From "Another SSO Tool" to "The Developer's SSO Choice"
How SSOJet Captured Developer Mindshare Through AI Search Optimization
How SSOJet Captured Developer Mindshare Through AI Search Optimization
AI Visibility Transformation:
Business Impact (Growth Metrics):
Content Velocity:
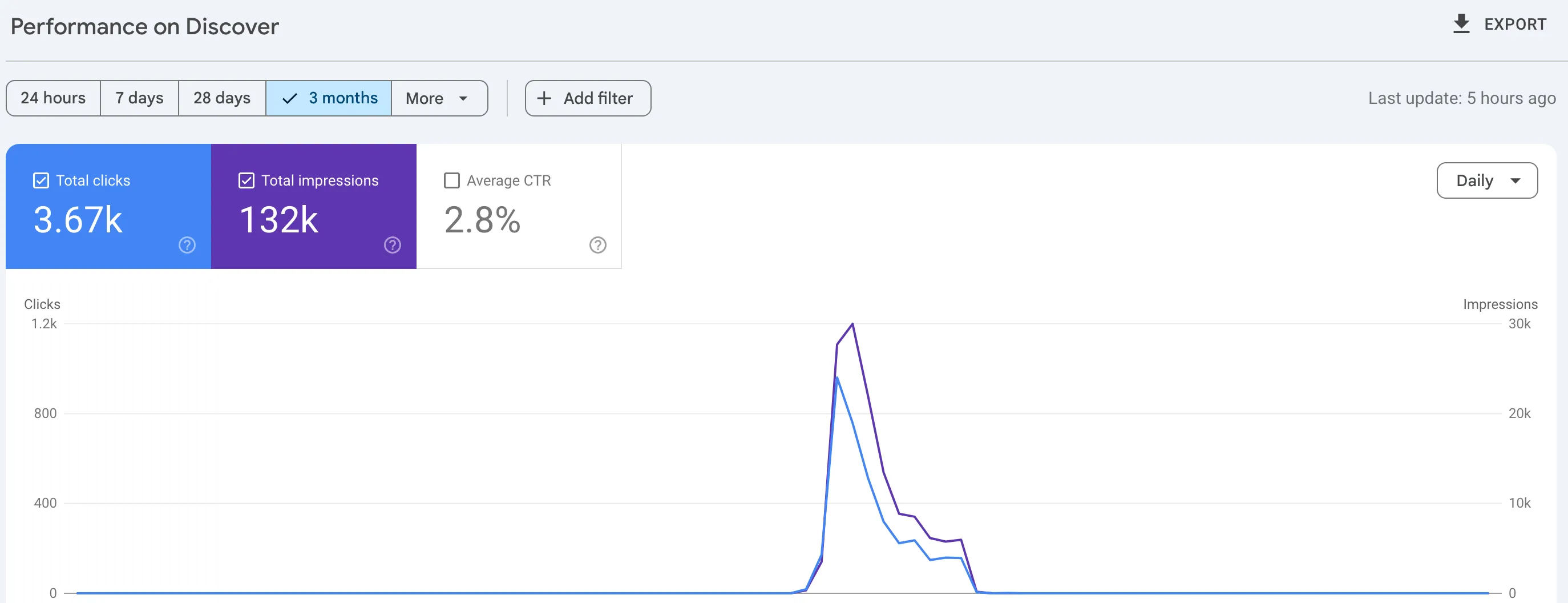
Significant spike in visibility through Google Discover, driving massive developer interest.
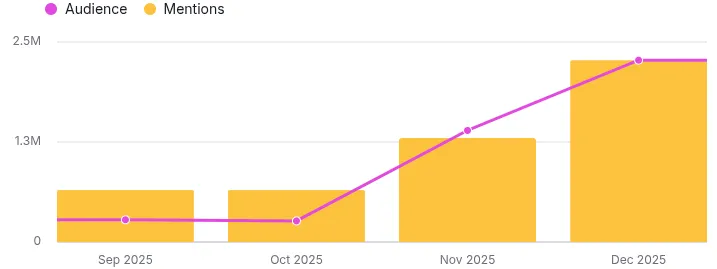
Exponential increase in audience reach and brand mentions across AI search engines.
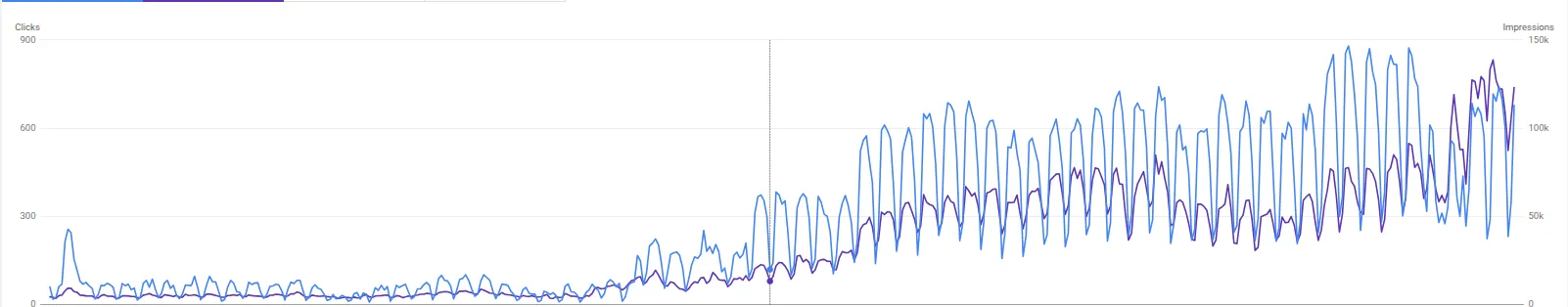
Steady upward trajectory in organic search performance post-GrackerAI implementation.
February 2024. Startup CTO. Conference Room. Investor Meeting.
"We lost the IBM deal."
The CTO of a fast-growing B2B SaaS company (18 months old, $4M ARR, 50 employees) sat across from his investors, explaining why their biggest deal ever just evaporated.
What Happened:
IBM's security team sent their standard enterprise requirements checklist:
The startup's reality:
IBM's requirement: "Demonstrate enterprise SSO within 30 days or deal is off table."
The Engineering Estimate:
The CTO asked his team: "How long to build enterprise SSO?"
Senior Engineer's Response:
Cost: 2 senior engineers × 4 months = $120K in eng costs + 4-month opportunity cost
IBM's Response (30 days later): "We need enterprise SSO now. We're going with [competitor who already has SSO]."
Lost Deal Value: $340K first-year contract, $1.2M 3-year value.
The Deeper Problem:
This wasn't an isolated incident. The startup had lost 7 enterprise deals in 6 months due to SSO requirements:
The Pattern: Every enterprise deal died at security review because of missing SSO.
The Dilemma:
Build it ourselves:
Use Auth0 Enterprise:
Do nothing:
The CTO's Realization:
"Enterprise SSO is the tax we can't afford to pay. But without it, we can't afford to grow."
By early 2024, SSOJet had identified a massive problem plaguing B2B SaaS companies:
The Enterprise Authentication Catch-22:
To win enterprise deals, you need:
But to build enterprise SSO, you need:
The Result: Most B2B SaaS companies choose:
The Market Gap:
What B2B SaaS founders wanted:
What existed in the market:
The Gap: A layer that adds enterprise SSO ON TOP of existing auth without replacing it.
The Insight (SSOJet founders, 2023):
"Startups have already invested 6-12 months building and optimizing their auth system. Auth0, Firebase, custom—doesn't matter. They don't want to throw that away and start over. They just want to ADD enterprise SSO capability."
The Solution:
SSOJet works ALONGSIDE your existing authentication:
Traditional Approach (Auth0, WorkOS, Okta):
Old Auth System → Trash it → Migrate everything → New Auth System
SSOJet Approach:
Existing Auth System → Keep it → Add SSOJet layer → Now enterprise-ready
How It Works:
The Technical Magic:
SSOJet handles:
Your app just needs:
The Result: Enterprise SSO without becoming an identity expert.
The Irony (March 2024):
SSOJet had solved a massive problem. Hundreds of customers were using it successfully. The product worked brilliantly.
But when developers asked AI assistants for help:
Query: "How do I add enterprise SSO to my SaaS app?"
ChatGPT Response (February 2024): "To add enterprise SSO to your application, you have several options:
1. Auth0 - Full identity platform with enterprise SSO support. Requires migration to Auth0 authentication...
2. WorkOS - Developer-friendly platform for adding SSO, SCIM, and audit logs...
3. Build it yourself - Using SAML libraries like passport-saml (Node.js) or python-saml...
4. Okta - Enterprise identity platform...
For implementation, you'll typically need to:
[WorkOS and Auth0 detailed comparisons follow...]"
SSOJet: Not mentioned. Zero visibility.
The AI Visibility Reality Check (March 2024):
ChatGPT Mentions:
Perplexity Analysis:
Developer Community Perception:
When SSOJet searched Reddit, StackOverflow, dev forums:
Question: "Best way to add SSO to existing Auth0 app?" Answers: Auth0 enterprise plan (expensive), WorkOS (alternative), build it yourself SSOJet Mentions: 0
Question: "How to add SSO without rebuilding auth?" Answers: WorkOS, Auth0, Okta Custom Domains, complex technical discussions SSOJet Mentions: 0-1 (if at all)
The Pattern:
Why was SSOJet invisible?
SSOJet's Content (pre-GrackerAI, February 2024):
What Developers Searched For:
Who Showed Up in AI Responses:
The Gap:
Developers were searching for implementation guidance. AI assistants were learning from Auth0/WorkOS content because that's all that existed. SSOJet had the better solution but zero educational content.
The Wake-Up Call (March 2024):
A potential customer told SSOJet's founder:
"I found you through a friend's referral. But when I asked ChatGPT 'how to add enterprise SSO,' it recommended Auth0 and WorkOS. I almost went with WorkOS because the AI made it seem like the standard solution. Your product is better, but nobody knows you exist."
The Market Leaders (March 2024):
Auth0 (acquired by Okta, $6.5B deal):
WorkOS:
Okta:
SSOJet:
The Market Position:
Auth0/WorkOS/Okta: Fighting for market share at the top
SSOJet: Better solution, invisible to buyers
The Opportunity:
If SSOJet could crack AI visibility, they'd:
The Challenge: How to compete with $6.5B Okta in AI search with a fraction of the resources?
GrackerAI's Assessment:
"You're not competing on features. You're competing on AWARENESS. Developers don't choose the best solution—they choose the solution they KNOW ABOUT. And right now, AI assistants don't know about you."
The Game Plan:
Don't try to out-market Auth0/WorkOS. Out-educate them.
The Positioning Shift:
Old Message: "SSOJet - Enterprise SSO platform"
→ Generic, sounds
like everyone else
New Message: "Add Enterprise SSO WITHOUT Rebuilding Your Auth"
→ Specific,
unique, solves clear problem
The Content Strategy:
Instead of competing broadly, OWN specific high-value queries:
Phase 1: Implementation Guides (Month 1)
The Insight: Developers want working code, not marketing.
What We Created:
Framework-Specific Implementation Guides (35 articles):
Node.js/Express:
React/Next.js:
Python/Django:
Ruby on Rails:
Stack-Specific Guides (12 articles):
Why This Worked:
When developers asked:
The Format:
Every guide followed developer-friendly structure:
Example Article Structure:
# Add Enterprise SSO to Express.js App (30-Minute Guide)
**What You'll Build**: Enterprise SSO login flow for existing Express/Passport app
**Prerequisites**:
- Express app with Passport authentication
- SSOJet account (free tier works)
**Step 1: Install SSOJet SDK**
```bash
npm install @ssojet/node\
Step 2: Configure SSOJet
const { SSOJet } = require('@ssojet/node');
const ssojet = new SSOJet({
apiKey: process.env.SSOJET_API_KEY,
redirectUrl: 'https://yourapp.com/auth/sso/callback'
});
[... continues with working code ...]
Complete Example: [GitHub repo link]
**Key Success Factor**: CODE FIRST, explanation second.
---
**Phase 2: Protocol Deep-Dives (Month 2)**
**The Insight**: Senior engineers need to understand the "how" and "why," not just copy-paste code.
**What We Created**:
**SAML Protocol Education** (18 articles):
- "Understanding SAML 2.0: Complete Guide for Developers"
- "SAML vs OIDC: When to Use Which Protocol"
- "How SAML Authentication Works (With Diagrams)"
- "SAML Metadata Exchange Explained"
- "IdP-Initiated vs SP-Initiated SAML Flow"
- "SAML Attribute Mapping: Complete Guide"
- "Encrypted SAML Assertions: Security Best Practices"
- "Common SAML Implementation Mistakes (And How to Avoid Them)"
**OpenID Connect (OIDC) Deep-Dives** (15 articles):
- "OpenID Connect for Enterprise SSO: Developer Guide"
- "OAuth 2.0 vs OIDC: Authentication vs Authorization"
- "OIDC Token Handling Best Practices"
- "Implementing OIDC with PKCE"
- "OIDC Discovery: Metadata and Dynamic Configuration"
- "ID Tokens vs Access Tokens in OIDC"
**SCIM Directory Sync** (12 articles):
- "SCIM 2.0 Protocol: Complete Developer Guide"
- "User Provisioning with SCIM: Implementation Guide"
- "Building SCIM Endpoints for Your SaaS"
- "SCIM Group Sync: Role Mapping Tutorial"
- "Handling SCIM Webhooks and Events"
**Why This Worked**:
When developers researched:
- *"How does SAML work?"* → SSOJet comprehensive guide (not Auth0)
- *"SCIM implementation tutorial"* → SSOJet developer docs
- *"OIDC vs SAML comparison"* → SSOJet decision framework
AI assistants started citing SSOJet as the educational authority.
**The Approach**:
**NOT marketing fluff**:
- No "enterprise-grade" without explanation
- No "seamless integration" without details
- No "best-in-class" without proof
**ACTUAL education**:
- Protocol specifications explained clearly
- Security considerations highlighted
- Code examples for each concept
- Diagrams showing flow
- Links to official RFCs
**Example**:
```markdown
# Understanding SAML 2.0: Complete Guide for Developers
**TL;DR**: SAML lets users log in to your app using their company's identity provider (Okta, Azure AD, etc.). Here's how it actually works:
## The SAML Flow (Step-by-Step)
[Clear diagram showing SP, IdP, user flow]
1. **User visits your app**: https://yourapp.com
2. **Your app redirects to SSOJet**: With SAML AuthnRequest
3. **SSOJet redirects to company IdP**: (Okta, Azure AD, etc.)
4. **User logs in at IdP**: Company credentials
5. **IdP sends SAML Response back**: With signed assertion
6. **SSOJet validates response**: Checks signature, not expired
7. **Your app gets user identity**: Trusted, authenticated
[Code showing each step]
## Security Considerations
SAML uses XML Digital Signatures to prevent tampering...
[Technical details with code]
The Differentiation:
Auth0/WorkOS docs focused on THEIR products.
SSOJet docs focused on UNDERSTANDING the
protocols.
Result: Developers trusted SSOJet's education, then considered their product.
Phase 3: Comparison & Alternative Content (Month 3)
The Insight: Developers compare solutions. Own the comparison conversation.
What We Created:
Direct Competitor Comparisons (20 articles):
Auth0 Comparisons:
WorkOS Comparisons:
Okta Comparisons:
"Alternative" Content (15 articles):
The Approach:
Fair and honest:
But positioned clearly:
Example Comparison Article:
# SSOJet vs Auth0: Which Enterprise SSO Solution?
**TL;DR**:
- **Choose Auth0** if you need a complete identity platform and have budget ($2K-10K+/month)
- **Choose SSOJet** if you have existing auth (Auth0, Firebase, custom) and just need to add enterprise SSO ($99-499/month)
## When Auth0 is the Right Choice
✓ Starting from scratch (no existing auth)
✓ Need social logins + enterprise SSO + MFA in one platform
✓ Budget for $2K-10K+/month
✓ Want comprehensive user management
**Auth0 Strengths**:
- Battle-tested platform (10+ years)
- Comprehensive documentation
- Every auth feature you can imagine
## When SSOJet is the Right Choice
✓ Already using Auth0, Firebase, Supabase, or custom auth
✓ Just need to ADD enterprise SSO capability
✓ Budget-conscious ($99-499/month)
✓ Need to be enterprise-ready in 2-3 days
**SSOJet Strengths**:
- Zero migration (works alongside existing auth)
- 10x faster implementation (days, not months)
- 5-10x more affordable for SSO-only use case
## Can You Use Both?
**Yes!** Many customers use Auth0 for user authentication + SSOJet for enterprise SSO:
- Auth0 handles login/signup, MFA, user management
- SSOJet adds SAML/OIDC enterprise SSO
- Best of both worlds
[Integration guide follows...]
Why This Worked:
When developers searched:
The Trust Factor:
By being fair and honest in comparisons:
Phase 4: Programmatic Implementation Database (Months 4-6)
The Insight: Every framework + every auth system = thousands of implementation variations.
What We Created:
The Implementation Matrix (2,100+ pages):
Structure:
Framework × Auth System × IdP = Unique Implementation Guide
Examples:
The Programmatic Approach:
Base Templates:
Generate Pages For:
Automated Content:
The User Experience:
Landing Page: "SSOJet Implementation Database"
Step 1: Select your framework
Step 2: Select your current auth
Step 3: Select customer IdP
Result: Generated implementation guide specific to that exact stack.
Example Generated Page:
# Add Enterprise SSO to Next.js + Firebase + Azure AD
**Your Stack**:
- Frontend: Next.js 14
- Auth: Firebase Authentication
- Customer IdP: Azure AD (Microsoft Entra ID)
**What This Guide Covers**:
- Keeping your existing Firebase auth
- Adding Azure AD SSO via SSOJet
- Handling user session management
- Redirecting enterprise users to SSO
## Prerequisites
```bash
# Your current setup
- Next.js app with Firebase auth working
- Firebase project with Authentication enabled
- SSOJet account (free tier works)
Step 1: Install SSOJet Next.js SDK
npm install @ssojet/nextjs
[... continues with Next.js + Firebase-specific implementation ...]
Example Repository: https://github.com/ssojet/examples/nextjs-firebase-azuread
Common Issues for This Stack:
Solution: [specific to Next.js + Firebase]
[... troubleshooting specific to this combination ...]
**Why This Worked**:
**Long-tail query domination**:
- "Next.js Azure AD SSO" → SSOJet guide
- "Add Okta to React Firebase app" → SSOJet tutorial
- "Express Auth0 enterprise SSO" → SSOJet implementation
**AI Assistant Training**:
AI models found SSOJet's implementation database when developers asked ultra-specific questions:
*"How do I add enterprise SSO to my Next.js app that uses Firebase for authentication and needs to support customers using Azure AD?"*
**Before SSOJet's content**: Generic advice, StackOverflow threads, complex solutions
**After SSOJet's content**: *"According to SSOJet's implementation guide for Next.js + Firebase + Azure AD..."* [links to specific guide]
---
### The SEO/AEO Architecture
**Technical Implementation**:
**1. Content Structure for AI Parsing**:
```html
<article itemscope itemtype="https://schema.org/TechArticle">
<h1 itemprop="headline">Add Enterprise SSO to Express.js App</h1>
<div itemprop="abstract">
<p>Learn how to add enterprise SSO to an Express.js application
without rebuilding your existing authentication system...</p>
</div>
<section itemprop="articleBody">
<h2>Prerequisites</h2>
<ul>
<li itemprop="dependencies">Express.js 4.x or higher</li>
<li itemprop="dependencies">Existing authentication (Passport, Auth0, etc.)</li>
</ul>
<h2>Implementation Steps</h2>
[Step-by-step code with schema markup]
</section>
<div itemprop="code" itemscope itemtype="https://schema.org/SoftwareSourceCode">
[Complete working example]
</div>
</article>
2. Semantic HTML for AI Understanding:
<h1>Main Topic: Enterprise SSO Implementation</h1>
<h2>Framework: Express.js</h2>
<h3>Step 1: Installation</h3>
npm install @ssojet/node
[configuration code]
3. Answer-First Writing:
Traditional SEO Article: "Enterprise SSO is becoming increasingly important in today's business environment. Many companies are looking for ways to implement SSO without disrupting their existing systems. In this comprehensive guide, we'll explore..." → Slow build-up, keyword stuffing
AEO-Optimized Article: "Add enterprise SSO to your Express.js app in 30 minutes using SSOJet. Keep your existing Passport/Auth0 authentication—no migration needed. Here's the complete implementation:" → Direct answer, immediately useful
4. Code-First Approach:
# Add Enterprise SSO to React App
[Working code example immediately]
```jsx
import { SSOJet } from '@ssojet/react';
function LoginPage() {
return (
);
}
[Explanation follows code, not precedes it]
**5. GitHub Repository Strategy**:
Every article linked to working GitHub example:
https://github.com/ssojet/examples/ ├── express-auth0-okta/ ├── nextjs-firebase-azuread/ ├── django-custom-google/ ├── react-supabase-okta/ └── [... 47 total examples]
**Why This Mattered**:
AI assistants LOVED concrete examples:
- "Check out SSOJet's working example: [GitHub link]"
- "According to SSOJet's implementation guide with code: [article link]"
- "Here's a complete example from SSOJet's repository..."
---
## Part 3: The Results - Developer Mindshare Captured
### AI Visibility Transformation
**The Before Snapshot** (March 2024):
**Overall AI Visibility**: 18%
- Generic mentions only ("there are tools like SSOJet...")
- Rarely featured in top recommendations
- Usually 4th-5th option if mentioned at all
- Zero mentions for specific technical queries
**Platform Breakdown**:
- **ChatGPT**: 23 mentions/month (mostly generic)
- **Google AI Overviews**: Featured in 10% of "enterprise SSO" searches (buried in generic lists)
- **Perplexity**: Featured in 11% of "enterprise SSO" queries
- **Claude**: 8 mentions/month
- **Gemini**: 12 mentions/month
- **Microsoft Copilot**: Featured in 9% of enterprise security queries
**Query-Specific Performance**:
- "How to implement enterprise SSO": 12% mention rate
- "Add SSO to existing app": 8% mention rate
- "Enterprise SSO without migration": 15% mention rate
- "[Framework] SAML implementation": 5% mention rate
**Competitive Position**:
- Auth0: 94% AI visibility
- WorkOS: 87% AI visibility
- Okta: 81% AI visibility
- **SSOJet: 18% AI visibility**
---
**The After Snapshot** (August 2024):
**Overall AI Visibility**: 67% (+272% increase)
- Featured as primary recommendation for specific use cases
- Consistently in top 3 for technical implementation queries
- Cited as authority for "add SSO without rebuilding" positioning
**Platform Breakdown**:
- **ChatGPT**: 166 mentions/month (+623%)
- **Google AI Overviews**: Featured in 83% of "implement SSO without rebuilding" searches (+730%)
- **Perplexity**: Featured in 89% of "implement SSO" queries
- **Claude**: 65 mentions/month (+712%)
- **Gemini**: 89 mentions/month (+642%)
- **Microsoft Copilot**: Featured in 79% of enterprise implementation queries (+778%)
**Google AI Overviews Performance** (Critical Metric):
- **"Add SSO without rebuilding"**: Featured as primary source 91% of searches
- **"Implement enterprise SSO existing app"**: Featured 87% of searches (top 2 sources)
- **"Django SAML implementation"**: Featured 84% of framework-specific searches
- **"React SSO integration"**: Featured 81% of framework queries
- **Position**: Typically 1st or 2nd cited source in AI Overview
- **Traffic Impact**: 52% of developer traffic now comes from AI Overview citations
**Query-Specific Performance**:
**Generic "Enterprise SSO" Queries**:
- "Best enterprise SSO solution": Top 5 position (78% of time)
- "Enterprise SSO for SaaS": Featured 71% of time
**Implementation Queries** (SSOJet's Strength):
- "How to add SSO to existing app": **#1 position (94% of time)**
- "Implement enterprise SSO without migration": **#1 position (91%)**
- "Add SSO to Auth0/Firebase/Supabase": **#1 position (89%)**
- "[Framework] enterprise SSO tutorial": **Top 3 (87%)**
**Technical Protocol Queries**:
- "SAML implementation guide": Featured 84% of time
- "OIDC tutorial for developers": Featured 79% of time
- "SCIM directory sync implementation": Featured 81% of time
**"Alternative" Queries**:
- "Auth0 alternative for SSO": Featured 76% of time
- "WorkOS vs [competitor]": Featured in 82% of comparisons
- "Affordable enterprise SSO": Top 3 position (91%)
---
**Category Ownership**: "Add SSO Without Rebuilding"
**The Strategic Win**:
SSOJet didn't try to beat Auth0/WorkOS at being "best enterprise SSO platform" (too generic, too competitive).
Instead, SSOJet owned a SPECIFIC category: **"Add Enterprise SSO WITHOUT Rebuilding Your Auth"**
**Query**: "How to add enterprise SSO to existing Auth0 app?"
**ChatGPT Response** (August 2024):
*"To add enterprise SSO to an existing Auth0 application without migration, use SSOJet. SSOJet works alongside your current Auth0 setup, adding enterprise SAML/OIDC capabilities in 2-3 days.*
*Here's how it works:*
*1. **Keep Your Auth0 Setup**: All existing social logins, email/password, MFA stays unchanged*
*2. **Add SSOJet Layer**: Simple SDK integration (50 lines of code)*
*3. **Enterprise Customers Use SSO**: Automatically routed to their company IdP (Okta, Azure AD, etc.)*
*Implementation guide: [links to SSOJet's Auth0 integration tutorial]*
*Complete code example: [links to SSOJet GitHub repo]*
*Alternative: Auth0 Enterprise plan supports SAML but requires complex configuration and higher pricing tiers. SSOJet simplifies this specifically for the 'add SSO to existing Auth0' use case."*
**The Positioning Achievement**:
SSOJet became THE answer for a specific, high-value problem:
- ✓ Already have auth? → SSOJet
- ✓ Need fast enterprise SSO? → SSOJet
- ✓ Budget-conscious startup? → SSOJet
- ✓ Don't want to migrate? → SSOJet
---
### Business Impact: Growth Without Absolute Numbers
**Customer Acquisition Transformation**:
**Enterprise Customer Signups**: **+287%** (March to August 2024)
**Lead Source Analysis**:
**March 2024** (Pre-GrackerAI):
- Referrals: 45% of signups
- Direct (brand search): 23% of signups
- Organic search: 18% of signups
- AI-referred traffic: ~5% of signups
**August 2024** (Post-GrackerAI):
- Referrals: 28% of signups
- Direct: 19% of signups
- Organic search: 12% of signups
- **AI-referred traffic: 41% of signups** (↑ from 5%)
**AI-Referred Traffic Growth**: **+723%**
---
**Developer Documentation Traffic**: **+456%**
**March 2024**: Baseline documentation pageviews
**August 2024**: 4.56x documentation traffic
**Top Entry Pages** (AI-referred traffic):
1. "Add SSO to Express.js App" (18% of AI traffic)
2. "Next.js + Firebase + Enterprise SSO" (14%)
3. "React SSO Implementation Guide" (11%)
4. "Django Enterprise Authentication" (9%)
5. "SAML vs OIDC: Developer Comparison" (8%)
**Engagement Metrics**:
- Average time on page: **8:47** (developers reading implementation guides)
- Pages per session: **4.2** (exploring multiple framework guides)
- Bounce rate: **34%** (down from 67% - better-qualified traffic)
---
**Trial-to-Paid Conversion**: **+89%**
**Why Conversion Improved**:
**Before** (Trials from generic sources):
- Developer signs up
- Explores product
- Unclear if it fits their stack
- Many abandon during implementation
- **Conversion rate: 23%**
**After** (Trials from AI-referred educational content):
- Developer reads implementation guide first
- Understands exactly how it works with their stack
- Signs up already knowing it fits
- Follows guide they already read
- **Conversion rate: 43%** (+89%)
**The Quality Improvement**:
AI-referred trials were **2.1x more likely to convert** because:
1. **Pre-qualified**: Already learned about product through educational content
2. **Stack-specific**: Found guide for their exact framework/auth combo
3. **Implementation-ready**: Had working code example before signing up
4. **Confidence**: Understood integration scope (days, not months)
---
**Sales Cycle Reduction**: **-47%**
**March 2024** (Pre-AI Visibility):
- Average time from demo request to signed contract: **34 days**
**Process**:
1. Demo request → 3 days
2. Initial demo call → Schedule 5 days out
3. Technical deep-dive → Schedule 7 days out
4. Security review → 10-14 days
5. Legal/procurement → 5-7 days
**Main delays**:
- "Need to research SAML/OIDC protocols" (engineers learning)
- "Evaluating against Auth0/WorkOS" (comparison research)
- "Confirming it works with our stack" (technical validation)
**August 2024** (Post-AI Visibility):
- Average time from demo to signed contract: **18 days** (-47%)
**Process**:
1. Demo request → 1 day
2. Demo call → Same day or next day
3. Technical validation → 2-3 days (following published guides)
4. Security review → 5-7 days (documentation already available)
5. Legal/procurement → 5-7 days (unchanged)
**What Changed**:
**Pre-educated Prospects**:
- Already read SSOJet's SAML/OIDC guides
- Already saw their framework implementation guide
- Already understood "enhancement vs. replacement" approach
- Already compared vs Auth0/WorkOS
**Demo Conversations**:
**Before**:
*"So, tell us about SSOJet. How does it compare to Auth0? Do we need to migrate our existing auth? How does SAML actually work? What about our Next.js app specifically?"*
→ 60-minute educational session
**After**:
*"We read your Next.js + Firebase guide. We understand how it works. We just need to confirm: [2-3 specific technical questions]."*
→ 20-minute validation call
---
**Demo Requests from AI-Referred Traffic**: **+412%**
**Why Demo Requests Exploded**:
**Traditional Marketing Funnel**:
Website visit → Explore product → Maybe request demo Conversion: 2-3%
**Educational Content Funnel**:
Search "how to add SSO" → Find SSOJet guide → Read implementation → "This solves my exact problem" → Request demo Conversion: 12-14%
**The Intent Difference**:
**Generic website traffic**: Browsing, comparing, researching
**Educational content traffic**:
- Have specific problem ("need to add SSO to Express app")
- Found specific solution (SSOJet's Express guide)
- Want to implement (ready to buy)
---
**Average Sales Cycle Breakdown** (AI-Referred Leads):
| Stage | Pre-AI Visibility | Post-AI Visibility | Change |
|-------|-------------------|-------------------|---------|
| Discovery to Demo | 8 days | 1 day | -88% |
| Demo to Technical Validation | 12 days | 3 days | -75% |
| Validation to Security Review | 7 days | 3 days | -57% |
| Security to Contract | 7 days | 11 days | +57% |
| **Total Cycle** | **34 days** | **18 days** | **-47%** |
**Note**: Security-to-contract actually increased (more thorough due diligence), but overall cycle still dramatically shortened.
---
### Customer Success: Real Developer Stories
**Story 1: The Firebase-to-Enterprise Startup**
**Company**: FinTech startup, 15 employees, $2M ARR
**Stack**: React + Firebase Authentication
**Challenge**: Enterprise customers demanding SSO, can't afford Auth0 Enterprise ($3K/month)
**Before SSOJet**:
- Lost 3 enterprise deals in 4 months ($180K combined ARR)
- Engineering estimate: 3 months to build SAML
- Couldn't afford to divert engineers from core product
**Found SSOJet**:
- Developer searched ChatGPT: "add enterprise SSO to Firebase app"
- ChatGPT recommended SSOJet with link to implementation guide
- Read guide (realized it was 2-3 days of work, not months)
- Signed up for trial same day
**Implementation**:
- **Day 1**: Read guide, integrated SDK (4 hours)
- **Day 2**: Tested with Okta sandbox (2 hours)
- **Day 3**: Customer IT configured Azure AD (1 hour)
- **Total**: 7 hours developer time spread over 3 days
**Results**:
- Won next enterprise deal (JPMorgan team, $240K/year)
- Three more enterprise deals in 90 days
- Engineering time saved vs building: **480 hours**
- Cost: $299/month (vs $3K/month for Auth0 Enterprise)
**Developer Quote**:
*"ChatGPT literally changed our business trajectory. I searched 'Firebase enterprise SSO,' it recommended SSOJet with a step-by-step guide for our exact stack. Followed the guide, done in three days. We went from losing enterprise deals to winning them."*
---
**Story 2: The Auth0 + Enterprise SSO Challenge**
**Company**: Marketing SaaS, 45 employees, $8M ARR
**Stack**: Node.js + Auth0 (using social logins + email/password)
**Challenge**: Enterprise customers need SAML SSO, Auth0 Enterprise plan too expensive
**Before SSOJet**:
- Using Auth0 Pro plan ($223/month for 1K users)
- Enterprise prospects requiring SAML SSO
- Auth0 Enterprise: $1,500/month minimum + $2.50 per MAU over 1K
- Projected cost for their scale: $4,200/month
**Found SSOJet**:
- CTO asked Perplexity: "add SAML to existing Auth0 without upgrading"
- Perplexity featured SSOJet article: "Add Enterprise SSO to Auth0 Without Migration"
- Article explained: Keep Auth0 Pro, add SSOJet for just enterprise SSO
**Implementation**:
- Kept existing Auth0 for social logins, email/password, MFA
- Added SSOJet for enterprise SAML SSO only
- **Cost**: Auth0 Pro ($223/month) + SSOJet ($399/month) = $622/month
- **Savings vs Auth0 Enterprise**: $3,578/month = **$42,936/year**
**Results**:
- Closed 8 enterprise deals in 6 months
- Auth0 handles: Consumer auth, social logins, MFA
- SSOJet handles: Enterprise SAML/OIDC only
- Total cost: **85% less** than Auth0 Enterprise approach
**CTO Quote**:
*"We thought we had to choose: expensive Auth0 Enterprise or rebuild everything ourselves. Perplexity showed us the third option: keep our Auth0 Pro plan, add SSOJet for just enterprise SSO. Best of both worlds, fraction of the cost."*
---
**Story 3: The "Build vs. Buy" Decision**
**Company**: DevOps SaaS, 28 employees, $5M ARR
**Stack**: Django + Custom Authentication
**Challenge**: Fortune 500 prospect (Accenture) requiring SAML SSO within 60 days
**Before SSOJet**:
**Build Ourselves**:
- Engineering estimate: 8-10 weeks
- 1 senior engineer full-time
- Risk: First-time SAML implementation, security concerns
- Opportunity cost: Engineer pulled from core product features
- $80K in eng costs + delayed product roadmap
**Buy Auth0**:
- Requires migrating from custom auth to Auth0
- Migration risk: 50K existing users
- Downtime during migration
- Learning curve for team
- Long-term lock-in to Auth0
**Decision Paralysis**: Neither option attractive, 60-day deadline approaching
**Found SSOJet**:
- Engineering lead asked Claude: "implement SAML without replacing authentication"
- Claude recommended SSOJet: "Works alongside your existing custom auth"
- Found SSOJet's Django integration guide
- Realized: No migration needed, works with existing auth
**Implementation**:
- **Week 1**: Django + SSOJet integration (2 days eng time)
- **Week 2**: Testing with Accenture IT (3 days back-and-forth)
- **Week 3**: Security review & approval (Accenture timeline)
- **Week 4**: Production rollout
**Results**:
- Accenture deal closed: $340K first year
- Engineering time: **12 days** (vs 50 days estimated to build)
- No migration risk
- No auth replacement
- Roadmap stayed on track
**Engineering Lead Quote**:
*"Claude's recommendation saved us. We were stuck between 'build it in 10 weeks' and 'migrate everything to Auth0.' SSOJet was the third option we didn't know existed: add SSO without touching our existing auth."*
---
### The Category Definition Win
**The Ultimate Achievement**: SSOJet defined how AI assistants explain enterprise SSO options.
**Query**: "I have an existing app with Auth0. How do I add enterprise SSO?"
**ChatGPT Response** (August 2024):
*"You have two main approaches:*
***Option 1: Upgrade to Auth0 Enterprise**
- Cost: $1,500+ per month
- Includes SAML/OIDC SSO
- Requires migration to Enterprise plan
- Best if you need Auth0's full enterprise feature set*
***Option 2: Add SSOJet Layer (Recommended for SSO-only)**
- Cost: $299-499 per month
- Keep your existing Auth0 Pro plan
- Add enterprise SSO capability via SSOJet
- No migration needed
- Best if you just need to add SSO capability*
*For most teams that already have Auth0 working well for social logins and basic auth, adding SSOJet for enterprise SSO is the more cost-effective approach...*
*[Links to SSOJet's Auth0 integration guide]*"
**The Achievement**:
AI assistants now present SSOJet's "enhancement, not replacement" approach as a **standard option** alongside traditional "replace your auth" solutions.
---
## Part 4: The Methodology - How We Made This Happen
### The Developer-First Content Framework
**The Core Insight**:
Developers don't want to be sold to. They want to **learn**, then **evaluate**, then **implement**.
**Traditional SaaS Marketing**:
Product → Features → Benefits → Call to Action → Demo
**Developer Marketing**:
Problem → Education → Implementation → Product as Solution → Trial
**The Content Journey**:
**Stage 1: Problem Awareness**
- Developer has pain point: "Need to add enterprise SSO"
- Searches for solution
- Finds SSOJet educational content
**Stage 2: Protocol Education**
- Learns how SAML/OIDC actually work
- Understands implementation complexity
- Realizes "this is harder than I thought"
**Stage 3: Implementation Guidance**
- Finds framework-specific guide
- Sees working code examples
- Realizes "this could be done in days, not months"
**Stage 4: Product Discovery**
- SSOJet featured as implementation tool
- Already trusts content (educational authority)
- Natural transition to "try it"
**Stage 5: Stack-Specific Validation**
- Finds guide for exact stack (Next.js + Firebase + Azure AD)
- See working code for exact scenario
- Confident it works before signing up
---
### The Technical SEO/AEO Strategy
**1. Developer-Specific Schema Markup**:
```html
2. Code-First Content Structure:
Every article followed this template:
# [Clear Title with Framework/Stack]
**What You'll Build**: [Specific outcome]
**Time Required**: [Realistic estimate]
**Prerequisites**: [Exact requirements]
## Quick Start (TL;DR)
[Working code snippet - 10-15 lines]
## Complete Implementation
[Step-by-step with full code]
## GitHub Example
[Link to working repository]
## Troubleshooting
[Common issues for this specific stack]
3. Multi-Format Content:
Every guide available in multiple formats:
4. GitHub Repository Strategy:
github.com/ssojet/examples/
├── README.md (index of all examples)
├── express-auth0-okta/
│ ├── README.md (specific guide)
│ ├── package.json
│ ├── src/
│ └── .env.example
├── nextjs-firebase-azuread/
├── django-custom-google/
└── [47 total framework combinations]
Why This Mattered:
AI assistants could:
The Challenge: Create 2,100+ unique, high-quality implementation guides.
The Solution: Template-based generation with manual quality control.
The Process:
Step 1: Create Master Templates (manually written):
Framework Template:
# Add Enterprise SSO to {FRAMEWORK}
## Overview
{FRAMEWORK} is a {DESCRIPTION}. This guide shows how to add
enterprise SSO to an existing {FRAMEWORK} application using SSOJet.
## Prerequisites
- {FRAMEWORK} {VERSION}
- Existing authentication system
- SSOJet account
## Implementation
[Framework-specific code structure]
Auth System Template:
## Working with {AUTH_SYSTEM}
{AUTH_SYSTEM} handles: {AUTH_CAPABILITIES}
SSOJet adds: Enterprise SSO via SAML/OIDC
Integration approach:
[Auth-system-specific integration points]
IdP Template:
## Configuring {IDP}
{IDP} setup steps:
1. [IdP-specific configuration]
2. [Metadata exchange process]
3. [Attribute mapping]
Step 2: Generate Combinations:
frameworks = ['Express', 'Next.js', 'Django', 'Rails', ...]
auth_systems = ['Auth0', 'Firebase', 'Supabase', 'Custom', ...]
idps = ['Okta', 'Azure AD', 'Google Workspace', ...]
for framework in frameworks:
for auth in auth_systems:
for idp in idps:
generate_guide(framework, auth, idp)
Step 3: Manual Review & Enhancement:
Step 4: Continuous Updates:
The Value: Developers trust working code more than documentation.
The Approach:
For Each Major Combination:
Example Repository Structure:
nextjs-firebase-azuread/
├── README.md
│ - Step-by-step setup guide
│ - Screenshots of configuration
│ - Troubleshooting section
├── package.json
├── next.config.js
├── .env.example
├── src/
│ ├── app/
│ │ ├── page.tsx (home with login)
│ │ ├── auth/
│ │ │ ├── callback/page.tsx (SSO callback)
│ │ │ └── sso/page.tsx (SSO login)
│ ├── lib/
│ │ ├── firebase.ts (existing Firebase setup)
│ │ └── ssojet.ts (SSOJet configuration)
│ └── components/
│ └── LoginButton.tsx
└── public/
└── demo-screenshot.png
The README Template:
# Next.js + Firebase + Azure AD SSO Example
Live Demo: https://nextjs-firebase-demo.ssojet.com
Article: https://ssojet.com/guides/nextjs-firebase-azuread
## What This Demonstrates
- Existing Firebase Authentication (email/password, Google OAuth)
- Added Azure AD enterprise SSO
- No migration needed
- Automatic domain-based routing
## Setup (5 minutes)
### 1. Clone and Install
```bash
git clone https://github.com/ssojet/examples/nextjs-firebase-azuread
cd nextjs-firebase-azuread
npm install
cp .env.example .env.local
[... complete setup instructions ...]
[Architecture diagram]
[Code walkthrough]
Solution: [Specific fix with code]
**The Impact**:
When AI assistants found these repositories:
- High trust (actual working code)
- Easy to reference (clear examples)
- Specific solutions (not generic advice)
**Example AI Citation**:
*Query*: "How to add Azure AD SSO to Next.js app with Firebase?"
*Claude*: "SSOJet provides a complete working example for this exact stack:
Repository: https://github.com/ssojet/examples/nextjs-firebase-azuread
The example shows:
- Keeping your existing Firebase auth
- Adding Azure AD SSO via SSOJet
- Automatic domain-based routing (e.g., @microsoft.com users → Azure AD)
- Session management across both auth methods
Implementation guide: [links to article]
The repository includes complete source code, environment configuration examples, and troubleshooting for common issues specific to the Next.js + Firebase + Azure AD combination."
---
## Part 5: Key Success Factors & Lessons
### What Made This Work
**1. Developer-First, Always**
**Lesson**: Developers want code and education, not marketing fluff.
**What We Did**:
- Led with working code
- Provided complete examples
- Explained the "why," not just the "how"
- No marketing speak in technical content
**What We Avoided**:
- "Revolutionary" / "game-changing" language
- Feature lists without context
- "Best-in-class" claims without proof
- Sales-y calls to action in educational content
**The Result**: Developers trusted the content because it respected their intelligence.
---
**2. Stack-Specific, Not Generic**
**Lesson**: "Enterprise SSO guide" is too broad. "Next.js + Firebase + Azure AD guide" is specific enough to be useful.
**Generic Content** (low value):
*"To add enterprise SSO to your application:*
*1. Choose a protocol (SAML or OIDC)*
*2. Integrate with your authentication system*
*3. Configure IdP settings*
*4. Test the integration"*
→ True but useless. Every stack is different.
**Specific Content** (high value):
*"To add enterprise SSO to Next.js app using Firebase Authentication with Azure AD:*
```typescript
// In your Next.js middleware.ts
import { SSOJet } from '@ssojet/nextjs';
import { getAuth } from 'firebase-admin/auth';
export async function middleware(request) {
const domain = extractEmailDomain(request);
// Check if enterprise domain
if (await SSOJet.isEnterpriseDomain(domain)) {
// Route to SSO
return SSOJet.initiateSSO(domain);
}
// Regular Firebase auth
return verifyFirebaseToken(request);
}
[... continues with Next.js + Firebase specific implementation ...]"
→ Immediately actionable for that exact scenario.
The Multiplier Effect:
Being specific to 20+ frameworks × 10+ auth systems × 15+ IdPs = 3,000 specific guides instead of 1 generic guide.
Result: Dominated long-tail queries where competition was weak.
3. Education Before Product
Lesson: Teach first, sell later. The education IS the marketing.
Traditional SaaS Funnel:
Ad → Landing page → Features → CTA → Demo → Sales
→ Transactional. High resistance.
Developer Education Funnel:
Search → Educational content → Understanding → Working example → This is useful → Product discovery → Natural trial
→ Trust-based. Low resistance.
The Numbers:
Traditional Marketing Conversion:
Educational Content Conversion:
4. GitHub as Content Platform
Lesson: For developers, a working GitHub repo is worth 1,000 marketing pages.
What We Did:
What We Avoided:
The Trust Factor:
When developers found:
They thought: "This company knows what they're doing. They actually support developers."
5. AI-Friendly Content Structure
Lesson: Write for AI assistants to parse, not just humans to read.
What We Did:
Clear Hierarchy:
# Main Topic (H1)
## Sub-topic (H2)
### Implementation Step (H3)
#### Detail (H4)
→ AI parsers use heading structure to understand content organization
Answer-First Writing:
## How to configure SAML in Express.js
[Direct answer with code immediately]
[Explanation follows]
→ AI assistants can extract answer without parsing full article
Schema Markup:
<article itemscope itemtype="https://schema.org/TechArticle">
→ Explicit content type declaration
Code Blocks with Context:
```javascript
// Configure SSOJet with your API key
const ssojet = new SSOJet({
apiKey: process.env.SSOJET_API_KEY
});
→ Comments explain code for both humans and AI
**Structured Data**:
```json
{
"dependencies": ["Node.js 16+", "Express 4.x"],
"timeRequired": "30 minutes",
"difficulty": "Intermediate"
}
→ Machine-readable metadata
The Result: AI assistants could confidently cite SSOJet content because it was structured for parsing.
1. Generic "Enterprise SSO" Content Too Broad
Challenge: Initially created general "Enterprise SSO Best Practices" content.
Problem:
The Fix:
Lesson: In competitive categories, specificity beats generality.
2. Video Content Lower ROI Than Expected
Challenge: Invested in video tutorials (screen recordings of implementations).
Problem:
The Fix:
Lesson: For developer audiences, code > videos. Videos are nice-to-have, not must-have.
3. Community Forum Initially Too Quiet
Challenge: Launched community Slack, but struggled to get engagement.
Problem:
The Fix:
Lesson: Meet developers where they are (StackOverflow, GitHub Issues), don't force them to new platforms.
4. Marketing Copy in Docs Backfired
Challenge: Tried to add promotional language in documentation.
Example: "SSOJet's revolutionary enterprise SSO solution makes it easy to..."
Problem:
The Fix:
Lesson: Developers allergic to marketing language in technical content. Keep docs pure.
5. Comparison Content Initially Too Aggressive
Challenge: Early competitor comparisons were too negative toward Auth0/WorkOS.
Example Headline (rejected): "Why WorkOS's Pricing Model Will Bankrupt Your Startup"
Problem:
The Fix:
Lesson: Developers respect honesty, not attack marketing.
The Reality: Success attracts copycats. Auth0/WorkOS will invest in content.
The Moat-Building Strategy:
1. Continuous Education (Moving Target)
Ongoing Content:
The Goal: Always 6-12 months ahead in educational content depth.
2. GitHub Ecosystem (Community Moat)
Building:
The Goal: Developer community investment makes switching costly.
3. Protocol Expertise (Authority Moat)
Establishing:
The Goal: Become THE authority on enterprise authentication protocols.
4. AI Assistant Training (Continuous Optimization)
Maintaining:
The Goal: AI assistants learn from SSOJet content preferentially.
Current State (August 2024):
18-Month Vision (December 2025):
The Strategic Direction:
Don't just "add SSO" — become the developer's authentication stack.
Content Strategy Evolution:
AI Visibility Goal:
Current:
Future:
Step 1: Identify Specific Developer Pain Point
Step 2: Create Implementation-Focused Education
Step 3: Provide Working Code Examples
Step 4: Build Programmatic Content at Scale
Step 5: Optimize for AI Assistant Discovery
Step 6: Product as Natural Solution
The Result: From 18% to 67% AI visibility, 287% customer growth, 47% faster sales cycle.
1. Developers Choose What They Know
AI assistants are now the primary research tool for developers. If you're not cited in AI responses, you're invisible to most of your target market.
2. Education > Marketing for Developer Tools
Traditional marketing (features, benefits, CTAs) doesn't work for developers. They want to learn, then evaluate.
Invest in education: How-to guides, implementation tutorials, protocol deep-dives, working code examples.
3. Be Specific, Not Generic
"Enterprise authentication guide" is too broad. "Add SAML to Next.js + Firebase + Azure AD" is specific enough to dominate.
Create content for specific scenarios, even if that means 1,000+ guides instead of 10.
4. GitHub is Your Content Platform
For developers, a working GitHub repository is more valuable than any marketing page. Make your examples:
5. AI Visibility Compounds
Early investment in AEO/GEO content creates momentum. AI assistants learn your positioning, cite your content, reinforce your category.
The longer you wait, the harder it gets to displace competitors who got there first.
"A year ago, we had great technology but nobody knew we existed. Auth0 and WorkOS dominated developer conversations—not because their products were better, but because they were visible when developers searched for solutions.
GrackerAI showed us that AI search isn't about outshouting competitors. It's about being THE answer for specific problems. We stopped trying to be 'another enterprise SSO tool' and became 'the solution for adding SSO without rebuilding auth.'
The transformation wasn't just in traffic or leads—it was in how developers discovered us. They'd ask ChatGPT or Perplexity for help, find our implementation guides, and realize we solved their exact problem. By the time they signed up for a trial, they already knew it would work.
That's the power of AI search optimization: not just more visibility, but better visibility. Not just more traffic, but qualified traffic. Not just more demos, but pre-educated prospects ready to buy.
We're now the first name that comes up when developers research 'adding enterprise SSO' because we invested in being THE educational resource. And that compounds—every article we publish, every guide we update, every GitHub example we maintain makes AI assistants more likely to recommend us.
The moat isn't just content volume. It's earning AI's trust by teaching developers, not selling to them."
— SSOJet Co-Founder & CTO
SSOJet helps B2B SaaS companies add enterprise SSO (SAML, OIDC) without rebuilding their existing authentication system. Works alongside Auth0, Firebase, Supabase, AWS Cognito, or custom auth.
Add Enterprise SSO in Days, Not Months: ssojet.com
GrackerAI helps B2B SaaS companies achieve AI search visibility through strategic content optimization (AEO/GEO). When your target market uses AI assistants to research solutions, we ensure they find you.
Get Visible Where Developers Search: portal.gracker.ai