What are the Current Best Practices for Cybersecurity Marketing?
In today's rapidly evolving digital ecosystem, cybersecurity has become more than just a technical necessity—it's a critical business strategy that demands sophisticated marketing approaches. Cybersecurity marketing is not simply about selling products or services; it's about educating, empowering, and protecting organizations from increasingly complex digital threats. This comprehensive guide will explore the intricacies of cybersecurity marketing and outline the most effective best practices to help businesses communicate their value proposition and build trust in an increasingly vulnerable digital world.
What is Cybersecurity?
Cybersecurity is a holistic approach to protecting digital systems, networks, and data from malicious attacks, unauthorized access, and potential breaches. It encompasses a wide range of technologies, processes, and practices designed to safeguard digital infrastructure, sensitive information, and organizational assets from cyber threats such as malware, ransomware, phishing attacks, and other sophisticated digital risks.
Why is Cybersecurity Important?
The digital landscape is fraught with potential risks that can devastate businesses and organizations. Cybersecurity has become paramount due to:
Increasing frequency and sophistication of cyber attacks
Potential financial losses from data breaches
Regulatory compliance requirements
Protection of sensitive customer and corporate data
Maintaining organizational reputation and trust
What Does Cybersecurity Best Practices Mean? Strategies to Know
Cybersecurity best practices are a set of strategic and tactical approaches that organizations implement to minimize digital risks and protect their technological assets. These practices go beyond simple technical solutions and require a comprehensive, proactive approach to digital security.
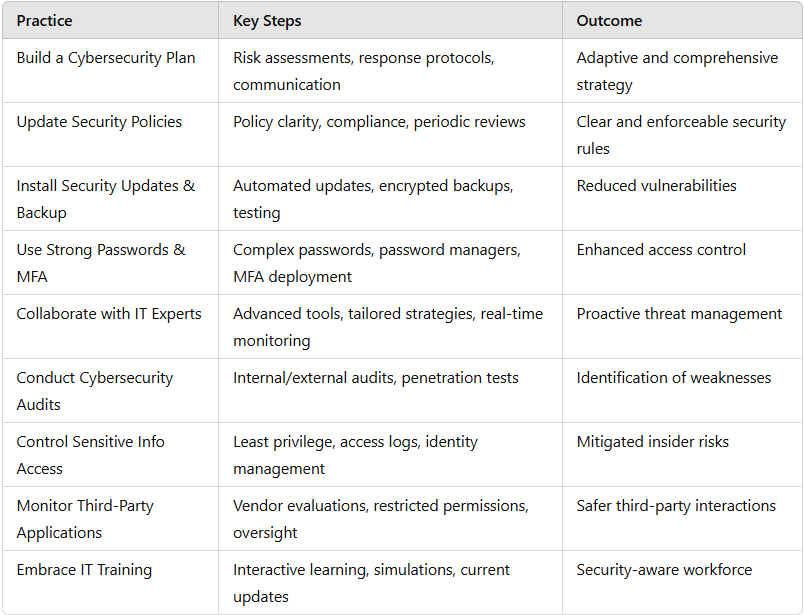
1. Build a Strong Cybersecurity Plan
A well-structured cybersecurity plan is the cornerstone of any organization's digital defense. The process includes:
Risk Assessment: Identify critical assets, assess vulnerabilities, and evaluate the potential impact of risks.
Incident Response Protocols: Develop a step-by-step response guide for mitigating security incidents.
Communication Plans: Establish clear communication channels for reporting and managing incidents.
Continuous Improvement: Regularly update strategies to address evolving threats.
By treating this plan as a living document, organizations can adapt to new challenges and maintain resilience.
2. Update and Enforce Security Policies
Security policies provide the framework for an organization's defense mechanisms. Essential actions include:
Policy Clarity: Define acceptable use of devices, data, and systems.
Violation Consequences: Clearly outline repercussions for non-compliance.
Regulatory Compliance: Align policies with industry standards, such as GDPR or ISO 27001.
Periodic Reviews: Regularly audit and revise policies to stay ahead of threats.
Well-enforced policies empower employees to contribute to a secure environment.
3. Install Security Updates and Backup Data
Keeping systems updated and securing data backups are crucial for mitigating cyber risks:
Automated Updates: Implement systems that automatically install patches and updates.
Redundant Backups: Create multiple encrypted backups, stored both onsite and offsite.
Testing: Periodically test backup and recovery processes to ensure functionality.
Proactive updates and reliable backups provide a safety net against unexpected threats.
4. Use Strong Passwords and Multi-Factor Authentication (MFA)
Passwords and MFA are frontline defenses against unauthorized access:
Strong Password Policies: Require a mix of characters, numbers, and symbols.
Password Management: Promote the use of secure password managers.
MFA Deployment: Implement MFA for all sensitive accounts and systems.
Regular Updates: Rotate passwords and keys periodically.
These measures significantly reduce the risk of compromised credentials.
5. Collaborate with IT Experts to Prevent Attacks
Working with cybersecurity professionals enhances threat detection and response:
Advanced Tools: Leverage expert knowledge of detection and mitigation tools.
Customized Strategies: Tailor security measures to specific organizational needs.
Real-Time Monitoring: Ensure constant monitoring to detect anomalies promptly.
Collaboration with experts ensures a proactive approach to emerging risks.
6. Conduct Regular Cybersecurity Audits
Audits are essential for identifying and fixing security gaps:
Internal Audits: Regularly review internal processes and defenses.
External Assessments: Hire third-party auditors for unbiased evaluations.
Penetration Testing: Simulate attacks to evaluate system robustness.
Documentation: Maintain detailed reports of findings and actions taken.
Frequent audits help maintain a resilient cybersecurity posture.
7. Control Access to Sensitive Information
Restricting access minimizes the risk of insider threats:
Least Privilege Principle: Limit user permissions to only what is necessary.
Access Logs: Track and review user activity on critical systems.
Identity Management: Use identity verification tools to ensure only authorized access.
Controlled access enhances security while maintaining efficiency.
8. Monitor Third-Party Users and Applications
Third-party integrations can introduce vulnerabilities if not properly managed:
Vendor Assessments: Evaluate third-party security measures before collaboration.
Access Control: Limit and monitor third-party permissions.
Regular Monitoring: Continuously oversee third-party activities to detect risks.
Strong third-party policies safeguard against indirect threats.
9. Embrace IT Training and Education
Educating employees is crucial in building a security-conscious culture:
Interactive Training: Use engaging methods to teach security best practices.
Phishing Simulations: Test and improve employee awareness of common threats.
Updated Modules: Keep training content current with emerging trends.
An informed workforce is one of the strongest defenses against cyberattacks.
Summary Table of Practices
Learn More About Cybersecurity with GrackerAI
Navigating the complex world of cybersecurity requires continuous learning and adaptation. GrackerAI offers cutting-edge solutions and insights to help organizations stay ahead of emerging digital threats.
External Resources
For more in-depth information on cybersecurity best practices, we recommend exploring:
Conclusion
Cybersecurity marketing is about more than selling products—it's about building trust, demonstrating expertise, and helping organizations protect their most valuable digital assets. By implementing these best practices, businesses can create a comprehensive, proactive approach to digital security that resonates with potential clients and stakeholders. Stay informed, stay prepared, and stay secure.