Understanding Why Cybersecurity Awareness Programs Fail in 2025
Most cybersecurity training programs fail because they aren't behaviorally engaging and rely on outdated formats. Human error remains the leading cause of security breaches. According to the Verizon 2024 Data Breach Investigations Report, over 74% of breaches involve a human element, often stemming from simple mistakes like clicking phishing links or mismanaging credentials.
The Disengagement Issue
Despite widespread implementation of cybersecurity awareness programs, many employees ignore training due to the disconnect between how people learn and how cybersecurity is taught. Employees are overloaded and often unmotivated when training feels irrelevant or punitive.
Best Practices for Preventing Security Fatigue
Security fatigue is a phenomenon where employees become overwhelmed by constant warnings and compliance requirements. According to a report from the National Institute of Standards and Technology (NIST), this leads to avoidance of security best practices (NIST Security Fatigue Study).
Key insights include the need for relevant messaging and avoiding cognitive overload, as demonstrated by research from the Frontiers in Psychology Journal (Frontiers in Psychology, 2023).
Personalizing Cybersecurity Training
Generic training doesn’t reflect the real risks different departments face. The Cybersecurity & Infrastructure Security Agency (CISA) recommends role-based cybersecurity training tailored to specific tasks and risks (CISA Cybersecurity Training Guide).
The Impacts of Fear-Based Messaging
Fear-based messaging is often counterproductive, leading to avoidance behavior rather than proactive learning. A study from the SANS Institute shows that positive reinforcement leads to higher participation and behavior change (SANS Security Awareness Report).
Addressing Habituation
Employees may ignore security alerts if they become routine. Research from Stanford University indicates that habituation reduces attention to real threats (Stanford Behavioral Cybersecurity Research).
The Psychology of Engagement
Organizations should focus on fostering genuine behavioral change. Traditional programs often emphasize compliance over practical learning.
Behavioral Change Models
Ebbinghaus Forgetting Curve: Without reinforcement, individuals may forget up to 80% of new information within a month. Effective strategies include microlearning and spaced repetition (Wikipedia – Die freie Enzyklopädie).
Cognitive Load Theory: Overwhelming learners with excessive information can hinder processing and retention. Simplifying training materials through clear objectives and relatable examples is essential.
Habit Formation: Small, consistent actions lead to sustainable behavioral change. Rewarding secure behaviors and providing immediate feedback are effective strategies.
Brightside AI’s Approach
Brightside AI exemplifies behavior-first principles with AI-driven microlearning, real-time reinforcement, and adaptive training modules (Brightside AI).
Fixing the Problem: 5 Research-Backed Strategies
Gamification: Incorporating game-like elements enhances engagement. AES shifted to a gamified phishing training platform, increasing participation from 10% to 60-70% (Hoxhunt).
Microlearning: Delivering content in short bursts improves retention. The Ponemon Institute found that concise, role-relevant training leads to better outcomes (Ponemon Institute Cybersecurity Training Benchmark Study).
Role-Specific Training: Tailoring content to job functions leads to higher retention and behavioral change. For example, HR professionals should focus on threats involving personal data access.
Personalized Simulations: Realistic simulations enhance preparedness. The Ponemon Institute found that incorporating realistic simulations delivers the greatest ROI (Security Innovation Cybersecurity).
Making Cybersecurity Personal: Connecting practices to personal lives fosters commitment. Personal risk assessments and family inclusion are effective approaches.

Case Study: IGT’s Transformation
IGT faced high phishing failure rates and low engagement due to traditional training. The company shifted to a behavior-first model, implementing gamified training and personalized phishing simulations.
The results were immediate: phishing failure rates dropped from 30% to just 4-6%, and employee engagement soared to over 56%.
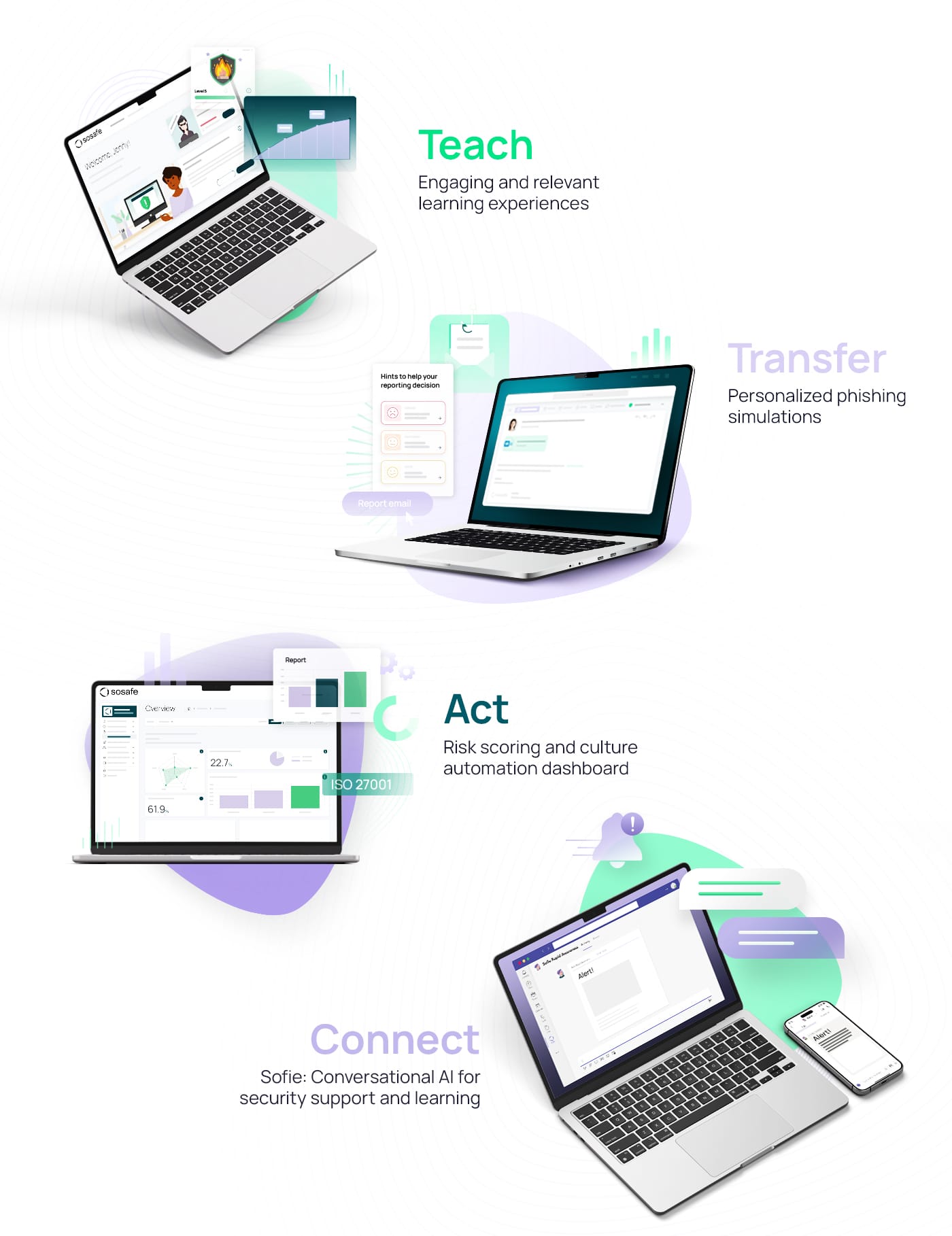
Human Risk Management in Cybersecurity
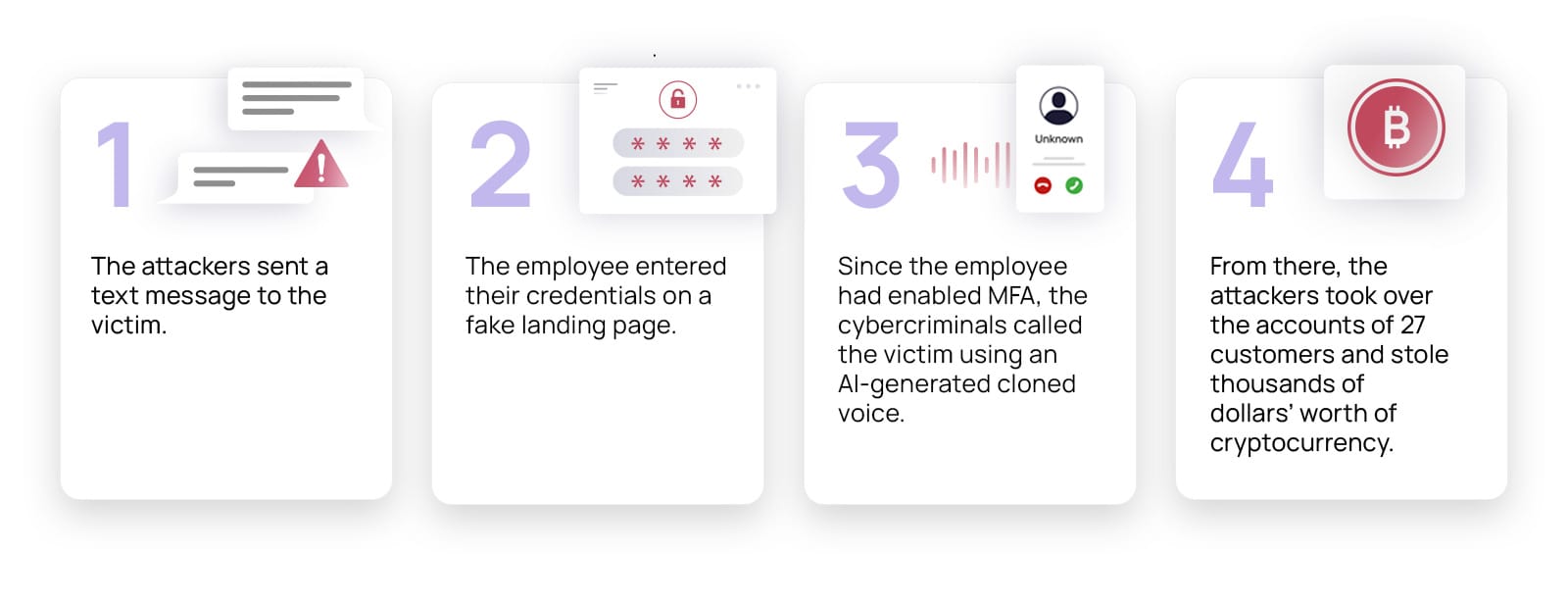
A behavioral-based human risk management approach is essential in combating cyber threats. A study by SoSafe revealed that 90% of breaches involve human error. With the rise of AI-driven attacks, traditional defenses must evolve.
To mitigate risks, training programs should prioritize human-related risks specific to an organization and foster behaviors that enable employees to identify and respond to threats.
SoSafe focuses on creating security cultures that protect against digital threats while involving individuals in reducing human-related risks.