Starting in December 2024, Microsoft Threat Intelligence identified a phishing campaign that impersonates the online travel agency Booking.com. This campaign targets organizations in the hospitality sector, employing a social engineering technique known as ClickFix to deliver credential-stealing malware. As of February 2025, this campaign remains active. The phishing attack specifically targets individuals in hospitality organizations across North America, Oceania, and Europe. Attackers send fake emails that appear to come from Booking.com, prompting users to address negative guest reviews or verify accounts. 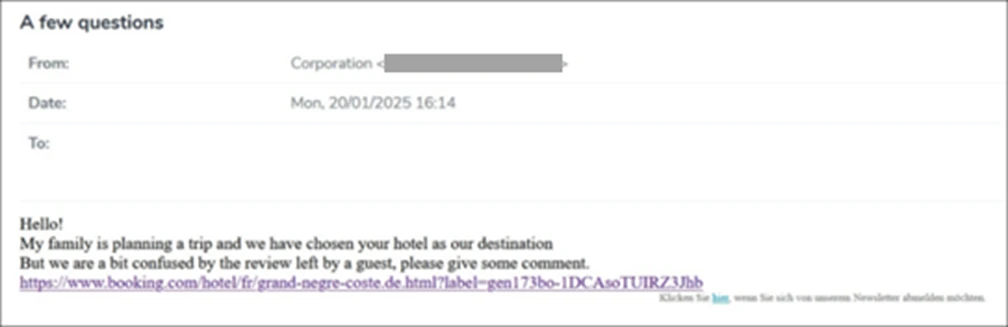
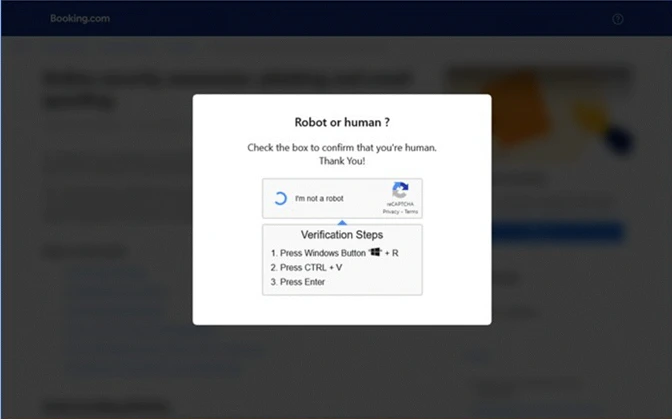 Image courtesy of Microsoft Security Blog The malicious code, executed via mshta.exe, downloads a variety of malware, including XWorm, Lumma stealer, and AsyncRAT, all capable of stealing financial data and credentials.
Image courtesy of Microsoft Security Blog The malicious code, executed via mshta.exe, downloads a variety of malware, including XWorm, Lumma stealer, and AsyncRAT, all capable of stealing financial data and credentials.
Recommendations for Defense
Organizations can mitigate the impact of phishing campaigns by educating users to recognize these threats:
- Verify the sender’s email address.
- Contact the service provider directly for suspicious messages.
- Be cautious of urgent calls to action.
- Hover over links to check the full URL.
- Look for typos in the email content, which can be indicators of phishing.
For enhanced security, Microsoft recommends implementing phishing-resistant authentication methods and enforcing multi-factor authentication (MFA) across all accounts.
Malware Types Involved
The phishing campaign delivers various malware families:
- XWorm: A remote access trojan that allows the attacker to take control of the victim's device.
- Lumma Stealer: Focused on stealing sensitive information.
- AsyncRAT: A remote access trojan known for its ability to capture keystrokes and access files.
Microsoft Defender Antivirus detects these threats as follows:
ClickFix Technique Explained
The ClickFix technique is a sophisticated method used in this phishing campaign. Users are misled into executing malicious commands by following instructions embedded in fake CAPTCHA pages. 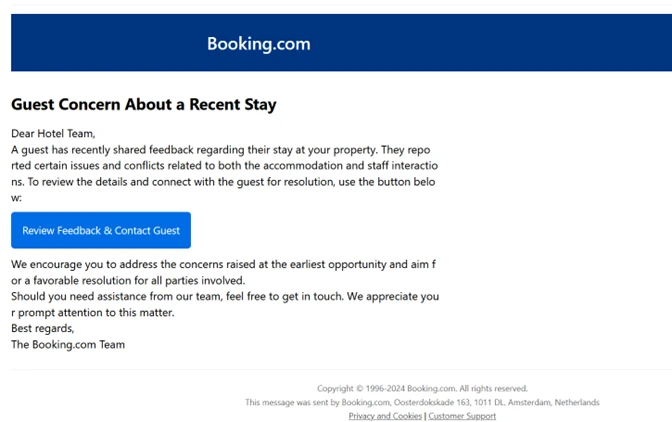
Implications for Cybersecurity Marketing
For companies in the cybersecurity sector, such as GrackerAI, there is a significant opportunity to address these emerging threats through targeted content marketing and threat monitoring. By leveraging insights from such phishing campaigns, GrackerAI can help organizations create relevant marketing materials and educate their audiences on the latest cybersecurity threats. GrackerAI is an AI-powered cybersecurity marketing platform designed to assist organizations in transforming security news into strategic content opportunities. It enables marketing teams to identify emerging trends, monitor threats, and produce technically relevant content that resonates with cybersecurity professionals. Explore our services at GrackerAI to enhance your cybersecurity marketing strategy.
Latest Cybersecurity Trends & Breaking News
Critical Vulnerability in Erlang/OTP SSH Implementation Automating Cybersecurity in Software Development with AI





