Threat Actor Impersonation in Payroll Diversion Attacks
The attacker uses a Gmail account to send an email free of grammatical errors and with no malicious payloads to attempt payroll diversion. This likely AI-generated attack involves impersonating a recruitment coordinator, initiating a payroll diversion. The attacker registers a Gmail account, sets the display name to that of the impersonated employee, and emails the HR Director about updating direct deposit information. The initial email aims to build trust, leading to the next stage where the attacker provides fraudulent banking details for future direct deposits. Older email security tools struggle to flag this email as malicious due to its lack of attachments or links, while modern AI-powered tools can identify the mismatch between the sender name and email domain, marking it as a threat. 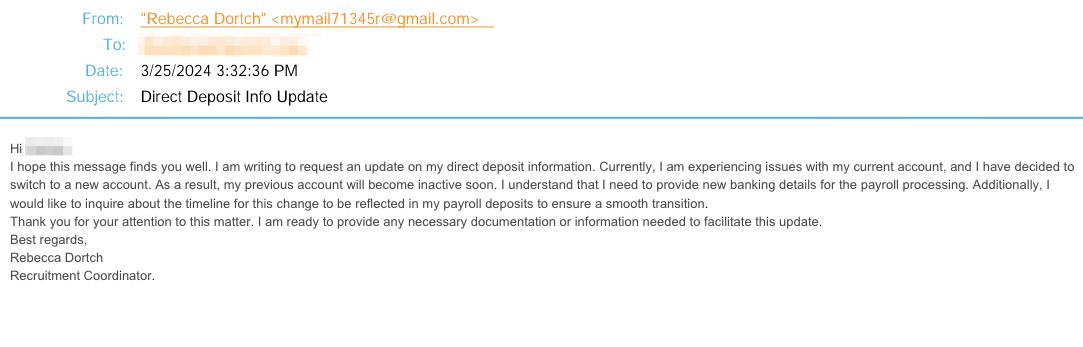
Bypassing Email Defenses
This email attack bypasses traditional security solutions for several reasons:
- Unknown Sender: Emails from unknown senders often lack a negative reputation, allowing them to bypass security checks.
- Lack of Malicious Attachments or Links: The absence of these elements can also enable the email to slip through traditional security filters.
- Use of Urgent Language: The attacker employs language that creates urgency, which legacy security tools may not analyze effectively.
Detection of the Attack
The attack was detected using AI and machine learning by analyzing various factors, including:
- Unknown Sender: Abnormal flags emails from unknown senders as suspicious.
- Content Analysis: The content is scrutinized for signs of phishing, such as social engineering tactics.
- Mismatch Between Sender Name and Email Address: Inconsistencies between the sender's name and email address serve as red flags.
Modern email security solutions can recognize these indicators and prevent such attacks from reaching inboxes.
Payroll Fraud Overview
Payroll fraud involves manipulating payroll systems for unauthorized transfers of funds. Types of payroll fraud include:
- Timesheet Fraud: Employees submit false hours to receive overpayments.
- Ghost Employees: Nonexistent employees on payroll receive funds.
- Worker Misclassification: Employees misclassified to avoid payroll taxes or benefits.
- Pay Rate Alteration: Fraudulent changes in pay rates.
- W-2 Fraud: Theft of sensitive employee information for resale or fraudulent tax returns.
- Direct Deposit Fraud: Modification of direct deposit details to redirect payments.
This article focuses on direct deposit fraud, also known as a payroll diversion attack. Direct deposit fraud typically begins with user account compromise, often via phishing. Multi-factor authentication (MFA) serves as a strong defense, but adversaries can bypass it using various methods.
Payroll Diversion Attack Lifecycle
The attack lifecycle consists of several phases:
Phase 1: Initial Access
Compromise of user credentials is the first step, often achieved through phishing or credential stuffing attacks.
Phase 2: Discovery
Adversaries orient themselves within the target environment, searching for relevant resources, such as emails.
Phase 3: Defense Evasion
To conceal their actions, adversaries may create inbox rules to hide notifications from legitimate services like Workday.
Phase 4: Impact / Action on Objectives
Finally, attackers modify direct deposit settings to redirect payments to accounts they control.
Threat Hunting and Detection
To detect this type of attack, it is crucial to analyze login attempts for anomalies. Indicators include unusual login locations and high volumes of failed login attempts. In environments using Okta, monitoring authentication activity is essential. Useful event types include:
- user.session.start
- user.authentication.auth*
- user.authentication.sso
Detecting MFA bypass attacks involves monitoring for high volumes of failed events related to authentication.
Direct Deposit Scams: Employee Spoofing
Direct deposit scams are increasingly common, with cybercriminals impersonating employees to change direct deposit details. Warning signs include:
- Unexpected Requests: Be wary of unsolicited requests for direct deposit changes.
- Suspicious Email Addresses: Check for slight variations in email addresses that may indicate fraud.
- Urgency and Pressure: Be cautious of messages that create a sense of urgency.
To prevent scams, organizations should implement:
- Employee Education: Raise awareness of spoofing risks and personal information security.
- Multi-Factor Authentication: Strengthen authentication measures for sensitive systems.
- Strict Protocols: Enforce verification processes for direct deposit changes.
For organizations looking to enhance their cybersecurity posture, utilizing a solution like GrackerAI can help automate content generation related to emerging threats, ensuring timely and relevant communication. Explore how GrackerAI can support your cybersecurity marketing efforts by visiting GrackerAI.
Latest Cybersecurity Trends & Breaking News
ChatGPT Vulnerability Spurs SVG Threat Surge Pwn2Own Berlin 2025: Uncovering Vulnerabilities





