Cybersecurity SEO: A Comprehensive Guide for Organizations
“Cybersecurity SEO is about more than getting traffic—it's about building trust.”
— Geeky Tech
Cybersecurity SEO is the practice of optimizing a security website to rank for industry-specific, threat-focused, and compliance-related search terms (Keywords or Prompts) across search engines and LLMs like ChatGPT, Gemini, and Copilot, and building trust among their prospects.
The goal is simple: increase visibility, attract qualified leads, and build trust and authority in a competitive security market.
It involves mainly these 5 core components:
Competitor Research
Conducting cybersecurity keyword research and targeting niche-relevant terms
Optimizing technical SEO to improve crawlability, performance, and site security
Creating high-quality content using threat-specific and solution-specific keywords
Building domain authority through high-quality backlinks from cybersecurity publications
GrackerAI is an AI editorial and programmatic SEO platform built specifically for cybersecurity and SaaS companies. It helps security marketers generate search-ready content, targeted keyword clusters, and long-tail programmatic pages that rank for technical, compliance, and threat-related queries.
For cybersecurity companies, being visible for the right queries at the right time is critical.
Suppose your target audience searches for a problem you solve—like “How to mitigate credential stuffing attacks”—and your company does not appear in search results or AI answers. In that case, you immediately lose a potential lead.
Cybersecurity is also a crowded and complex industry. Some buyers are highly technical (CISOs, security engineers), while others are non-technical (CEOs, compliance teams). Your SEO content needs to be clear, accurate, and easy for both groups to understand.
Table of Contents
Why Cybersecurity SEO Matters?
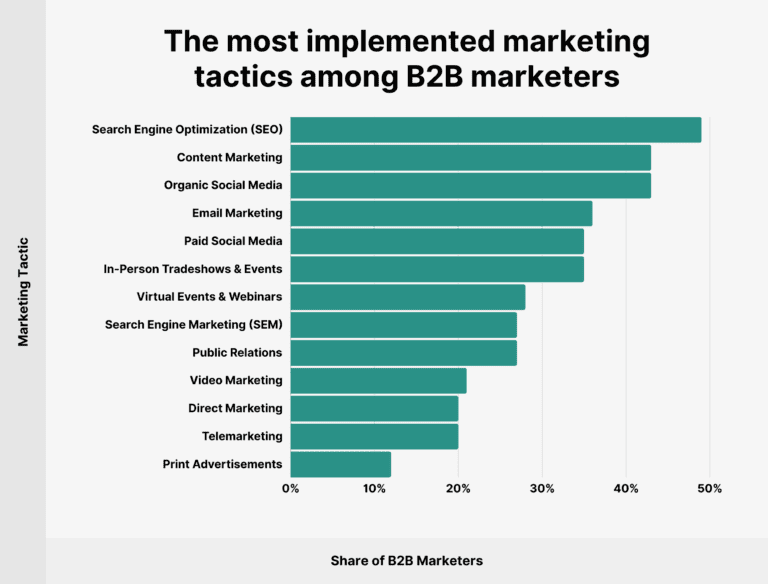
About 7 out of 10 B2B buyers start their research with a quick Google search. And with Google controlling nearly 85% of all searches, it shows that being visible and easy to find is very important for B2B or cybersecurity brands if they want early attention of their prospects.
In an industry worth $193.7 billion as of 2025, visibility is everything.
Why Visibility Matters
SEO helps cybersecurity vendors rank for:
Threat-based queries
Compliance-driven searches
Solution-focused keywords
Industry-specific long-tail terms
And today, visibility is not just about Google.
Organizations must also optimize for LLMs, ensuring AI models recognize their brand as a reliable source of cybersecurity content.
Key Reasons Cybersecurity SEO Matters
1. Search Habits:
Most cybersecurity buyers begin their journey online. Before they ever speak to a sales team, they’re researching threats, comparing solutions, and trying to understand what they actually need. This early research phase is your first opportunity to show up and earn their trust.
Here’s what the data shows:
90% of B2B customers initiate their journey with an online search.
80% of B2B customers rely on search engines.
70% of B2B customers consume content.
55% of B2B customers still find industry publications valuable.
What You Should Do
To make the most of your buyers’ search behavior, focus on these simple, high-impact actions:
1. Publish timely content on emerging cyber threats
Short updates or quick explainers on new vulnerabilities help you show up when buyers are actively researching what’s happening right now—and let you position your product as part of the solution.
2. Understand what your audience is searching for
Use Google Search Console, competitor research, and keyword tools to learn the exact questions and problems your prospects are typing into Google. Then create content that answers those needs directly.
3. Match the right content to the right search intent
Whether someone is looking for basic info, comparing vendors, or ready to buy, your content should meet them where they are.
4. Maintain strong overall SEO performance
Good technical SEO, quality content, and relevant backlinks help you rank on page one—where the research journey truly begins.
In short: turn your buyers’ search habits into an advantage by consistently showing up with helpful, relevant, and trustworthy content.
2. Building Trust:
As we have already discussed, building trust is very important in cybersecurity. Buyers want to feel confident that their data, systems, and people are safe in your hands. Before they talk to your sales team, they’re already looking for signals that your brand is credible and knows what it’s talking about.
Showing up consistently in search results is one of the strongest trust signals you can send. When prospects repeatedly see your content while researching threats, tools, or best practices, they naturally begin to view your company as a reliable expert.
A proper SEO for your cybersecurity company helps you stay visible in these early moments, turning casual researchers into confident buyers.
What Builds Trust
1. Publish genuinely helpful content
Create clear, accurate, and well-researched content that answers real questions cybersecurity buyers have.
2. Build authority with strong backlinks
Get referenced by reputable cybersecurity publications, partners, and industry blogs.
3. Show your expertise openly
Add case studies, certifications, awards, customer proof, and technical explanations where relevant.
4. Be transparent about your practices
Share how your security, compliance, and internal processes work—buyers respect clarity.
When you consistently do these things, search engines—and your prospects—start treating your brand as trustworthy. And the higher your pages rank, the more credible you appear to potential customers.
The higher your website ranks in search results, the more trustworthy it appears to searchers.
3. Attract a Targeted Audience:
Cybersecurity solutions aren't a one-size-fits-all deal. A hospital, a fintech startup, and a manufacturing company all face different risks — and they all search for solutions in different ways.
This is exactly why SEO is such a game-changer for cybersecurity companies. It's how you get in front of the people who desperately need what you've got, not just a bunch of random folks browsing.
And how do you do that? Long-tail keywords are your secret weapon here.
When someone searches for something super specific, like "cloud security for healthcare providers" or "ransomware protection for law firms," it shows clear search intent. Companies that are actually solving those exact problems have a much better chance of converting that visitor into a lead.
Honestly, good keyword research is key. It helps you get inside the heads of each of your target industries. What keeps them up at night? What threats are they sweating over? What solutions are they even comparing? When your content directly hits those points, the right people just… find you. It feels natural.
What You Should Do
1. Identify industry-specific problems
Look at your ICPs (healthcare, finance, manufacturing, SaaS, etc.) and list the unique threats, compliance needs, and pain points for each segment.
Create content for each segment—not generic cybersecurity topics.
Instead of “What is ransomware?”, write content like:
“Ransomware Risks for Healthcare Providers”
“How Law Firms Can Prevent Credential Stuffing”
“Cloud Security Checklist for Fintech Teams”
2. Use long-tail commercial keywords
Target terms that show stronger intent, such as:
“MDR solutions for small businesses.”
“Zero Trust for remote teams.”
“SOC 2 compliance tools for startups.”
These keywords bring visitors who are already closer to making a decision.
3. Build mini-topic clusters for each industry.
Create clusters like:
Healthcare Cybersecurity
Legal Cybersecurity
SMB Cybersecurity
The more complete your cluster, the more search engines trust you for that audience.
When you focus on industry-specific needs instead of broad cybersecurity topics, you attract visitors who actually need your solution — not random traffic that won’t convert.
4. Improve Lead Quality & Conversion Rates:
Today it’s not about ‘get the traffic, it’s about ‘get the targeted and relevant traffic.’” Adam Audette
In cybersecurity, more traffic doesn’t automatically mean more leads. What matters is attracting people who are already aware of the problem and are actively exploring solutions. SEO helps you bring in this “ready-to-act” audience.
When your content matches the intent behind keywords like “best MDR tools for SMBs” or “SOC 2 automation for startups,” the visitor is already closer to taking action — which naturally increases conversion rates.
What You Should Do
1. Create pages with a clear next step
Use simple, relevant CTAs like “Book a demo,” “Scan your environment,” or “Download breach checklist.”
2. Optimize landing pages for decision-makers
Add use cases, short summaries of benefits, and quick comparison sections.
3. Offer helpful lead magnets
Templates, checklists, and security assessment tools work extremely well in cybersecurity.
Good SEO brings the right people to your site — conversion-focused UX turns them into real leads.
5. Cost-Effective Marketing Strategy:
Cybersecurity marketing can get expensive fast, especially in paid search, where CPCs for keywords like “SOC 2 compliance” or “MDR services” can run very high. SEO, on the other hand, compounds over time.
Once you rank for valuable queries, you continue to generate traffic and leads without paying for every click — making SEO one of the most cost-efficient growth channels for cybersecurity companies.
What You Should Do
1. Invest in content that compounds
Evergreen pages like “What is Zero Trust?” or “Types of Cyber Attacks” build traffic year after year.
2. Build a repeatable content workflow
Assign roles or use tools (like GrackerAI) to consistently publish optimized content.
3. Balance paid and organic
Use paid search only where needed and let SEO carry long-term traffic growth.
SEO doesn’t replace paid marketing, but it significantly reduces dependency on it.
6. Stay Ahead of the Competition:
As cyber threats continue to rise, the demand for cybersecurity companies is growing alongside them.
Cybersecurity is crowded and getting noisier every year. New vendors, tools, and frameworks appear constantly — and buyers compare their options heavily online.
A strong SEO strategy keeps you ahead of competitors by ensuring your brand shows up more often in key research moments. If your competitor ranks above you for your core solutions, they will win the conversation long before your sales team gets involved.
What You Should Do
1. Track competitor keywords regularly
Identify where they outrank you and create better, more useful content on those topics.
2. Differentiate with expertise
Add insights, real examples, and technical explanations competitors don’t provide.
3. Watch industry trends early
Publishing content on new threats or regulations before others helps you dominate topics early.
When you consistently outrank competitors, you become the brand that buyers remember first.
Source: Backlinko
Common Cybersecurity SEO Challenges And How to Fix Them
SEO for Cybersecurity companies is not like the regular SEO for a technical niche.
One of the biggest challenges cybersecurity marketers face is turning highly technical concepts, threats, and frameworks into clear, readable, and in storytelling forms that their potential buyers can actually understand and trust.
You’re not just explaining “what is ransomware” — you’re translating vulnerability reports, CVEs, attack flows, compliance requirements, and detection strategies into articles, guides, and resources that feel human, practical, and genuinely useful. And doing this well is hard.
On top of that, cybersecurity SEO comes with challenges most industries never face: intense keyword competition, strict Google E-E-A-T expectations, security risks like SEO poisoning, fast-expiring threats that require constant content updates, and a landscape that evolves faster than most teams can publish.
Here are the challenges that matter most today, along with practical fixes your team can actually use.
1. Competing for Highly Competitive Keywords
One of the biggest headaches in cybersecurity SEO is the keyword competition.
Most broad terms — like “cybersecurity services” or “network security” — are already taken over by huge players such as government sites, analyst firms, and large security vendors.
If you’re a mid-sized or growing cybersecurity company, trying to outrank them is almost impossible in the beginning.
Why does this become a real challenge?
Your content gets buried under authoritative .gov/.edu sites
Google trusts big industry domains more for security topics
Broad keywords bring random, low-quality traffic
LLMs also lean toward well-known sources
You end up spending time on keywords you cannot realistically win
So instead of helping, targeting these keywords actually slows down growth.
How to Fix it
Here’s how cybersecurity marketers solve this problem without fighting the giants-
1. Use a mix of high-volume + niche keywords (Longtail Keywords)
Instead of only aiming for broad terms, build your strategy around a mix of:
High-volume cybersecurity keywords
Industry-specific keywords
Compliance keywords
Threat-driven keywords
Long-tail, intent-based searches
Solution-focused keywords
This gives you both reach and relevance without fighting impossible battles.
If you want a clean breakdown of which cybersecurity keywords actually matter today — including search volume, competition, and niche-specific terms — you can check this guide:
Top Cybersecurity Keywords: Boost Traffic & Conversion
This guide helps you pick the right keywords before you start building content — which saves months of effort.
2. Build Keyword Clusters around Threat Trends
Cybersecurity buyers search heavily for emerging cybersecurity threats:
New ransomware strains
0-day vulnerabilities
CVE breakdowns
Industry breach analysis
Create small clusters like:
threats/cve-2025-xxxx
threats/ransomware-variant-guide
This builds topical authority, which both Google and LLMs love.
3. Create Industry-Specific Content Hubs
Every industry has different security needs:
Healthcare → HIPAA, PHI protection
Finance → PCI-DSS, ransomware
SaaS → IAM, API security
Manufacturing → OT security, ICS hardening
Industry hubs rank faster because they are highly specific and less competitive. You can use longtail keywords here which are very specific.
4. Produce comparison & evaluation content
Mid-funnel decision-makers search for:
“MDR vs XDR”
“Best IAM tools for SMEs”
“SOC 1 vs SOC 2 explained”
Competitor 1 vs Competitor 2
Best Alternatives of your competitor or popular tools in your niche
Cybersecurity marketers often avoid writing comparison content — which is why it ranks SUPER fast when someone finally does it.
5. Strengthen internal linking around your core topics
If you have 50+ cybersecurity blogs (which you do), you can build authority faster by:
Linking all threat-related articles together
Linking industry-specific pages into their clusters
Pushing authority toward your high-intent landing pages
This alone helps pages jump 10–30 positions in competitive niches.
2. Balancing Technical Accuracy With Readability
One of the hardest parts of cybersecurity SEO is writing content that works for two completely different audiences at the same time:
Technical readers → CISOs, security engineers, architects
Non-technical readers → CEOs, founders, compliance teams, procurement
Everyone in between → IT managers, product owners, mid-level evaluators
If your content is too technical, non-technical buyers won't understand it.
If it’s too simple, technical buyers won’t trust your expertise.
This is a challenge almost every cybersecurity marketer struggles with.
Why This Becomes a Real Problem
Cybersecurity terminology (IAM, SIEM, XDR, CVEs) gets overwhelming fast
Buyers need explanations, not jargon
Google expects clear, well-structured explanations for YMYL topics
LLMs prefer pages that explain complex ideas in simple language
If your content doesn’t strike the right balance, you lose trust, traffic, and conversions.
How to Fix This
1. Start simple → then go deeper
This is the easiest way to make content readable for everyone:
Open with a simple explanation (“What this is and why it matters”).
Then break it down technically for engineers and CISOs.
This approach helps both audiences stay engaged without dumbing anything down.
2. Use analogies, diagrams, and real examples
Instead of explaining IAM with technical terms, show:
A simple workflow diagram
A real-world example (“Here’s how a finance company uses this…”)
A visual comparison chart
Visuals make complex concepts easier for LLMs and humans to understand.
3. Create a Cybersecurity Glossary
This is one of the most powerful SEO tools for security companies:
Explains complex terms
Reduces jargon fatigue
Helps with internal linking
Improves topical authority
LLMs LOVE structured glossaries
How GrackerAI Helps You With This Challenge?
GrackerAI can automatically create content that is easy for non-technical readers yet still accurate and useful for technical decision-makers.
Here’s how:
1. Cybersecurity Glossary Hub (Fully Automated)
GrackerAI can build a glossary section with:
5,000+ cybersecurity terms
Simple + technical explanations
Related-term clustering
Real examples
Internal links to your product pages
This makes your entire site more readable and boosts topical authority for SEO.
2. Framework & Standards Libraries
For audiences needing deeper compliance clarity:
NIST
ISO 27001
CIS Controls
SOC 2
CMMC
GrackerAI creates “simple explanation → technical deep dive → checklist” content automatically.
Perfect for both CEOs and CISOs.
3. Technical Implementation Guides (Simplified + Detailed)
GrackerAI can create:
Step-by-step configuration guides
Architecture diagrams
Misconfiguration fixes
Industry-specific best practices
Each guide can include both:
Plain-English summary for non-technical readers
Deep technical walkthrough for engineers
4. Threat Explainability Content (For Both Audiences)
When new threats appear, GrackerAI can create two layers:
Simple breakdown (“What happened and why it matters”)
Technical analysis (IoCs, CVSS, attack chains, prevention steps)
This is perfect for CVEs, ransomware updates, and breach analysis.
3. Building Trust in a “Zero-Trust” Industry
Cybersecurity is one of the few industries where nobody believes anything at first glance — and honestly, buyers shouldn’t. They’re cautious, skeptical, and always double-checking claims. They have to be. They’re responsible for protecting data, money, and entire systems.
This creates a challenge most industries don’t face:
Even if your product is great, buyers won’t trust you until you prove it.
And this doesn’t apply only to your prospects. Google is even stricter. LLMs are even stricter than Google.
YMYL + E-E-A-T rules hit cybersecurity harder than almost any other niche. So if your brand doesn’t show credibility clearly, you lose rankings and buyer trust.
Why This Becomes a Real Challenge
Cybersecurity is full of scams → buyers naturally question everything
Google treats security content as “high risk” → demands real expertise
LLMs pull answers from “trusted” brands first → not from unknown sites
Most cybersecurity websites talk about expertise but don’t show it
Buyers don’t understand technical claims unless supported by proof
Trust is the barrier, and it can be passed by proper SEO work.
How to Fix it
1. Show credentials and real experience (Google and LLMs care about this)
Cybersecurity falls under Google’s YMYL category, which means both Google and LLMs are strict about who they trust. They want to see that your content comes from someone with real security experience — not just a generic writer.
This is why your technical pages should be written (or reviewed) by people who understand security deeply, such as:
security engineers
technical content writers
solution architects
developers who built the product
When their names appear as the author, it sends a strong trust signal.
Google and LLMs look for things like:
cybersecurity certifications (CISSP, CISM, CEH, OSCP, ISO 27001, etc.)
hands-on security experience
real-world roles (SOC analyst, pentester, cloud security engineer)
a history of publishing accurate technical content
The more your content reflects real expertise, the more value search engines and AI models assign to it — because they know the reader is getting trustworthy information.
2. Publish case studies that show real outcomes
People trust cybersecurity companies when they can see what you’ve actually done — not what you claim you can do.
The best way to do that is through simple, honest case studies.
Example:
If you helped a client reduce false positives, show it.
If you helped a team recover faster from ransomware, show the difference in hours or days.
If you helped a small company pass a compliance audit, explain what changed.
Even something like:
“We helped a fintech team cut alert fatigue by 40%.”
“We reduced dwell time for one customer from days to hours.”
Small, specific wins build more trust than big promises. And always link to whatever you can — a page, a testimonial, a screenshot. Buyers like to verify things for themselves.
But what if you’re a new cybersecurity company and don’t have case studies yet?
That’s normal. Every security startup faces this.
Here’s what you can do:
Start with simple scenario-based examples
Use internal product data
Do small pilot projects
Break down real breaches or CVEs
3. Explain security topics clearly and transparently
Cybersecurity gets complicated fast — CVEs, attack chains, Zero Trust, IAM, lateral movement… the list never ends.
But buyers trust you more when you explain things in a way that actually makes sense.
Breakdown
What the attack was
How it unfolded
Where things went wrong
Why it mattered
And how your approach fixes or prevents it
4. Get mentioned by credible cybersecurity sources
In cybersecurity, who talks about you matters more than how many people talk about you.
A backlink from a random website doesn’t mean much.
But a mention from a place the security community actually respects — like DarkReading, ThreatPost, BleepingComputer, NIST, MITRE, or even well-known vendors — carries a lot more weight.
These are the sources Google and AI models trust by default. So when they reference you or link to you, that trust transfers.
And it doesn’t have to be a full-featured story. Even small things help:
Contributing a quote
Sharing a quick insight
Getting interviewed
Publishing a research snippet
Writing a guest article
Slowly, these mentions build your reputation in the ecosystem.
If you want a deeper breakdown of how to earn these types of backlinks and mentions (and which ones matter most in cybersecurity), here’s a detailed guide:
Link Building Strategies for Cybersecurity Websites: A Comprehensive Guide
5. Add small trust signals across your site
Trust in cybersecurity is built in small moments — often the details people overlook.
Things like:
Showing the author’s name and credentials
Adding “security reviewed by ___” under technical content
Sharing real screenshots instead of mockups
Showing compliance badges (SOC 2, ISO, HIPAA, etc.)
Listing customer logos or case-study links
Adding analyst quotes or ratings
It’s a simple way to show that you're not hiding behind marketing claims — you're open, transparent, and confident in what you do.
4. Technical SEO Problems
Cybersecurity websites become technically heavy very quickly — with documentation pages, product guides, diagrams, CVE content, and constant updates. All of this makes them slower, harder to crawl, and much more likely to run into technical SEO issues that quietly limit rankings and AI visibility.
Why Technical SEO Is a Challenge for Cybersecurity Websites?
1) Heavy, documentation-style content slows pages
Security pages often include code blocks, diagrams, demos, screenshots, and large JS components.
This hurts Core Web Vitals and makes Google/LLMs struggle to render the content properly.
2) Content grows too fast to stay organized
Threat updates, CVE notes, compliance changes, and product updates pile up.
Old URLs and outdated structures rarely get cleaned, which creates crawl and indexation problems.
3) Sitemaps and indexing break quietly
Common issues:
stale or removed URLs in the sitemap
orphan pages
duplicate/near-duplicate content
wasted crawl budget
This causes important pages to stay unindexed for weeks or months.
4) Overlapping topics cause canonical problems
Cybersecurity content overlaps naturally (IAM, Zero Trust, vulnerabilities, compliance).
Without proper canonical tags, Google splits authority between similar pages.
5) Broken pages accumulate quickly
Because content updates so frequently, sites end up with:
404s
soft 404s
redirect loops and chains
crawled but not indexed
These weaken user experience and downgrade authority.
6) Core Web Vitals fail more often
Heavy content → poor LCP, CLS, and INP. This directly affects both search rankings and AI visibility, since slow pages rarely get fully crawled.
How to Fix it
1. Improve Core Web Vitals the “security content” way
Convert diagrams to SVG
Lazy-load screenshots & videos
Use next-gen formats (WebP/AVIF)
Limit JS on product/docs pages
Use a CDN
Remove unused tracking scripts monthly
2. Fix indexing and sitemap issues
Clean the sitemap monthly
Remove outdated URLs
Split large sitemaps
Add internal links to new pages immediately
Submit key pages via Search Console
3. Use canonical tags to stop competing with your own pages
When multiple pages cover similar threats or frameworks, combine them or set a clear canonical. This protects your topical authority.
4. Clean up broken links and redirects
Quarterly must-do:
fix 404s and soft 404s
remove redirect chains
use permanent 301 redirects
Security sites change URLs often—don’t let old pages rot.
5. Add schema markup that AI models value
Use:
FAQPage for guides
HowTo for configurations
Organization for brand info
Software application for products
TechArticle for in-depth blogs
Schema helps Google and AI understand your pages instantly.
5. Mobile UX Becomes a Serious SEO Problem for Cybersecurity Websites
Google doesn’t just “prefer” mobile-friendly sites anymore — it ranks you based on your mobile version first.
And that’s a problem for cybersecurity companies, because security content is naturally heavy and not built for small screens.
According to the Google Guidelines on Mobile First Indexing, Google uses the mobile version of a website as its primary source for indexing and ranking all pages
Cybersecurity pages often include:
diagrams
compliance tables
long explanations
screenshots
code blocks
All of this looks fine on desktop, but on mobile, it turns into zooming, pinching, scrolling sideways, slow loading, and instant frustration.
And Google picks up that frustration.
Why does this hurt cybersecurity sites specifically?
Mobile-first indexing → Google uses your mobile version to decide rankings
Poor mobile UX → higher bounce rates (especially for long technical pages)
Slow load speeds → Core Web Vitals fail
Confusing layouts → users can’t read diagrams or tables
LLMs also treat unreadable content as low-quality
If your mobile experience is bad, your SEO ceiling becomes low — even if your desktop version is perfect.
How to Fix it
1. Make technical visuals readable
Most cybersecurity diagrams break on mobile.
Fix by:
offering tap-to-zoom
using simplified mobile versions of architecture diagrams
breaking big tables into scrollable blocks
Even one of these changes reduces mobile bounce rates immediately.
2. Rewrite long content into mobile-friendly formats
Security content is long by nature, but you can make it readable:
Use short paragraphs and natural breaks
Add expandable sections for deeper explanations
Summarize complex ideas before going deeper
Add real-world examples instead of long theoretical blocks
This helps both non-technical decision-makers and technical teams.
3. Optimize for Core Web Vitals (the cybersecurity way)
Mobile performance matters more than desktop
Fix:
Compress heavy dashboard images
Lazy-load videos and screenshots
Remove old tracking scripts
Reduce JS from product demo widgets
Use a CDN
Cybersecurity sites improve dramatically when visual content is optimized.
4. Make forms and CTAs mobile-first
Security companies often have desktop-length demo forms.
On mobile, they’re impossible.
Fix:
Single-column layout
Fewer fields
Larger buttons
Auto-fill enabled
This improves conversion instantly.
6. Outdated Content
In most industries, a blog can stay relevant for months or years. Not in cybersecurity.
Your content becomes outdated in weeks, sometimes days:
A new CVE drops
A vendor changes its IAM flow
A compliance requirement update
A threat strain evolves
Cloud platforms release new security features
Readers notice this instantly — and so does Google. Outdated content quietly destroys trust and rankings.
Why is this such a big SEO challenge?
Old examples make you look disconnected from the threat landscape
Outdated compliance info leads to misinformation (big trust issue)
LLMs avoid citing outdated cybersecurity pages
Competitors who update faster dominate rankings
Outdated security content isn’t “just stale.” It sends negative trust signals to both your prospects, Google, and AI.
How to Fix It
Instead of rewriting everything randomly, use an update schedule:
Threat/CVE content → weekly
Compliance content → monthly
Vendor comparison pages → quarterly
Educational/strategic content → every 6 months
A simple refresh can include:
Updating statistics
Adding the latest attack examples
Referencing a recent CVE
Updating compliance checklists
Replacing broken diagrams
Improving readability
Adding relevant internal links
Even a 20% update boosts rankings dramatically.
This is exactly why top cybersecurity companies dominate SERPs — they stay “current” by default. Updating content is a major ranking factor and an LLMs and Google visibility booster.
7. Keyword Cannibalization (A Very Common Cybersecurity SEO Problem)
Keyword cannibalization simply means you have multiple pages on your site trying to rank for the same keyword or search intent. When that happens, Google doesn’t know which one to pick — so it ranks none of them well.
Why does this happen so often in cybersecurity?
Cybersecurity topics naturally overlap:
Zero Trust overlaps with IAM
MFA overlaps with Identity Security
XDR overlaps with SIEM
CVE content overlaps with vulnerability management
So teams keep writing content… and without realizing it, they create 5–8 pages covering the same idea in slightly different ways.
Example:
Three different blogs are trying to rank for “Active Directory hardening” or “Zero Trust best practices.”
Suddenly, your own content is competing against itself.
How to Fix it
1. Identify overlapping pages
Run a quick audit: look for pages covering the same threat, framework, or security concept.
2. Merge → don’t multiply
Combine weak or repetitive pages into one strong, complete resource.
3. Use 301 redirects
Redirect old URLs so their authority transfers to the “master” page.
4. Add canonical tags
Use them when merging isn’t possible (e.g., similar compliance guides).
5. One keyword → one page
Assign each major keyword or intent to one URL only.
Cleaning up cannibalization immediately helps your best cybersecurity content rise in rankings — and makes your site clearer for both Google and LLMs.
8. Missing High-Intent Pages
Most cybersecurity websites attract traffic through blogs and educational content, but they don’t have pages built for people who are actually ready to buy. This creates a major gap between awareness and conversion — the stage where SEO should deliver the highest ROI.
How does this impact cybersecurity SEO?
When buyers reach the point where they’re actively comparing solutions or looking for a provider, Google expects to see focused, solution-oriented pages.
If your site doesn’t have them, Google simply sends those high-intent searches to competitors — even if your blog content is stronger.
So-
You get impressions
You get traffic
But you lose the best leads to vendors who structured their site properly.
How to Fix it
1. Create dedicated solution pages
Not generic product pages — but pages clearly aligned with buyer problems and outcomes.
2. Build industry-specific pages
Cybersecurity needs vary drastically across industries. Dedicated pages help Google understand who you serve and why you’re relevant.
3. Add use-case pages
These help convert users who already understand the problem and are evaluating approaches.
4. Link blogs to these pages
Your blogs bring the traffic.
Your high-intent pages close the gap.
Internal linking connects both and increases topical authority.
In short, most cybersecurity websites struggle because:
They chase the same broad keywords, making it nearly impossible to stand out against analysts, vendors, and government sites.
Content becomes too technical or unclear, so non-technical buyers bounce while Google struggles to understand the page.
Trust signals are weak, which is deadly in a zero-trust industry where buyers and search engines expect proof, not claims.
Technical SEO issues — broken links, slow pages, messy sitemaps, duplicate content, and outdated posts.
They lack pages built for real buyers, so even with traffic, they don’t capture high-intent searches that actually convert.
10 Proven SEO Strategies for Cybersecurity Companies
Cybersecurity SEO isn’t about ranking for general marketing keywords — it’s about earning trust, demonstrating expertise, and showing up when buyers search for very specific threats, compliance issues, and technical problems.
Here are the 10 proven cybersecurity SEO strategies
1. Comprehensive Keyword Research
Most cybersecurity SEO fails because a cybersecurity marketer starts with keywords instead of problems.
Your buyers don’t search for common terminology like "Cybersecurity Services" — they search when something breaks, fails, or needs explaining to their leadership team.
If you understand the situation behind a search, you win the keyword — no matter what the exact phrase is. Real cybersecurity keyword research starts with the incident → not with the keyword tools.
Here’s how experienced cybersecurity marketers do it:
They listen to support tickets, sales calls, and Slack screenshots from engineers.
They map keywords to security pain points like compliance confusion, misconfigurations, cloud visibility issues, vendor audits, downtime, and cost concerns.
They categorize keywords by urgency, not search volume.
They align keywords with the buyer’s internal pressure — board reporting, risk acceptance, audits, pentest findings, etc.
This approach gives you keywords that convert, not keywords that just bring traffic.
Common Ways to Find the Right Cybersecurity Keywords
1. Use Google Itself (The Free Hack Every Cybersecurity Marketer Should Use)
You don’t need giant and expensive keyword research tools for your first draft of keywords. Just type your primary keyword and topics related to your niche and your target market into Google (IAM, cloud risk, DLP, etc.), but don't hit enter. Pay attention to the suggestions that pop up in the dropdown menu (this is Google Autocomplete). These are actual searches that people are making! This Autocomplete "hack" is easy and free.
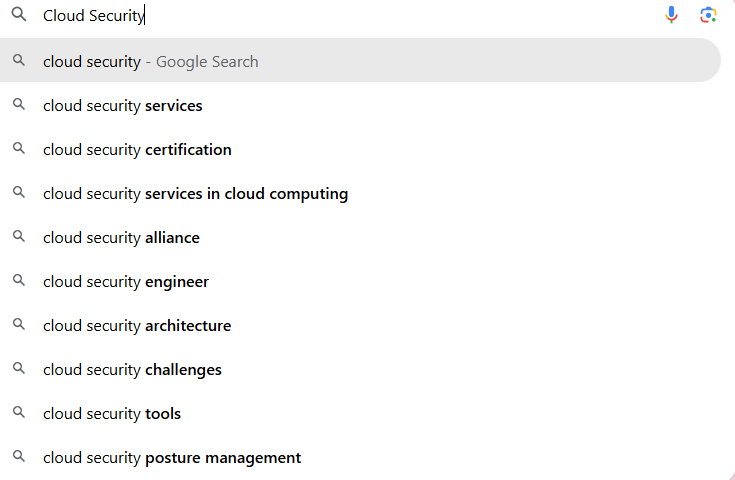
Another Google Hack for Keyword Research
Google also shows you related questions and search results. Look what you can do!
Check the “People Also Ask” and “Related Searches” sections — they show the exact questions and variations people search for. Use these to understand what buyers are really looking for and to find keyword ideas you may have missed.
1. Use Tools Only to Validate
Once you know what people search, use tools like LogicBalls, Ahrefs, and SEMrush to:
Check real search volume
Estimate difficulty
Find similar variations
Spot gaps competitors are ranking for
If you want a deeper, cybersecurity-focused approach to choosing keywords, you can check this guide: Keyword Research Tips for Cybersecurity SEO
2. Prioritize High-Intent Long-Tail Keywords
Cybersecurity long-tails convert better because they show context: industry, environment, urgency, or compliance pressure.
They may have lower volume, but they attract buyers who already know what they need — not just people “researching.”
3. Check Competitor Rankings for Missing Topics
Analyze which pages bring traffic to competitors to understand:
What Google rewards in your niche
Which topics you haven’t covered yet
Where competitors are weak
This gives you a roadmap without reinventing anything.
4. Use Your Own Customer Conversations
The best keywords come from:
Sales calls
Demo questions
Support tickets
Onboarding conversations
This is the real language your buyers use — and it’s often more valuable than anything found in a tool.
2. Create Unique & High-Quality Content
When you are writing content, remove everything that doesn’t benefit the customer.” Dario Sipos
Most cybersecurity content sounds the same — recycled definitions, generic “best practices,” and zero real insight. Buyers don’t trust that. What works is content that shows how security actually works in the real world.
Write about things your team sees every day: common misconfigurations, mistakes during audits, threat trends, gaps you notice during onboarding, or simple explanations of technical topics that even a non-technical stakeholder can follow. This kind of firsthand clarity builds trust, improves E-E-A-T, and is the type of content Google and LLMs prioritize.
If you already have deep-dive guides, use this section as a “value snapshot” — the quick version a busy CISO or marketer can skim and immediately apply.
If you want a deeper look and wanna write SEO friendly cybersecurity articles, check out this guide: Step-by-Step Guide to Writing SEO-Friendly Cybersecurity Articles
3. Make Your Website Secure & User-Friendly
If a cybersecurity company’s own website feels slow, insecure, or outdated, trust dies instantly. Make sure the site loads fast, passes Core Web Vitals, uses HTTPS everywhere, and is simple enough that even non-technical decision-makers can navigate it. A secure, clean site quietly boosts both rankings and conversions.
4. Optimize for Local Searches
If your cybersecurity business has a physical location or serves specific geographic areas, you'll need to optimize for local SEO. This helps your company become more visible in local searches.
The first important step is to claim and keep your Google Business Profile (formerly Google My Business) up-to-date. You should also ensure your business is listed accurately on other local directories, like your city's Chamber of Commerce or national organizations such as Yellow Pages or Yelp.
Make sure your NAP (name, address, phone number) is correct and that all other information is current on every directory listing. Your Google Business Profile is especially crucial because these profiles appear at the top of Google's search results for local queries. You can optimize this profile to improve your chances of appearing in the top local results.
Some additional local SEO techniques include:
Encouraging your best customers to leave reviews on Google
Adding location pages to your website that are optimized for location-based keywords
Creating locally-focused content on your blog about unique cybersecurity issues businesses face in your area
You can improve your local SEO and check whether your local SEO ranking is improving or not from these local rank checker tools
5. Optimize Your Technical SEO
Cybersecurity sites grow fast and break fast — outdated URLs, old documentation, redirect chains, slow dashboards, near-duplicate posts. Fix indexing issues, 404s, sitemaps, Core Web Vitals, and weekly broken-page reports before publishing anything new. Technical cleanup alone can double visibility in competitive niches.
Check out this Mastering Technical SEO Audits: A Comprehensive Guide for Marketing Professionals to learn all technical SEO hacks for your cybersecurity SEO
6. Optimize for On-Page SEO
On-page SEO is the practice of optimizing specific web pages to improve their rankings in search results and draw in more organic traffic. Here are the main elements to concentrate on:
A. Optimize Title Tags and Meta Descriptions for Keywords
Title tags and meta descriptions are the initial elements that users encounter when your pages show up in search results. These components are essential in determining whether users choose to click on your link.
Title Tags: Use the main keyword near the beginning of the title tag. Keep it under 60 characters and make sure it clearly describes what the page is about.
Meta Descriptions: Include the primary keyword and summarize what readers can expect from your page. Keep these under 160 characters.
B. Optimize H1-H6 Headings for Keywords
Using keywords in your headings helps structure your content for readers, LLMs, and search engines.
C. Optimize Your Content for Keywords
The body of your content is where you can provide value through keyword optimization.
Include primary keywords within the first 100 words and throughout longer content.
Use secondary keywords throughout the text to support the primary keywords.
D. Build a Strong Internal Linking Structure
Internal linking connects different pages of your website, which can improve SEO by making navigation easier for both users and search engines.
E. Optimize Your Images
Image optimization improves loading speed and user experience, which is important for SEO.
Name your image files clearly, using descriptive names that include keywords. Instead of “image1.jpg,” use something like “ransomware-prevention-tool.jpg” so search engines understand what the image is about.
Add alt text that describes the image, including keywords if relevant. Alt text helps images rank better in search and assists visually impaired users.
Compress images and choose the right formats to ensure they load quickly. Use JPEG for photos and PNG for graphics.
F. Implement Structured Data
Structured data offers extra context to search engines, allowing them to grasp your page content more effectively. This can enhance the chances of your content being featured as a rich snippet at the top of search results, boosting visibility and traffic. Typical types of structured data for cybersecurity companies include FAQs, product reviews, service listings, and how-to guides. Incorporating structured data aids search engines in categorizing and showcasing your content more efficiently in search results.
7. Build High-Quality Backlink
Building backlinks is super important for SEO on Google and improving AI visibility. These are links from other websites that point to your site. They tell search engines that your content is trustworthy and valuable. The more respected the website links to you, the better it is for your search rankings. Here’s how to get good backlinks:
1. Guest Posts: Write guest posts for well-known blogs in your field. This shows your expertise and gets you a backlink. Pick blogs with a similar audience and high authority.
2. Great Content: Create useful and unique content. If it’s relevant, you can add a link to your site in your bio or within the content.
3. Ask for Links: If your content adds value to someone else’s article, ask them to link to your site. This works well if your content supports their main points.
4. Press Releases: Share important news about your business, like new products or awards. News sites and blogs might pick them up and link back to you.
5. Check Your Backlinks: Regularly look at the backlinks you have. Some tools can help with this:
Ahrefs: Shows detailed info about backlinks and helps you track competitors.
SEMrush: Gives an overview of your backlinks and flags any that might hurt your SEO.
Moz Link Explorer: This breaks down your backlink profile and shows trends over time.
In cybersecurity, who links to you matters more than how many links you have. Mentions from security publications, vendors, researchers, or compliance experts transfer massive authority. Publish original insights, data, and mini-research updates to earn natural links.
8. Improve User Experience
A good user experience (UX) is really important for SEO. It helps keep people interested in your site and affects things like bounce rate, dwell time, and click-through rate (CTR). All these things can change how high your site shows up in search results.
Bounce Rate
If a lot of people leave your site right away, it means they didn’t find what they were looking for or had trouble using your site. To fix this, make your site easy to use, with clear navigation, useful content, and fast loading times. This shows search engines that your site is valuable.
Dwell Time
This is how long people stay on your site after clicking on search results. The longer they stay, the better it looks to search engines. You can help people stay longer by making your site easy to use and interesting.
Click-Through Rate (CTR)
Your UX starts working even before people visit your site. Good title tags, meta descriptions, and rich snippets can make people want to click on your link in search results. Once they’re on your site, a good UX keeps them interested.
Why UX Matters for SEO
A well-designed site keeps visitors happy, reduces bounce rates, and helps more people take action (like buying something or signing up). This means having:
Easy-to-use navigation
Fast loading times
Well-organized content
Clear calls-to-action (CTAs)
Security buyers are skeptical. They don’t read long paragraphs. Clean layouts, short sections, strong navigation, light images, and clear CTAs improve dwell time and reduce bounce. If your site feels “too technical,” users leave — and Google assumes the page isn’t helpful.
9. Use Case Studies and Video Content to Showcase Expertise
Cybersecurity buyers trust proof, not promises. Case studies showing real results (improved audit scores, reduced alert noise, better response times) and short explainer videos build credibility instantly. Even a 45-second walkthrough of how your solution works can outperform written content.
10. Tracking and Measuring SEO Performance
In cybersecurity, tracking “more traffic” is useless. What matters is whether the right people are finding you and whether that visibility turns into a pipeline.
Here’s what you should actually watch:
How fast new pages get indexed
Cybersecurity content moves fast. If Google takes weeks to index your threat or compliance pages, you lose momentum.
Growth in niche, long-tail keywords
Terms tied to CVEs, compliance controls, attack types, or industry-specific needs — these bring your real buyers.
Bottom-funnel traffic
Solution, industry, and use-case pages should grow steadily. If they aren’t, your SEO isn’t driving sales conversations.
Demo/trial conversions
If organic traffic isn’t turning into demos, sign-ups, or assessments, you’re ranking for the wrong intent.
Visibility on threat & compliance topics
Ranking early for new vulnerabilities or regulation updates builds trust faster than any ad.
Review these monthly → refresh what drops → scale what works.
For a deeper breakdown of all 10 strategies, here’s the full guide: 10 Proven SEO Strategies for Cybersecurity Companies
Some Real Case Studies
1. Enterprise Cybersecurity Platform: $7M+ Leads from SEO
(Source: Productive Shop) Problem: A Fortune 100-trusted platform struggled to generate leads despite technical expertise. Strategy:
Published educational content about IoT/OT security risks
Optimized pages for "cybersecurity demo requests" and "expanding cyber attack surface"
Focused on long-tail keywords and thought leadership articles
Results:
50% increase in demo form submissions
172% surge in non-branded traffic
Generated $7M+ in sales pipeline from SEO-driven leads
2. Dubai Cybersecurity Firm: 37,992% Traffic Surge
(Source: Nuoptima) Problem: Low visibility against global competitors in UAE markets. Strategy:
Built 6 high-authority backlinks
Published 7,000+ words/month targeting "cybersecurity UAE" and local keywords
Monitored rankings daily with a keyword tracking system
Results:
Ranked No. 1 for "cybersecurity companies in Dubai"
37,992% increase in organic traffic (from near-zero)
4,503 new keywords indexed in 2 years
3. Castra (Now Lumify): 64% Traffic Growth in 5 Months
(Source: Amplifyed) Problem: Only 10 first-page keywords and 340 monthly users. Strategy:
Overhauled technical SEO (site speed, mobile optimization)
Targeted niche terms like "XDR Solutions" and "MDR Services"
Results:
64% increase in organic traffic
49 first-page keywords (from 10)
70-position jump for "XDR Solutions"
4. Balbix Cybersecurity Platform: 100% Traffic Boost
(Source: Miromind) Problem: Low rankings despite valuable content. Strategy:
Created content clusters around cybersecurity pain points
Optimized for keywords like "cybersecurity risk assessment"
Results:
Doubled organic traffic in under a year
Secured top-page rankings for competitive terms
Key Takeaways from These Wins
- Local SEO works: Geo-targeted pages (e.g., "Dubai cybersecurity") convert 3x better. - Content depth matters: Pillar articles ranking for 100+ keywords outperform short posts. - Demo-focused CTAs: Pages with "Get a Free Risk Assessment" convert 50%+ leads. - Technical SEO fixes: Site speed improvements alone drove 38% traffic growth for one client.
What These Firms Did Differently
- They answered real questions:
Created guides like "How to Stop Ransomware Attacks" instead of generic "cybersecurity solutions" content.
- Built trust through expertise:
Used case studies like "IoT Security Risks in Healthcare" to showcase niche knowledge.
- Tracked daily:
One team adjusted content weekly based on keyword ranking changes
What Type of Content Do Cybersecurity Buyers Want?
Cybersecurity buyers are looking for content that addresses their specific needs and challenges while building trust and demonstrating expertise. Here’s what they want:
Educational Content
How-To Guides and Tutorials: Buyers want practical advice on how to implement cybersecurity measures. For example, instructional videos on setting up zero-trust architectures can be very helpful.
Whitepapers and Reports: In-depth whitepapers on advanced threats like APTs (Advanced Persistent Threats) are valuable for decision-makers like CISOs.
Real-World Solutions
Case Studies: Buyers are interested in seeing how your solutions have worked for others. Highlighting ROI and risk mitigation in case studies can be particularly persuasive.
Product-Led Content: Show how your product solves problems without a hard sales pitch. For example, an article on securing SaaS companies can feature your product as part of the solution.
Expertise and Thought Leadership
Original Insights: Share your own expert commentary on industry trends and events. This positions your brand as a thought leader.
Webinars and Podcasts: Multi-vendor webinars and podcasts offer a platform to discuss cybersecurity issues in depth and engage with high-intent buyers.
Trust-Building Content
Security Certifications and Compliance: Highlight your compliance with industry standards and security certifications to build trust.
Customer Testimonials: Share success stories and testimonials from satisfied clients to reassure potential buyers.
Industry-Specific Content
Regulatory Compliance: Address the unique regulatory requirements of different industries. For example, healthcare providers need content on HIPAA compliance.
Industry-Specific Threats: Discuss the common threats faced by specific industries and how your solutions mitigate them.
Engagement and Interaction
Social Media: Engage with your audience on platforms like LinkedIn and Twitter. Regularly sharing insights and responding to comments can build a following.
Forums and Q&A Sites: Participate in discussions on Reddit, Quora, and industry forums to provide value and drive traffic.
Urgency Without Fear
- Highlight Risks: Use data to highlight the risks of not having adequate cybersecurity measures, but avoid scare tactics. Focus on how your solutions can help.
Personalized Content
- Buyer Personas: Understand the different roles within organizations (e.g., CISOs, IT managers) and tailor your content to their specific needs and pain points.
For more detailed strategies and practical tips, check out the Effective Cybersecurity Content Strategy. This resource provides comprehensive insights and tools to enhance your cybersecurity marketing efforts. By focusing on these types of content, you can address the needs of cybersecurity buyers, build trust, and position your brand as an industry authority.
SEO Tools for Cybersecurity Marketers
1. Semrush: Great for finding keywords and checking backlinks.
2. Ahrefs: Helps you find new keywords and see how well you rank.
3. Google Analytics: Tracks how many people visit your site and what they do there.
4. Moz: Helps you optimize your site and track your rankings. Additional Cybersecurity Marketing SEO Tools:
5. Yoast SEO: Makes sure your content is optimized for search engines.
6. Google Search Console: Checks if your site is indexed correctly and if there are any issues with your search rankings.
7. Social Media Platforms: Helps you build your brand and connect with potential customers.
8. Google Keyword Planner: Finds relevant cybersecurity keywords and shows how often they are searched.
9. Screaming Frog SEO Spider: Checks your site for technical issues that might affect your search rankings.
10. Clearscope: Ensures your content is optimized for target keywords and search intent.
11. GrackerAI: Converts recent security news into SEO-optimized blogs.
AI in Cybersecurity SEO
AI in Cybersecurity SEO means using AI tools with cybersecurity pratices to keep websites safe and help them show up higher in search results by optimizing content. AI looks at lots of information to find possible dangers and protect the site before anything bad happens. It also helps make website content better so it matches what search engines and people are looking for, which boosts the site’s performance.
Key Aspects of AI in Cybersecurity SEO
AI is transforming cybersecurity SEO by enhancing threat detection, improving incident response, and optimizing content strategies. Here are the key aspects:
1. Threat Detection and Prediction: AI can analyze large volumes of data to identify vulnerabilities and predict potential threats. For example, Darktrace uses machine learning to monitor network activity and flag unusual behavior, helping businesses stay ahead of attackers.
2. Incident Response and Mitigation: AI tools can automate threat detection and response, reducing the time it takes to address security incidents. For instance, CrowdStrike’s Falcon platform uses AI to investigate and identify the root cause of breaches, enabling faster mitigation.
3. Fraud Detection and Prevention: AI is widely used to monitor transactions in real-time and flag suspicious activities. Mastercard uses AI to analyze billions of transactions daily, identifying fraudulent ones with a 95% accuracy rate.
4. Advanced Malware Detection: AI can detect new and unknown malware by analyzing behavior rather than relying on known signatures. CylancePROTECT uses AI to block unknown malware types before they can infect a system.
5. Vulnerability Management: AI helps prioritize which vulnerabilities need immediate attention. Tenable.io uses AI to automate patch management, ensuring systems stay updated and secure.
Benefits of Using AI in Cybersecurity SEO
AI offers several benefits that enhance cybersecurity SEO efforts:
1. Enhanced Accuracy in Threat Detection: AI improves the accuracy of detecting threats by analyzing vast amounts of data with precision. Companies using AI report up to a 90% improvement in detecting complex attacks.
2. Reduced Response Time for Incidents: AI tools quickly identify and prioritize threats, enabling faster action. Organizations using AI reduced their average response time to incidents from 30 minutes to under 5 minutes.
3. Continuous Adaptation to Evolving Threats: AI adapts by learning from new attack patterns, allowing it to respond to emerging threats 40% faster than traditional systems.
4. Improved Operational Efficiency: AI automates repetitive tasks like scanning logs and prioritizing alerts, freeing up human experts to focus on strategic decisions. This can increase cybersecurity team productivity by 50%.
Examples of AI Tools Used in Cybersecurity SEO
Several AI tools are widely used in cybersecurity SEO:
1. Tenable’s Exposure AI: Scans networks for weaknesses and suggests critical fixes.
2. IBM Guardium: Protects sensitive data by patching high-risk vulnerabilities.
3. SentinelOne’s Singularity: Provides a real-time view of emerging threats across an organization.
4. IBM QRadar: Uncovers hidden anomalies in security logs.
5. Malwarebytes: Uses AI to detect and block advanced malware threats.
6. BinNet AI: Integrates with reverse engineering tools to analyze malware behavior.
7. FortiNDR: A network detection and response system that uses AI to detect and respond to.
Conclusion
In today's digital landscape, standing out as a cybersecurity company is no easy feat. With fierce competition and ever-evolving cyber threats, businesses need a robust strategy to attract qualified leads and build trust with potential clients. This comprehensive guide has explored the ins and outs of cybersecurity SEO, highlighting its importance and offering actionable strategies to enhance your online presence.
Key Takeaways:
1. SEO Fundamentals: Understanding and implementing SEO best practices is crucial for improving search engine rankings and driving organic traffic. From keyword research to on-page optimization, each step plays a vital role in making your website more visible.
2. Content is King: High-quality, relevant content is the cornerstone of successful SEO. By creating educational materials, real-world case studies, and engaging videos, you can demonstrate your expertise and build trust with your audience.
3. Technical SEO: Addressing technical issues such as site speed, mobile responsiveness, and structured data is essential for ensuring a seamless user experience and improving search engine rankings.
4. User Experience (UX): A user-friendly website with clear navigation, fast loading times, and engaging content not only enhances SEO but also boosts conversion rates.
5. AI in Cybersecurity SEO: Leveraging AI tools can significantly enhance threat detection, incident response, and content optimization. AI-driven solutions help you stay ahead of emerging threats and tailor your content to meet search engine algorithms and user intent.
6. Building Backlinks: High-quality backlinks from reputable sources signal to search engines that your content is trustworthy. Guest posting, creating valuable content, and distributing press releases are effective ways to build a strong backlink profile.
7. Measuring Performance: Regularly tracking key metrics such as organic traffic, keyword rankings, and conversion rates helps you identify what’s working and where adjustments are needed. Tools like Google Analytics, Ahrefs, and SEMrush provide valuable insights into your SEO performance.
8. Engaging Your Audience: Building a strong online presence through social media, webinars, and interactive content fosters engagement and drives traffic to your site. Staying active on platforms like LinkedIn and Twitter can help you connect with potential customers and establish your brand as an industry leader.
9. Local SEO: Optimizing for local searches can significantly boost your visibility in specific geographic areas. Claiming and maintaining your Google Business Profile, creating location-specific content, and encouraging customer reviews are effective local SEO strategies.
10. Continuous Improvement: SEO is an ongoing process that requires regular updates and adjustments. Staying informed about the latest trends and best practices ensures your strategy remains effective and relevant. By integrating these strategies into your cybersecurity marketing plan, you can enhance your online visibility, attract more qualified leads, and establish your company as a trusted authority in the cybersecurity industry.
Remember, the journey to SEO success may be challenging, but the rewards are well worth the effort. Stay committed, stay informed, and keep optimizing to achieve long-term success.