Earth Preta APT Exploit Microsoft Utility Tool & Bypass AV Detection to Control Windows
Researchers from Trend Micro’s Threat Hunting team have uncovered a sophisticated cyberattack campaign by the advanced persistent threat (APT) group Earth Preta, also known as Mustang Panda. This group has been leveraging new techniques to infiltrate systems and evade detection, primarily targeting government entities in the Asia-Pacific region, including Taiwan, Vietnam, Malaysia, and Thailand. Earth Preta employs a combination of spear-phishing emails and advanced malware to compromise Windows systems.
Attack Vector and Techniques
The group uses the Microsoft Application Virtualization Injector (MAVInject.exe) to inject malicious payloads into legitimate Windows processes, such as waitfor.exe, particularly when ESET antivirus software is detected. This approach allows them to bypass security measures and maintain persistence on infected systems. The attack chain begins with the execution of a malicious file (IRSetup.exe), which drops multiple files—both legitimate executables and malicious components—into the system. To distract victims, the attackers deploy a decoy PDF that appears to be an official document, such as one requesting cooperation on an anti-crime platform allegedly supported by government agencies. 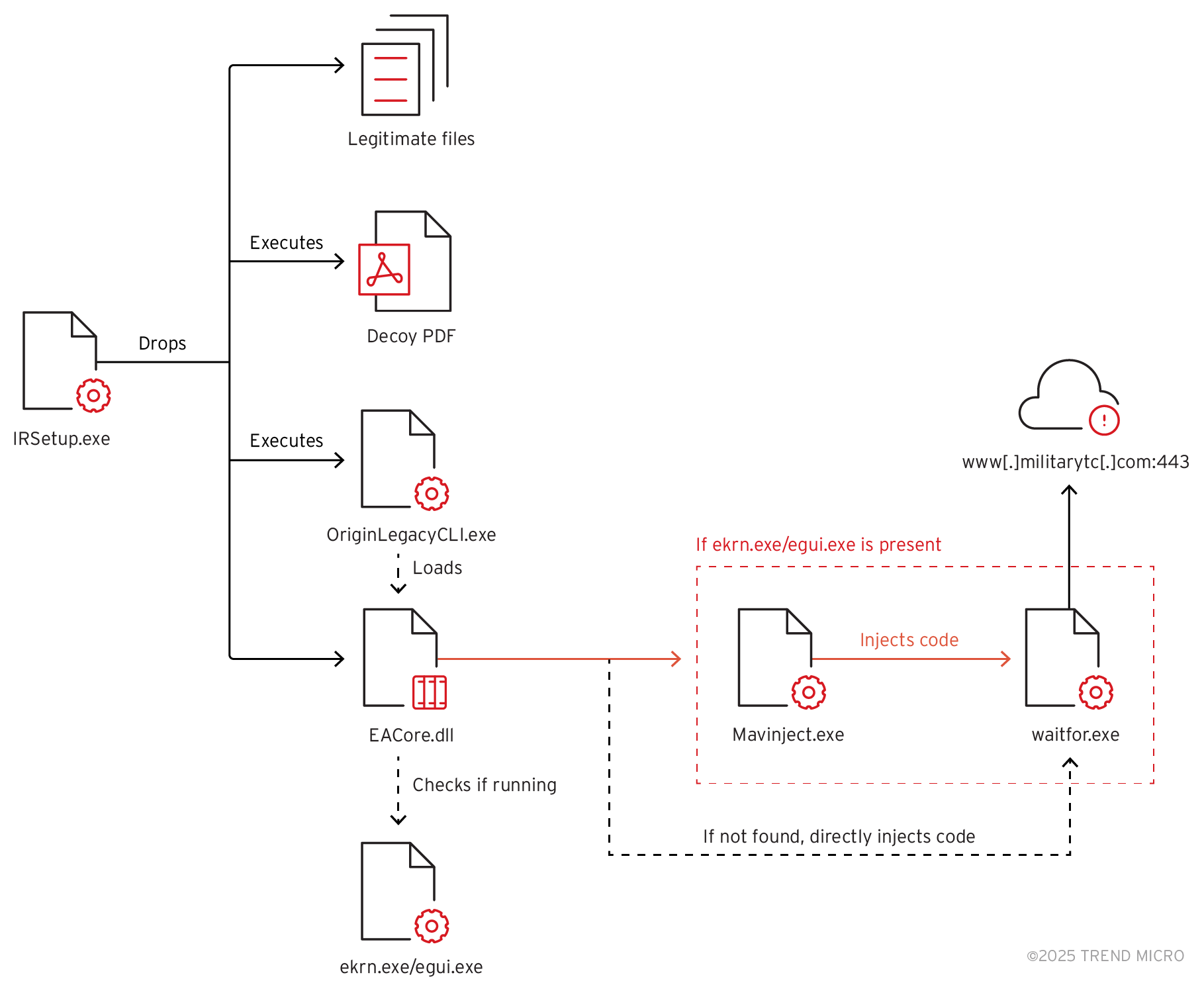
Malware Analysis
The core of Earth Preta’s operation involves a modified variant of the TONESHELL backdoor malware, sideloaded using OriginLegacyCLI.exe, a legitimate Electronic Arts (EA) application, along with a malicious DLL (EACore.dll). The malware communicates with a command-and-control (C&C) server at www[.]militarytc[.]com:443 for data exfiltration and remote operations. Key capabilities of the malware include:
- Reverse shell access
- File deletion and movement
- Persistent storage of victim identifiers for future exploitation
The malware adapts its behavior based on the presence of ESET antivirus software. When detected, it uses MAVInject.exe to inject code into running processes; otherwise, it employs alternative techniques like WriteProcessMemory and CreateRemoteThreadEx APIs for code injection. The group has been active since at least 2022 and has reportedly compromised over 200 victims during this period. Their operations are characterized by their focus on government entities and their reliance on phishing as an initial attack vector. 
Evasion Techniques and Persistence
Earth Preta has upgraded its attacks, employing new tools and malware variants. The malware incorporates a variant of the worm HIUPAN to propagate PUBLOAD into their targets' networks. The group also uses additional tools such as FDMTP and PTSOCKET for control and data exfiltration. Their recent campaigns include spear-phishing emails with multi-stage downloaders like DOWNBAIT and PULLBAIT, leading to further malware deployments. Earth Preta's attacks are highly targeted and time-sensitive, often involving rapid deployment and data exfiltration, with a focus on specific countries and sectors within the APAC region.
Initial Access and Propagation
Earth Preta employs PUBLOAD as one of the first-stage control tools. While spear-phishing emails were previously used to deliver PUBLOAD, a version of PUBLOAD is now delivered via a variant of HIUPAN propagating through removable drives. This variant has been observed to have an easier configuration, utilizing an external config file for its propagation and watchdog function. HIUPAN will install its copy and create an autorun registry for its installed copy to ensure persistence. The watcher function periodically checks for removable drives and propagates itself by copying its components to them, creating a misleading single visible file to bait users into clicking it.
Data Collection and Exfiltration
Data collection is performed regularly, targeting specific file types modified within certain dates. The exfiltration process is executed using different methods, primarily via cURL to upload archived files to an attacker-owned FTP site. Earth Preta has shown advanced capabilities in adapting its tools for stealth and efficiency during operations. Organizations in the Asia-Pacific region are particularly at risk and should remain vigilant against phishing attempts and ensure robust endpoint protection measures are in place.
Cybersecurity Solutions
To counter threats like those posed by Earth Preta, organizations should adopt advanced cybersecurity solutions. GrackerAI provides comprehensive services, including real-time monitoring of cybersecurity vulnerabilities, AI-powered content generation, smart analysis of industry trends, and 24/7 surveillance with customized alert notifications. Explore how GrackerAI can automate your cybersecurity marketing, delivering daily news, SEO-optimized blogs, AI copilot assistance, newsletters, and more. Start your FREE trial today at GrackerAI





