 7.8, was discovered by Assetnote researchers while analyzing patches for previously exploited vulnerabilities CVE-2024-0012 and CVE-2024-9474. The flaw originates from a path confusion issue between PAN-OS’s Nginx reverse proxy and Apache web server components. Attackers can craft malicious HTTP requests with multi-layered URL encoding, causing Nginx to incorrectly flag the request as non-sensitive (via the X-pan-AuthCheck: off header) while Apache processes it as a legitimate, authenticated request. This discrepancy allows attackers to access restricted PHP scripts, compromise configuration integrity and confidentiality, and exploit other vulnerabilities requiring authentication. Palo Alto Networks rates the flaw as CVSS 7.8–8.8, depending on network exposure. The severity drops to 5.9 if management interfaces are restricted to trusted IPs.
Active Exploitation and Mitigation Strategies
- 11.2 versions < 11.2.4-h4
- 11.1 versions < 11.1.6-h1
- 10.2 versions < 10.2.13-h3
- 10.1 versions < 10.1.14-h9
Cloud NGFW and Prisma Access are unaffected.
Mitigation Steps
- Immediate Patching: Upgrade to fixed PAN-OS versions.
- Network Hardening: Restrict management interface access to trusted IPs via firewall rules or VPNs.
- Monitoring: Use tools like GreyNoise to track exploitation trends.
Palo Alto Networks has not confirmed malicious exploitation but urges customers to prioritize updates. GreyNoise warns that organizations must assume unpatched devices are actively targeted.
Technical Analysis of the Vulnerability
Palo Alto Networks has disclosed a critical vulnerability (CVE-2025-0108) that allows attackers to bypass authentication on the management web interface. This flaw has been assigned a CVSS Base Score of 8.8, posing a significant risk to organizations using affected versions of PAN-OS. The vulnerability originates from a path confusion issue, which allows an unauthenticated attacker to invoke PHP scripts without proper authentication. While this does not allow remote code execution, it could compromise the integrity and confidentiality of the system. Affected Versions:
- PAN-OS 11.2 < 11.2.4-h4
- PAN-OS 11.1 < 11.1.6-h1
- PAN-OS 10.2 < 10.2.13-h3
- PAN-OS 10.1 < 10.1.14-h9
PAN-OS version 11.0 has reached its end of life (EOL) as of November 17, 2024, with no planned fixes.
Exploitation Risk and Recommended Actions
To mitigate this risk, Palo Alto Networks recommends restricting access to trusted internal IP addresses and following best practices for securing administrative access. Organizations are strongly advised to act promptly to secure their systems. Palo Alto Networks suggests:
- Upgrading affected systems to fixed versions.
- Restricting access to the management web interface using internal IPs only.
- Implementing a “jump box” system for accessing the management interface.
- Enabling Threat IDs through a Threat Prevention subscription to block potential attacks.
Organizations are encouraged to utilize real-time intelligence tools to track exploitation patterns and strengthen their defenses. Failure to act promptly could expose organizations to significant financial, operational, and reputational damage. 





