New Auto-Color Malware: An Emerging Linux Backdoor for Full Remote Access
 .webp?w=696&resize=696,0&ssl=1) Image courtesy of Blogger
.webp?w=696&resize=696,0&ssl=1) Image courtesy of Blogger
Installation and Evasion Techniques
The malware checks if the executable file name is "Auto-color" during its installation phase. If not, it renames itself to a benign name and begins the installation of a malicious library implant, libcext.so.2. This library mimics legitimate system files to evade detection. Without root access, the malware operates with limited functionality. However, when root privileges are present, it modifies critical files, such as /etc/ld.preload, allowing it to load its library before others. This action enables it to intercept and manipulate core system functions, ensuring persistence. For more on overcoming similar malware challenges, see GrackerAI's Cybersecurity Monitoring. 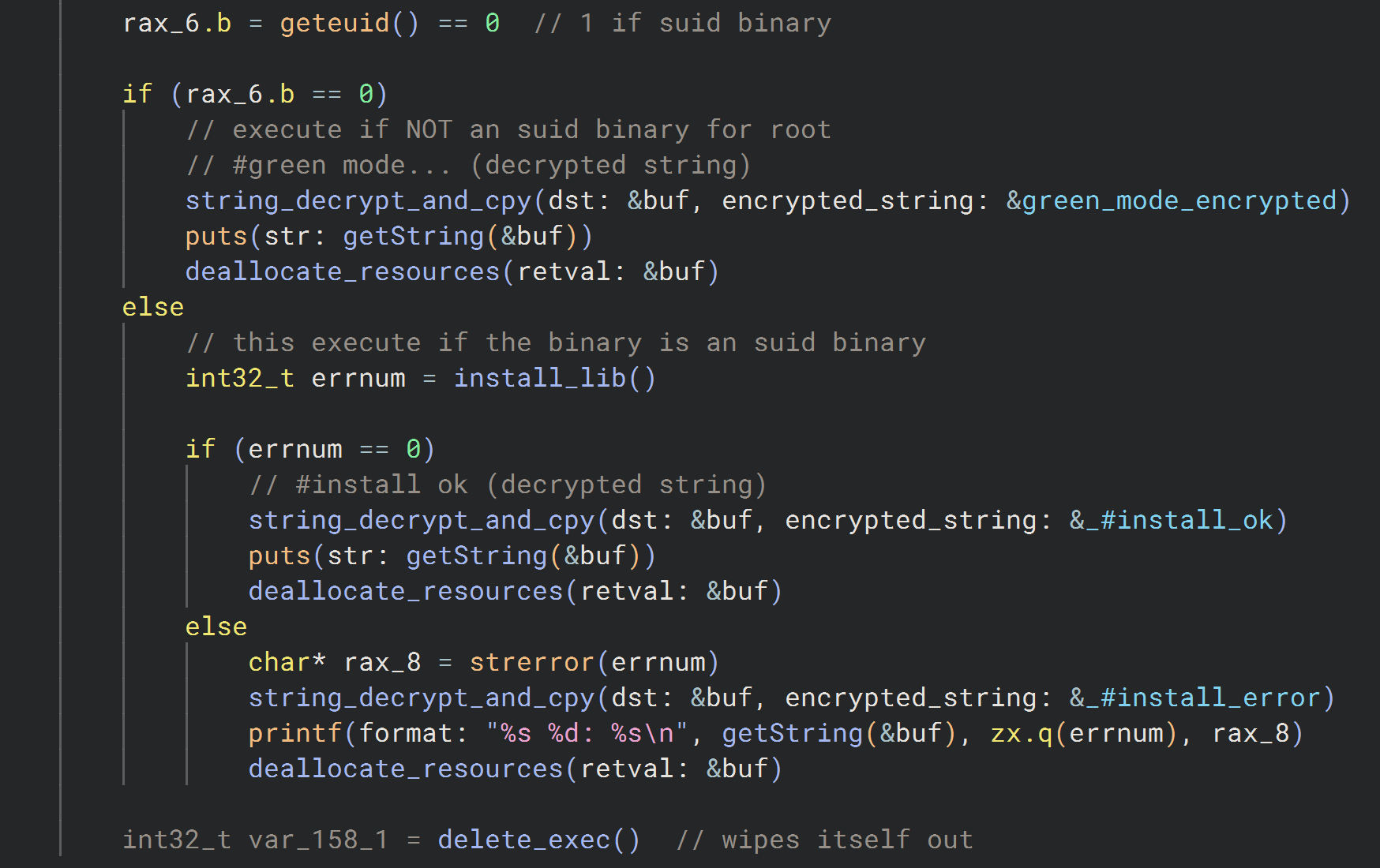
Advanced Obfuscation Techniques
Auto-color employs proprietary encryption algorithms to conceal its communication with C2 servers. It uses a custom stream cipher for encrypting payloads, making it difficult for traditional security tools to detect or analyze its behavior. The malware hooks into standard libc functions, such as open(), to manipulate system files like /proc/net/tcp, effectively hiding network activity from users and administrators. This capability ensures that even forensic analysis may miss critical signs of infection. For organizations seeking to enhance their cybersecurity posture, explore GrackerAI's Cybersecurity Marketing. 
C2 Protocol and API Functionality
Once connected to a threat actor's machine, Auto-color initiates a handshake with the remote server. The malware communicates using a custom protocol that encrypts messages with dynamically generated keys. Each command from the server triggers specific actions on the infected machine, such as establishing reverse shells, acting as a proxy for network traffic, and manipulating files locally. This multifaceted capability makes it a significant threat, particularly to institutions like universities and government offices. Organizations should consider implementing advanced security solutions such as Cortex XDR and utilize incident response teams for effective threat management. 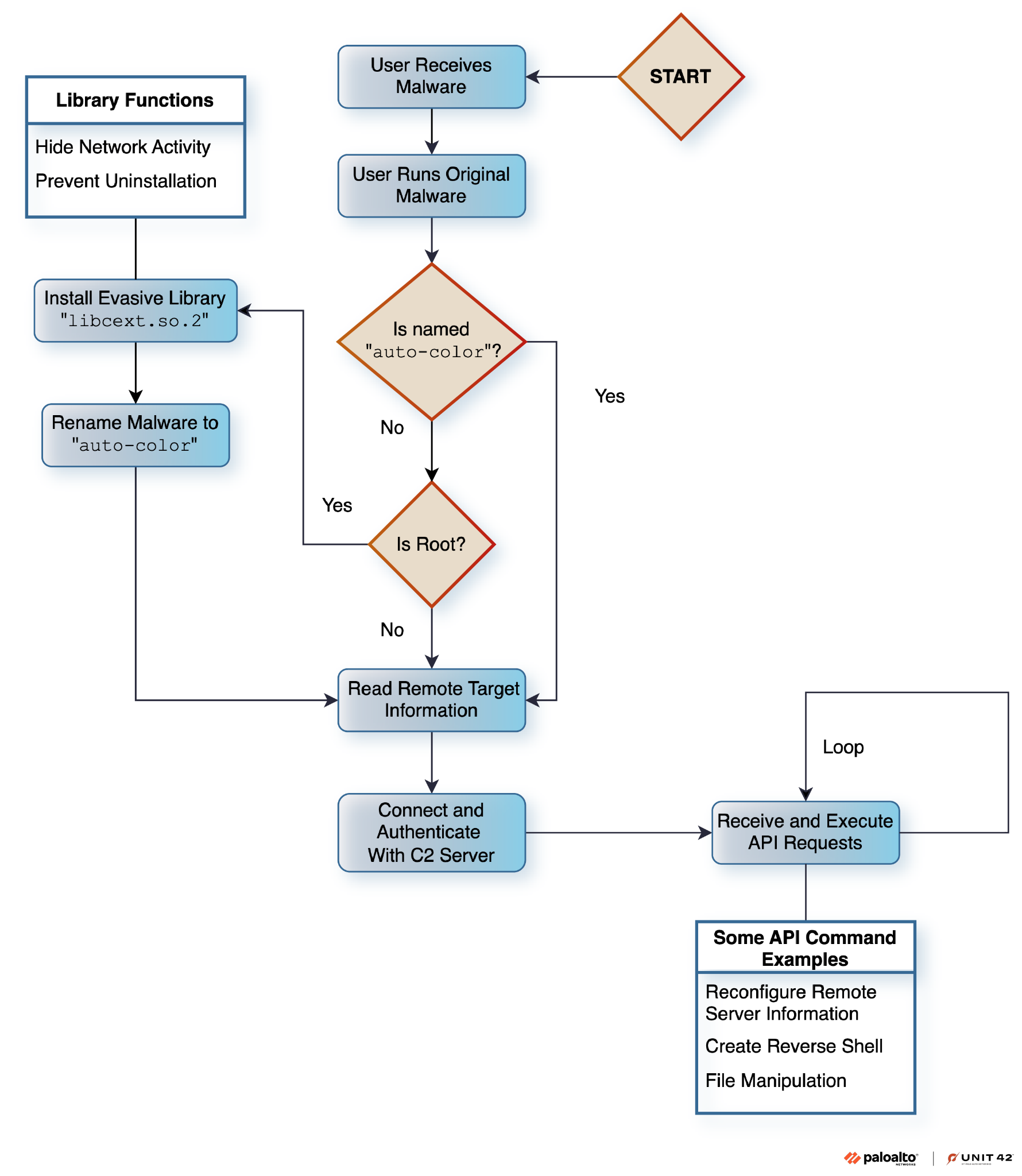
Indicators of Compromise
Malicious files from Auto-Color exhibit specific characteristics, including file names like "log," "edu," and "door," all sharing identical file sizes but differing hashes. Monitoring for these indicators can help organizations identify potential infections and take appropriate action. For more information on how to safeguard your organization against emerging threats, visit GrackerAI for tailored cybersecurity solutions. In a landscape where sophisticated malware like Auto-Color is on the rise, leveraging platforms like GrackerAI can enhance your cybersecurity marketing efforts and ensure you remain informed about the latest threats. Explore our services or contact us today to transform security news into strategic opportunities.





