The DollyWay malware operation has been active since 2016, compromising over 20,000 WordPress sites worldwide. It primarily targets vulnerable sites through n-day exploits in plugins and themes. GoDaddy researchers have linked this operation to a sophisticated threat actor that uses a well-organized infrastructure and advanced evasion techniques DollyWay World Domination.
Campaign Mechanics
DollyWay redirects site visitors to fake dating, gambling, and crypto sites, generating approximately 10 million fraudulent impressions each month. The malware's monetization strategy involves utilizing affiliate networks like VexTrio and LosPollos, which filter and redirect users based on their location and device type. 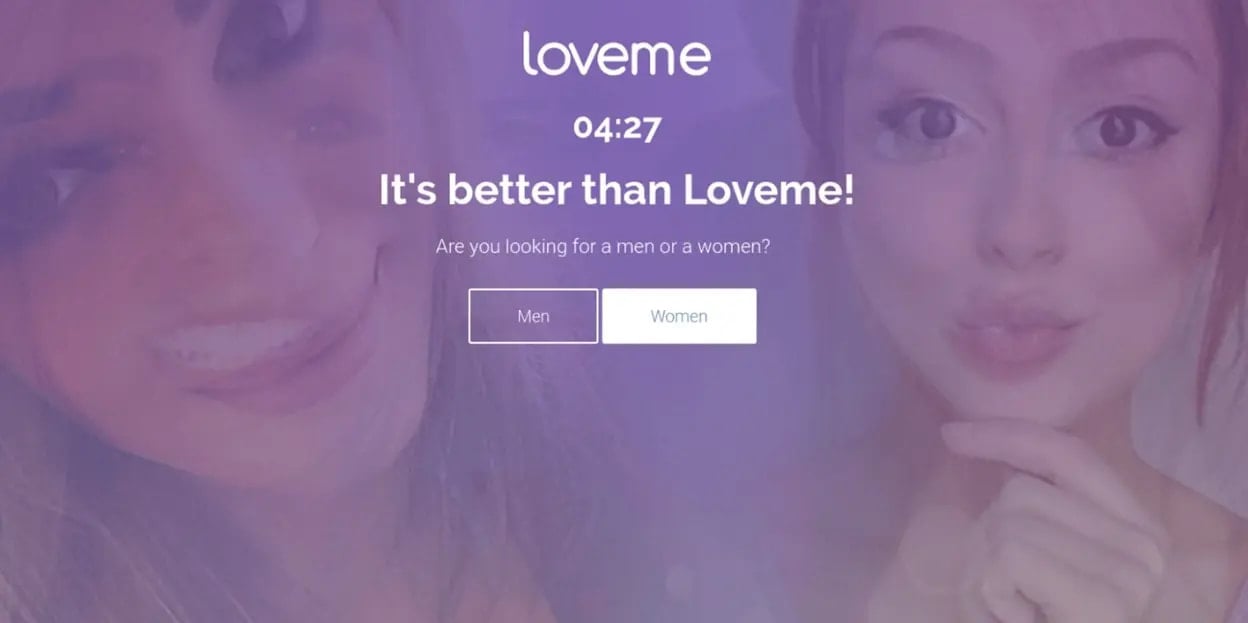
wp_enqueue_script function, loading a second script that collects visitor data and determines the appropriate redirection.
Reinfection and Persistence
DollyWay is known for its persistence; it automatically reinfects compromised sites with every page load. The malware spreads its code across all active plugins and installs the WPCode plugin, which contains obfuscated malware snippets. This makes disinfection particularly challenging since the WPCode plugin is hidden from the WordPress dashboard. In addition to hiding its presence, the malware creates malicious admin accounts with random hexadecimal usernames, further complicating detection and removal efforts.
Traffic Direction System (TDS)
The latest version, known as DollyWay v3, employs a Traffic Direction System (TDS) that evaluates various visitor parameters before executing redirects. This system ensures that logged-in users, known bots, and visitors without referrers are excluded from redirection, significantly reducing the risk of detection by security tools. 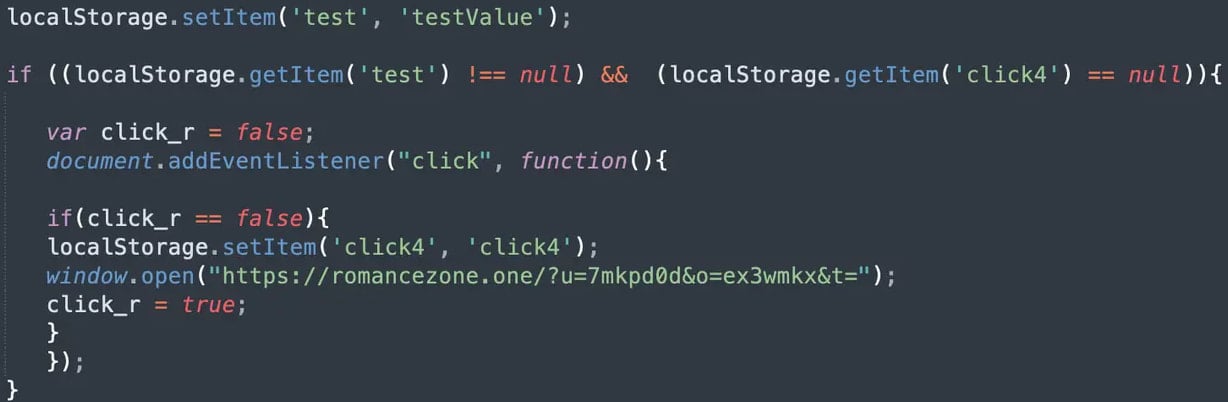
Backdoor Mechanisms
DollyWay incorporates advanced backdoor mechanisms that allow attackers to execute arbitrary PHP code on compromised sites. When a request containing a specific identifier is detected, the malware can create PHP files that enable further exploitation. The malware also captures admin login credentials by monitoring POST requests, allowing attackers to maintain access even if the initial admin accounts are discovered and deleted.
Indicators of Compromise (IoCs)
GoDaddy has shared comprehensive indicators of compromise associated with the DollyWay malware to assist in detection and remediation efforts. This includes identifying malicious admin users, the presence of the WPCode plugin, and various obfuscated code patterns. To safeguard against threats like DollyWay, organizations can utilize GrackerAI's AI-powered cybersecurity marketing platform. GrackerAI helps you transform security news into strategic content opportunities, enabling your marketing team to produce timely, relevant content that resonates with cybersecurity professionals. Explore our services at GrackerAI or contact us for more information on how we can enhance your cybersecurity content strategy.
Latest Cybersecurity Trends & Breaking News
AI and Cybersecurity: Understanding the Current Landscape Asia Morning Briefing: Crypto Industry 'Unprepared' For Quantum Threat Says Analyst





