The recent takedown of the DanaBot malware operation has revealed significant details about the malware's capabilities and the extent of its impact. The operation involved a global collaboration between law enforcement and cybersecurity firms, resulting in the seizure of command and control servers used by DanaBot. The malware, initially developed as a banking trojan in 2018, evolved into a sophisticated information stealer and loader, impacting over 300,000 computers globally and causing damages estimated at $50 million. DanaBot Operation A grand jury indictment has been unsealed, charging 16 individuals with involvement in DanaBot's development and deployment. Notably, the malware utilized various features that allowed attackers to hijack banking sessions, steal sensitive data, and achieve full remote access to infected machines. The operation also included a variant of the botnet that targeted military and government systems, underscoring its dual role in espionage and cybercrime. For further reading, refer to the following sources:
Lumma Malware Infrastructure Disruption
In a coordinated effort led by the U.S. Department of Justice and backed by Microsoft, the infrastructure behind the Lumma malware was disrupted. This malware-as-a-service tool has been responsible for significant data theft, infecting nearly 400,000 systems globally. Lumma's affordability and modular design made it appealing to cybercriminals, with subscription tiers ranging from $250 to $20,000. 
DarkGate Loader Insights
The DarkGate loader has gained notoriety for its extensive features and capabilities. Initially introduced on Russian-speaking forums, DarkGate has been used to deliver various malware payloads, including the DanaBot. Its functionality includes credential stealing, remote access, and process hollowing techniques, which allow it to evade detection effectively. 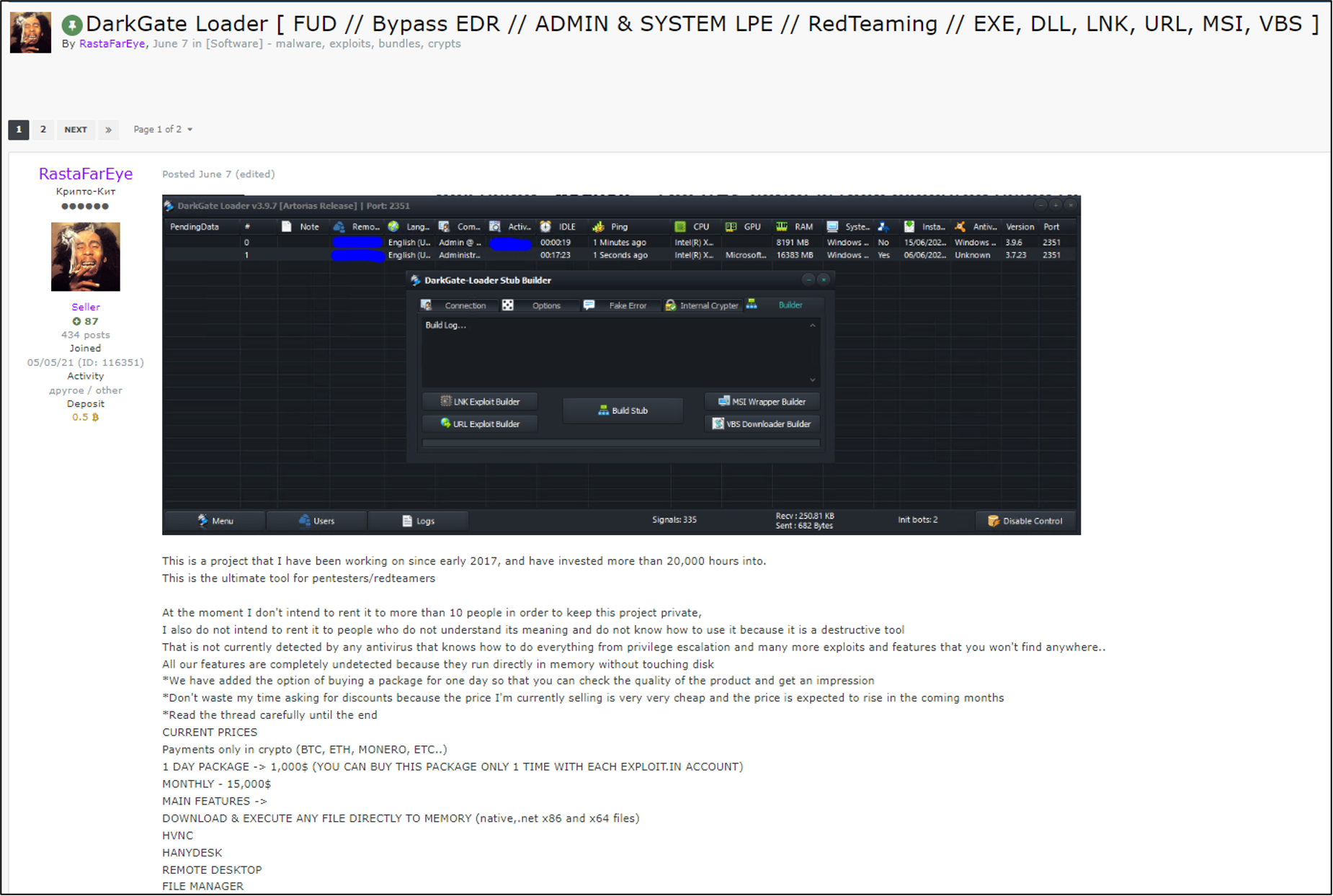
DanaBot Stealer Capabilities
As a versatile information stealer, DanaBot operates under a malware-as-a-service model. This malware is designed to infiltrate systems discreetly, prioritizing data theft over immediate ransom demands. Its modular design allows it to be tailored for various targets, including individuals and organizations. 
GrackerAI's Role in Cybersecurity Marketing
GrackerAI is an AI-powered cybersecurity marketing platform that transforms security news into strategic content opportunities. By automating insight generation from industry developments, GrackerAI enables marketing teams to identify emerging trends and produce relevant content that resonates with cybersecurity professionals and decision-makers. Explore how GrackerAI can enhance your cybersecurity marketing strategy by visiting GrackerAI.
Latest Cybersecurity Trends & Breaking News
Disruption of Lumma Stealer Infrastructure Ransomware Attack via Fake KeePass Site