Output Messenger Flaw Exploited in Espionage Attacks
A Türkiye-backed cyberespionage group, known as Marbled Dust, exploited a zero-day vulnerability in Output Messenger, specifically targeting users linked to the Kurdish military in Iraq. The flaw, identified as CVE-2025-27920, is a directory traversal vulnerability in the LAN messaging application. Microsoft Threat Intelligence analysts reported that this vulnerability could allow authenticated attackers to access sensitive files outside the intended directory or deploy malicious payloads on the server's startup folder. "Attackers could access files such as configuration files, sensitive user data, or even source code, and depending on the file contents, this could lead to further exploitation, including remote code execution," stated Srimax, the app's developer, in a security advisory released when the bug was patched with Output Messenger V2.0.63. The hacking group, also tracked as Sea Turtle and UNC1326, specifically targeted users who had not updated their systems. By compromising the Output Messenger Server Manager application, Marbled Dust hackers could steal sensitive data, access user communications, impersonate users, and disrupt operations. Microsoft assessed that Marbled Dust likely used DNS hijacking or typo-squatted domains to intercept and reuse credentials. After gaining access, the attackers deployed a backdoor (OMServerService.exe) onto victims' devices, which checked connectivity against an attacker-controlled command-and-control domain (api.wordinfos[.]com) and provided further information to identify each victim. 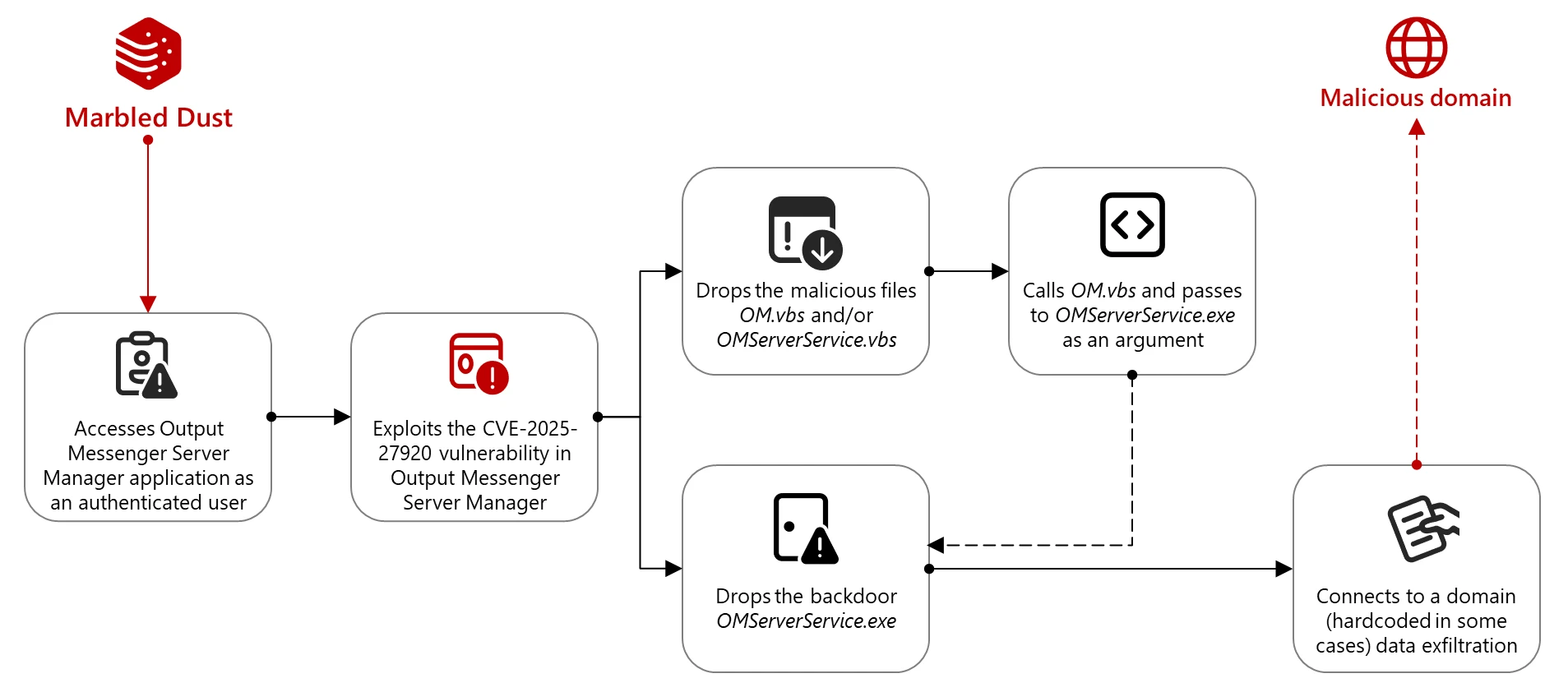
Trends in Zero-Day Exploitation
Response and Remediation Strategies
Upon the discovery of the zero-day vulnerability in Output Messenger, Srimax acted quickly to release patches for CVE-2025-27920 and a related vulnerability (CVE-2025-27921). Microsoft recommends that organizations using Output Messenger immediately upgrade to the latest version to mitigate risks. Key recommendations include:
- Network Monitoring: Flag and review traffic to domains and IP addresses associated with Marbled Dust infrastructure, particularly api.wordinfos[.]com.
- Malicious File Search: Actively search for known malicious file hashes and script names such as OMServerService.vbs, OMServerService.exe, and OMClientService.exe in endpoint and network logs.
- Credential Reset: Assume that credentials handled by compromised Output Messenger instances are at risk; arrange for organization-wide password resets.
Additionally, organizations can utilize advanced detection and response tools to monitor network flows and maintain visibility across endpoints. GrackerAI’s tools assist in automating the generation of insights from industry developments, allowing marketing teams to create timely, relevant content for cybersecurity professionals. To explore our services or learn more about how GrackerAI can enhance your cybersecurity marketing efforts, visit GrackerAI.
Latest Cybersecurity Trends & Breaking News
Data Breaches Digest - Week 14 2025 LockBit Revelations Following Major Takedown





