Introduction: Why CISOs Are the Hardest Audience to Reach (and How to Fix It)
Reaching a Chief Information Security Officer (CISO) through cold email is a challenge many cybersecurity marketers face.
CISOs manage complex security environments and make critical decisions daily. Their time is limited, and they are selective about the conversations they engage in. Over 80% of cold emails to CISOs go unanswered, not because your solution isn't valuable, but because your approach lacks relevance, urgency, and empathy.
According to LinkedIn, B2B campaigns targeting IT decision-makers achieve up to 2x higher engagement rates when messaging is highly relevant.
This means that with the right approach, cold emails to CISOs can be successful — if they are strategic, personalized, and genuinely valuable.This guide explains how to write cold emails that CISOs are more likely to open, read, and respond to — based on real-world research, cybersecurity industry best practices, and actionable examples.
Understanding What CISOs Worry About
To write good cold emails, you need to know what CISOs care about.
Things That Bother All CISOs
- Regulations: They have to follow rules like GDPR, CCPA, SOC-2, and others that keep changing.
- Vendor Risks: They worry about problems from the tools and services they use from other companies.
- New Threats: They need to stay ahead of new dangers that hackers might use. One of the most effective ways they do this is through proactive threat intelligence — continuously tracking emerging attack patterns to inform better defense strategies.
- Money: They have to show that spending on security is worth it.
- Too Many Alerts: They get lots of warnings from security tools, but not all are useful.
Why CISOs Often Ignore Cold Emails
- Volume: CISOs receive a high number of outreach emails daily.
- Skepticism: They are cautious about vendors making broad promises.
- Relevance: Emails that feel generic or sales-focused rarely earn attention.
- Ignoring Timing: Failing to align with current events (e.g., Log4j, ransomware trends).
- No Proof of Expertise: Missing trust signals like case studies or threat intelligence.
Common issues in cold emails include:
- Leading with product features instead of addressing real security concerns
- Asking for meetings without offering any immediate value
- Overloading the message with technical jargon or broad claims
What CISOs Prioritize When Responding
Before writing to a CISO, it is important to understand their priorities:
- ✅ Reducing Security Risk: They want solutions that help prevent, detect, or respond to threats.
- ✅ Regulatory Compliance: SOC 2, HIPAA, GDPR, and other frameworks drive their priorities.
- ✅ Operational Efficiency: Improving team productivity without adding complexity.
- ✅ Peer Validation: Knowing that respected companies trust a solution matters. Understanding how CISOs evaluate tools and vendors can make your message more relevant from the first line. If you haven't already, check out our guide on how CISOs select cybersecurity vendors in 2026. it maps their decision-making process step by step
- ✅ Strategic Advantage: Solutions that offer better resilience, faster detection, or cost savings.
A Proven Structure for Cold Emails to CISOs
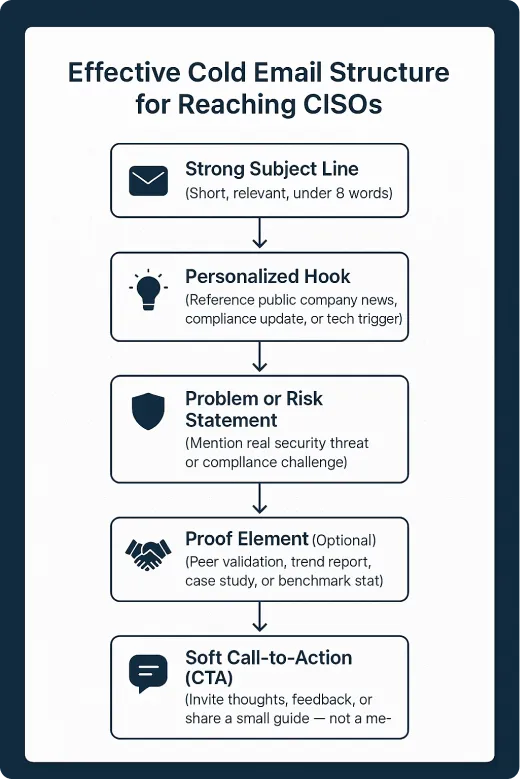
- Subject Line: Relevant, short, and specific (under 8 words)
- Personalized Opening: Reference a public fact about their company, stack, or initiatives
- Problem or Risk Insight: Focus on the security challenges they might be facing
- Social Proof (optional): Mention peer companies or certifications
- Soft CTA: Invite their thoughts, not their time
9 Best Practices for Cold Emailing CISOs
Here's how to write a good cold email to a CISO:
1. Focus on Risk, Not Features
Start by identifying a risk or emerging threat relevant to their environment.
Example:
"New phishing tactics are bypassing MFA. Is this an area of concern for [Company]?"
2. Subject Line: Get Their Attention in 8 Words
- Not Good: “Transform Your Cybersecurity Strategy”
- Good: “Reducing Alert Fatigue for [Industry] Teams”
- Even Better: “How [Similar Company] Cut False Positives by 70%”
- Tip: Use words that make them curious or feel they need to act quickly. For example: “Quick Question About [Specific Problem].”
3. Opening Line: Show You Know Who They Are
- Not Good: “I'm reaching out because…”
- Good: “I saw your blog on cloud security gaps - we can help with AWS issues.”
- Even Better: “After the [Industry] breach last week, I thought you'd want to know how [Client] fixed similar problems in less than 48 hours.”
- Tip: Mention something they posted or a connection you both have.
4. Body: Talk About Results, Not Features
- Not Good: “Our platform offers real-time threat detection.”
- Good: “We help CISOs like [Name] at [Company] cut incident response time by 60% without hiring more people.”
5. Use the “30-30-50 Rule”:
- 30% Personalization: Mention their job, company, or something recent. For example, if they recently switched to AWS, highlight your cloud security experience.
- 30% Value: Highlight a specific benefit. For example, “We helped reduce SOC 2 audit prep time by 40%.”
- 50% Credibility: Add proof, like “Used by Fortune 500 teams.”
6. CTA: Make It Easy to Reply
- Not Good: “Let's schedule a demo.”
- Good: “Here's a 3-minute case study on [Relevant Challenge]. Want the link?”
- Even Better: “Is dealing with false positives a top priority for your team this quarter?”
Need help drafting personalized outreach fast? You can try this free AI-powered email writer for cold outreach — it's built to help you create clear, relevant messages without sounding robotic.
7. Research Deeply: Know Their Stack & Compliance Challenges
- Use tools like LinkedIn Sales Navigator, Hunter.io, or Crunchbase to find out:
- What tools do they use (e.g., SIEM, SIEM-as-a-Service)?
- Recent compliance audits (SOC 2, GDPR).
- Industry-specific risks (e.g., healthcare: HIPAA; finance: PCI DSS).
- Example: If a CISO recently transitioned to AWS, highlight your experience with cloud security.
8. Optimize for Mobile & Timing
Mobile-First: 60% of professionals check emails on mobile. Keep lines short (<50 characters)
Timing
- 📅 Best Days: Tuesday to Thursday
- 🕒 Best Times: Between 7:30-9:00 AM or 6:30-8:00 PM (local time of recipient)
9. Plan Thoughtful Follow-ups
Best practice cold email sequence:
- Day 1: Introduction + insight
- Day 3: Follow-up with resource (e.g., case study, checklist)
- Day 7: Reminder email offering further value
- Day 14: Final nudge with a new insight
Avoid generic phrases like “just checking in.” Instead, continue adding value in each touch.
Real Examples: Effective Cold Emails to CISOs
Risk-Focused Email
Subject:
Reducing incident response gaps — quick thought
Body:
Hi [Name],
With ransomware incidents increasing across [industry], we're helping teams strengthen their detection and response workflows without overloading their analysts.
I shared a short guide here: [link].
Would love to hear if this is a current priority for your team.
Best regards,
[Your Name]
Compliance-Focused Email
Subject:
SOC 2 Trust Services changes — impact on audits
Body:
Hi [Name],
Congratulations on [Company]'s recent SOC 2 certification.
Upcoming changes to Trust Services Criteria for 2026 could affect future renewals.
Summarized key changes here: [link]. Curious if this is something your team is already planning for.
Thanks,
[Your Name]
Risk-Based Trigger Example (Post-Breach Outreach)
Subject:
Helping teams strengthen defenses post-Okta incident
Email Body:
Hi [Name],
Following the recent breach at Okta, several of our partners are reviewing third-party authentication risks.
We developed a short guide on mitigation steps based on the latest breach patterns: [link].
Curious if this aligns with initiatives [Company] is prioritizing this quarter.
Best regards,
[Your Name]
Peer Validation Example (Social Proof)
Subject:
How [Peer Company] improved security audit prep
Email Body:
Hi [Name],
Noticed [Company] is growing rapidly — congrats.
We recently worked with [Peer Company] to streamline evidence gathering for their SOC 2 and ISO 27001 renewals, cutting prep time by 35%.
Wrote a brief case study here: [link].
Would be great to hear if audit optimization is a current priority for your team, too.
Thanks,
[Your Name]
Compliance Insight Example (Upcoming Regulatory Change)
Subject:
New GDPR fines trend: Quick overview for security leaders
Email Body:
Hi [Name],
With GDPR enforcement actions increasing 28% year-over-year (source: DLA Piper report), security teams are revisiting their data retention policies.
If you're evaluating similar updates at [Company], I created a short breakdown on key trends: [link].
Happy to share additional benchmarks if helpful.
Best regards,
[Your Name]
Soft Product Introduction (without Pitching)
Subject:
Reducing threat detection time without expanding headcount
Email Body:
Hi [Name],
Given today's resource constraints, several cybersecurity teams have shifted toward lightweight automation to shorten response times without scaling their analyst teams.
I compiled a quick checklist of initiatives that are working across mid-market tech firms: [link].
Would love your thoughts based on [Company]'s current roadmap.
Thanks,
[Your Name]
Bonus Tip (for even higher value):
At the bottom of these emails, instead of "just asking" for meetings,
You could add a small micro-commitment like:
"If you'd like, I can send a 2-minute checklist based on your current tech stack — no strings attached."
It feels much more natural and peer-like, and builds early-stage trust.
If you're looking to explore more variations of these frameworks, we've compiled a full set of cold email templates for cybersecurity marketers, tailored specifically for outreach to CISOs, CIOs, and other security leaders.
Mini Email Teardown: Before vs After (What Not to Send… and What Works)
Here's a cold email teardown to make this guide even more practical. Let's take a typical “bad” outreach email to a CISO — and rework it using our proven 5-step framework.
❌ Before: Weak, Salesy Cold Email
Subject:
Improve Your Security Posture with [Product Name]
Hi [Name],
I'm with [Company], a leading provider of cybersecurity solutions. We help organizations like yours improve endpoint protection, automate risk assessments, and gain better visibility.
Are you available for a quick 15-minute call this week?
Best regards,
[Rep Name]
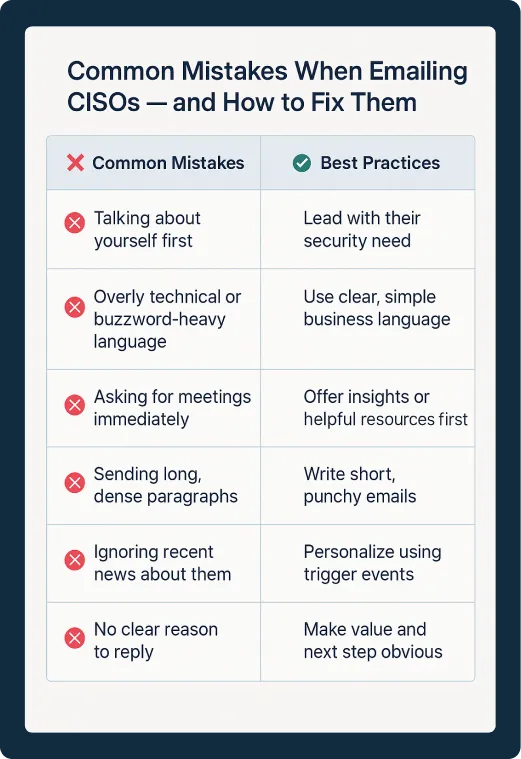
What's wrong:
- Generic subject line (vague + unremarkable)
- Self-centered intro (talks about the sender, not the recipient)
- No understanding of CISO-specific concerns
- Pushy call-to-action without context or value
✅ After: Value-Focused, Personalized Cold Email
Subject:
Reducing alert fatigue at scale — quick insight
Hi [Name],
I saw [Company] recently expanded cloud workloads — congrats. Teams in [Industry] now deal with increased alert fatigue and longer MTTR.
We just helped [Peer Company] cut false positives by 65% without adding analyst overhead.
I wrote a short breakdown on the approach — happy to send it if useful.
Cheers,
[Rep Name]
Why it works:
- Personalized subject and opening
- References a real pain point (alert fatigue)
- Offers social proof (peer validation)
- Ends with a low-friction CTA — doesn't push for a meeting
Common Mistakes to Avoid
Frequently Asked Questions
1. How do I get more responses from cold emails?
Personalize every email, lead with risk insights, and always offer value before asking for a meeting.
2. What is the 30 30 50 rule for cold emails?
It's a cold email metric rule — aim for 30% opens, 30% clicks, and 50% replies of clicked leads. In cybersecurity, response rates are lower, and a 10-15% reply is considered strong.
3. Why is there no response to my cold email?
Common reasons include lack of relevance, unclear value proposition, poor timing, or overly sales-driven messaging.
4. How to win at cold emails?
Focus on education and relevance. Think of cold emails as conversations, not sales pitches.
Conclusion
Winning a CISO's attention through cold email is not about clever tricks or aggressive sales pitches.It is about understanding their world, their risks, and their goals — and showing that you can help, without overwhelming or distracting them.
When you lead with real insights, speak with respect, and deliver genuine value, you build the foundation for trust. And trust is the key to starting meaningful conversations with today's security leaders