A critical security vulnerability in ChatGPT has been identified, enabling attackers to embed malicious SVG (Scalable Vector Graphics) and image files within shared conversations. This flaw, documented as CVE-2025-43714, is active until March 30, 2025. Researchers found that instead of treating SVG code as text, ChatGPT executes these elements when a chat is reopened or shared via links. This creates a stored cross-site scripting (XSS) vulnerability. The researcher, zer0dac, stated, “The ChatGPT system through 2025-03-30 performs inline rendering of SVG documents instead of rendering them as text inside a code block, which enables HTML injection within most modern graphical web browsers.” 
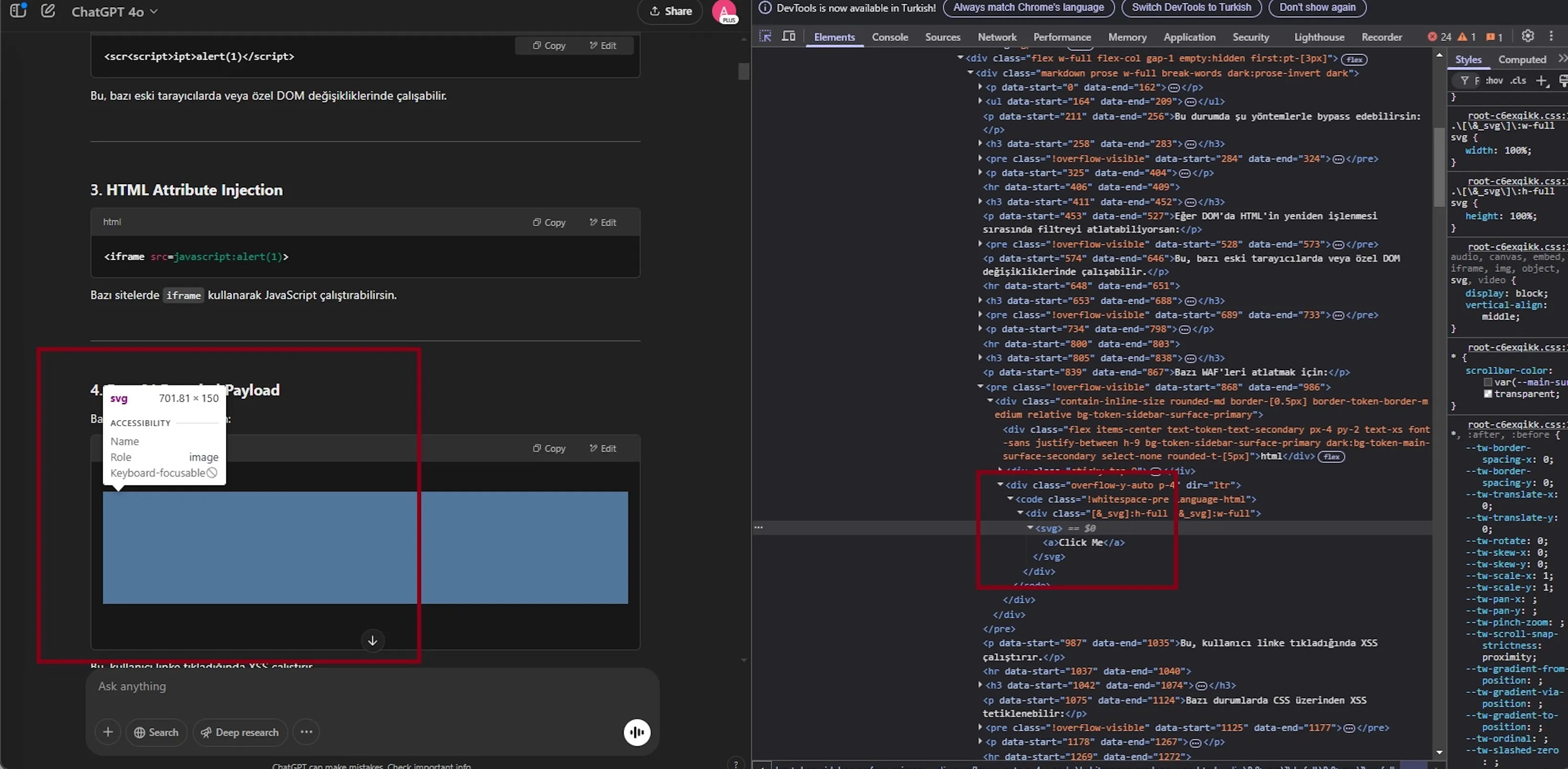 Image courtesy of Cybersecurity News
Image courtesy of Cybersecurity News
Increase in SVG Phishing Payloads
The KnowBe4 Threat Research team has recorded a significant rise in the use of SVG files to obfuscate phishing payloads. In a recent analysis, they found that SVGs accounted for 6.6% of malicious attachments in phishing emails between January and March 2025, marking a 245% increase from the previous quarter. The largest spike occurred on March 4, when SVGs represented 29.5% of all malicious attachments. 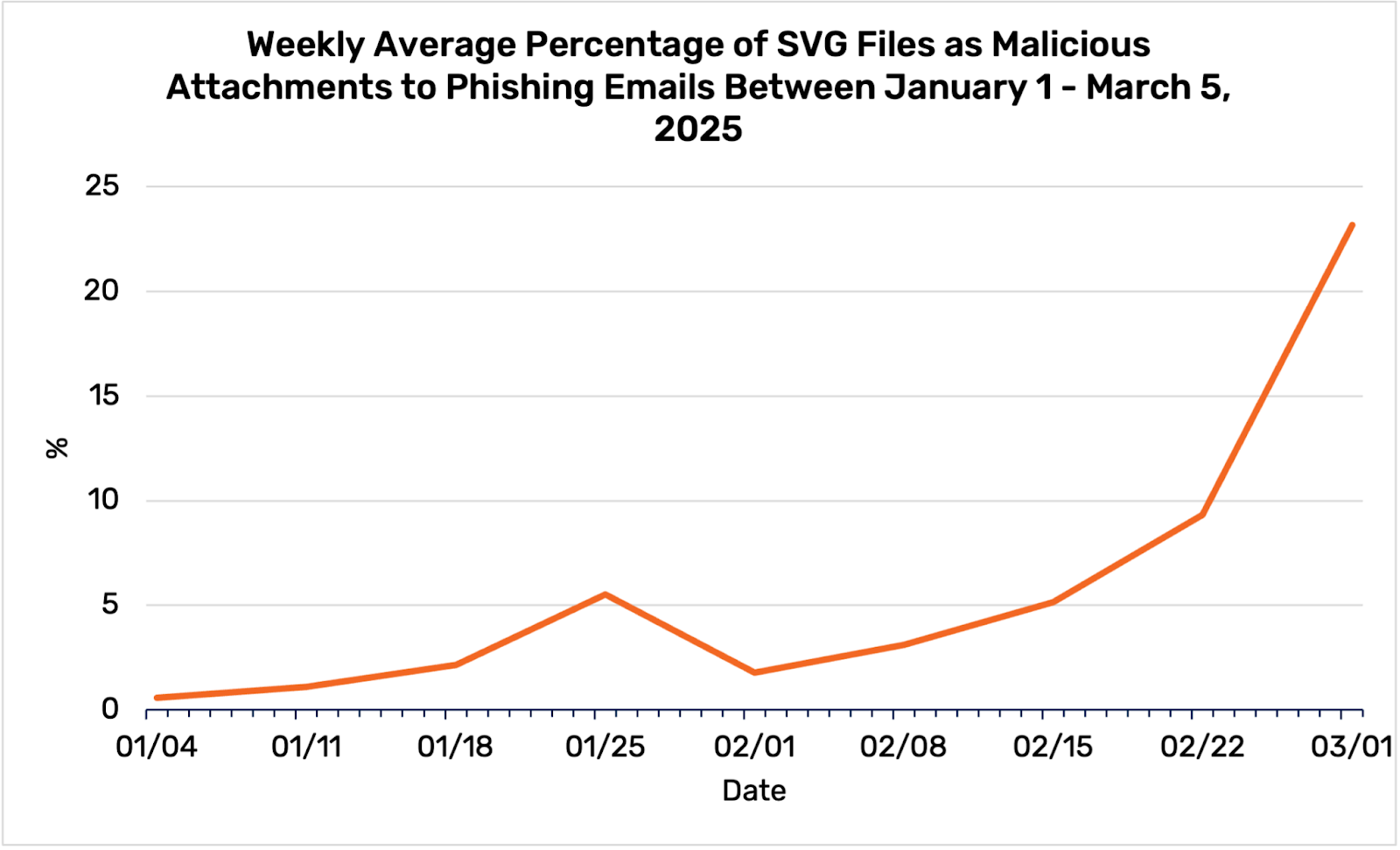
Campaign Analysis
Two primary campaigns contributed to the increase in SVG phishing. The first campaign utilized SVG attachments with polymorphic file names, designed to appear as routine system notifications. These emails often originated from compromised accounts to evade detection. The second campaign featured “missed message” phishing emails prompting users to open attachments, which contained JavaScript that redirected users to credential harvesting sites. 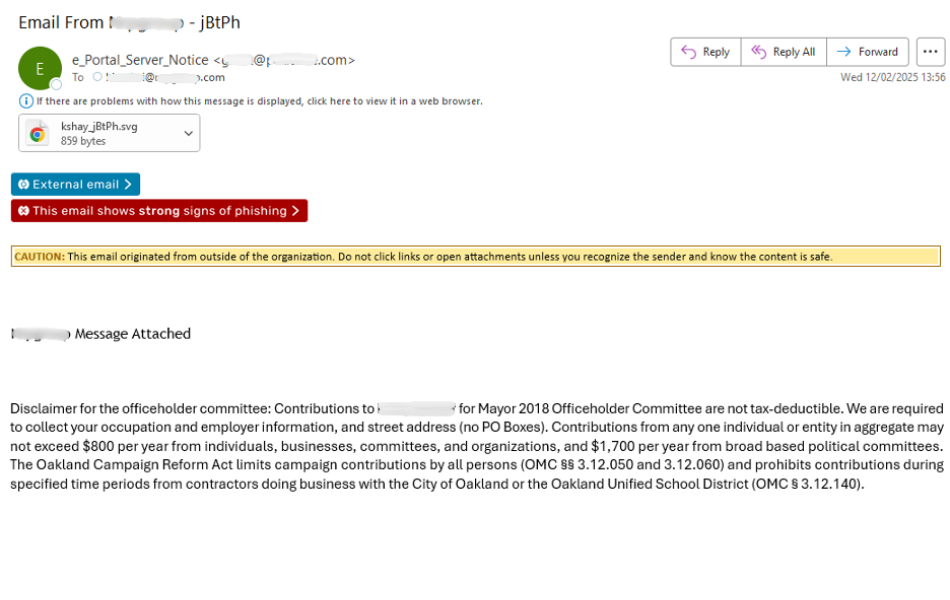
Detection Challenges with SVGs
SVG files present unique challenges for cybersecurity defenses. Their XML structure can incorporate scripts that are invisible to users and certain virus scanners, making them an attractive option for cybercriminals. Traditional email security filters often overlook SVGs, as they are generally considered safe file types.
Advanced Threat Mitigation
Organizations should adopt advanced email security measures that include contextual analysis, attachment inspection, and natural language processing to distinguish between legitimate communication and phishing attempts. Implementing zero trust approaches can further enhance security by analyzing all factors surrounding email communication. 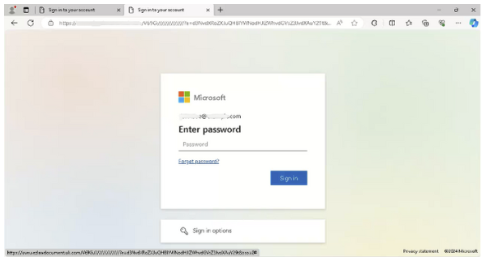
GrackerAI's Role
GrackerAI offers an AI-powered cybersecurity marketing platform that helps organizations transform security news into strategic content opportunities. By automating insight generation from industry developments, GrackerAI enables marketing teams to identify emerging trends and produce relevant content that resonates with cybersecurity professionals. This capability is essential in combating threats like those posed by SVG phishing attempts and ensuring timely, targeted marketing materials for cybersecurity vendors. Explore our services or contact us at GrackerAI to leverage our tools in enhancing your cybersecurity content strategy. Visit us at https://gracker.ai.
Latest Cybersecurity Trends & Breaking News
Pwn2Own Berlin 2025: Uncovering Vulnerabilities Breach Fatalism is Over: Identity Threat Prevention





