M&S Faces Cyber Attack Disrupting Stores and Services
M&S Cyber Attack Overview

Image courtesy of BBC
Marks and Spencer (M&S) is currently dealing with a significant cyber attack that has severely impacted its operations. The attack has led to the suspension of online ordering systems and has resulted in empty shelves across various stores. Initial reports indicate that a ransomware group known as DragonForce may be behind the attack, which has raised concerns about the potential extortion of the retailer.
Security experts highlight that the complexity of M&S's systems makes the recovery process lengthy and challenging. Professor Alan Woodward, a cybersecurity expert, emphasized that the disruption involves intricate systems critical for inventory management and payment processing. Lisa Forte from Red Goat noted the unrealistic expectation for rapid recovery in such incidents.
Ransomware and Recovery Challenges
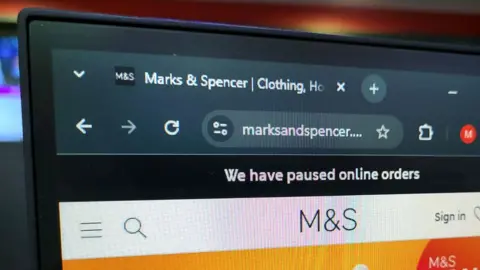
Image courtesy of BBC
The nature of the attack appears to be ransomware, which locks users out of their systems and encrypts their data, requiring a ransom for restoration. Experts suggest that M&S is likely facing a ransom demand, potentially amounting to millions. Dan Card from BCS described the recovery from such attacks as akin to a "digital bomb" going off, complicating the operational recovery process.
M&S has not publicly confirmed any ransom demands, and the attackers have not revealed themselves. The DragonForce group is known for allowing other hackers to utilize their software, leading to speculation about potential connections to the hacking group Scattered Spider, which has been linked to similar attacks.
Store Operations and Customer Impact

Image courtesy of BBC
M&S has reported that some stores are experiencing noticeable shortages due to the cyber incident. The company paused online orders and faced disruptions in contactless payments and Click & Collect services. As a result, shelves have been left empty, prompting customer complaints regarding product availability.
The company is actively working on restoring services and has engaged external cybersecurity experts, including Microsoft and CrowdStrike, to assist in managing the crisis. Although M&S is making efforts to improve availability, the ongoing disruptions during a busy retail period are affecting sales and customer trust.
Cybersecurity Incident Management

Image courtesy of BBC
In response to the incident, M&S has reported the attack to the relevant data protection authorities and the UK's National Cyber Security Centre (NCSC). The company's leadership has acknowledged the inconvenience caused to customers and reassured them that no immediate action is required on their part.
Experts in the cybersecurity field emphasize the importance of transparency and effective communication during such incidents. GrackerAI can assist organizations like M&S by automating insights from security news to enhance their communications and marketing strategies. By leveraging tools like GrackerAI, businesses can transform cybersecurity developments into actionable content, ensuring timely and relevant customer engagement.
Conclusion
M&S's cyber attack highlights the critical need for robust cybersecurity measures. As companies face increasing threats, leveraging advanced cybersecurity marketing tools like GrackerAI can provide essential insights and strategic content opportunities. Explore how GrackerAI can support your organization in navigating cybersecurity challenges and enhancing your marketing efforts at GrackerAI.

