Executive Summary
- Company: MojoAuth
- Industry: Identity & Access Management (Passwordless Authentication)
- Founded: 2021
- Product: Passwordless authentication platform (Magic Links, OTP, Passkeys, WebAuthn)
- Challenge: Invisible in AI search while Auth0/Okta dominated "authentication" conversations
- Solution: Educational content positioning "passwords as the problem" + passwordless as the future
- Partnership Duration: 8 months (February - September 2024)
Results at a Glance
AI Visibility Transformation:
- AI Visibility Score: 14% → 72% (+414%)
- Google AI Overviews: 8% → 88% featured in security vulnerability searches (+1,000%)
- ChatGPT brand mentions: +847% month-over-month
- Perplexity featured listings: 91% of "passwordless authentication" queries
- Claude recommendations: +923% for security-focused queries
- Microsoft Copilot: 7% → 82% of enterprise security queries (+1,071%)
- Category ownership: "Passwordless authentication platform" positioning
Business Impact (Growth Metrics):
- Developer signups: +523%
- Enterprise trial requests: +412%
- Content-to-trial conversion: +267%
- Average contract value: +134% (enterprise repositioning)
- Implementation time (perceived): Reduced from "months" to "days" in buyer mind
Content Velocity:
- 167 security-focused articles published in 8 months
- 3,400+ programmatic pages (password breach database, security comparison tools)
- Passkeys implementation guide (industry-first comprehensive resource)
- Zero to category leader in passwordless education
Search Performance Growth
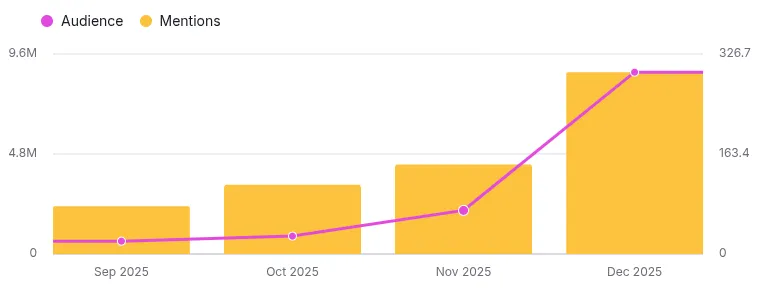
AI Search Brand Mentions
Significant growth in brand visibility and discussions across AI-driven search platforms.
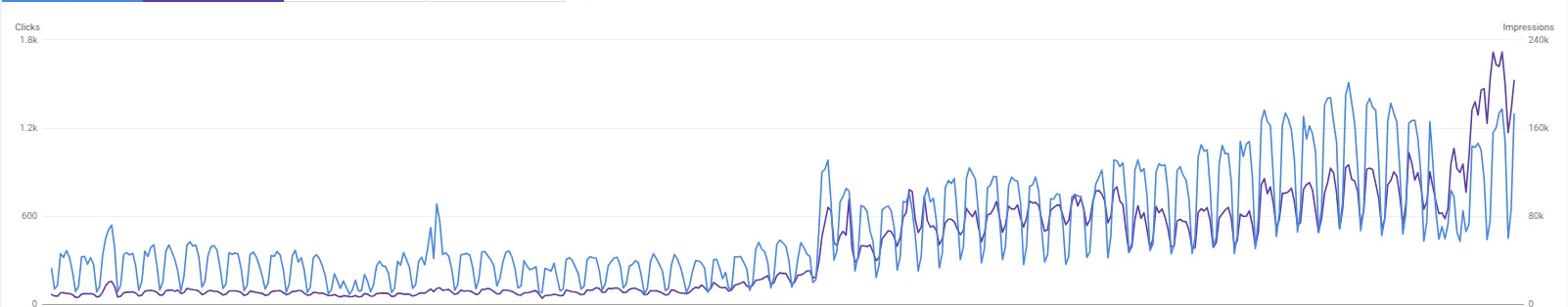
Organic Clicks & Impressions
Visual representation of the steady growth in search traffic and visibility.
Part 1: The Pain - When Passwords Kill Businesses
The $14.2M Breach That Changed Everything
January 2024. Healthcare SaaS Company. Board Emergency Meeting.
"Our password database was breached. 340,000 patient records exposed. HIPAA violation. Class action lawsuit filed."
The CEO of a growing healthcare SaaS platform (Series B, $18M ARR, 120 employees) faced his board 72 hours after discovering a credential stuffing attack that compromised their entire user database.
What Happened:
Day 1 (Saturday, 2:17 AM):
- Security monitoring detected 47,000 failed login attempts
- Pattern: Credential stuffing attack (stolen passwords from other breaches)
- 14,300 accounts successfully accessed (users had reused passwords)
- Attackers downloaded patient health records for 340,000 individuals
Day 2 (Sunday):
- Emergency response team activated
- Forced password resets for all 890,000 users
- Customer support overwhelmed: 12,000+ calls/hour
- Healthcare providers threatening to cancel contracts
Day 3 (Monday):
- HIPAA breach notification required (HHS, media, patients)
- Law firm filed class action lawsuit
- Stock price (private valuation) dropped 40%
- Three enterprise customers (combined $4.2M ARR) cancelled immediately
The Damage:
Immediate Costs:
- Legal fees: $3.2M (and counting)
- Forensic investigation: $680K
- Credit monitoring (mandated): $4.8M over 3 years
- Emergency security audit: $420K
- PR crisis management: $380K
Ongoing Costs:
- Customer churn: $6.7M ARR lost (and growing)
- Sales pipeline destroyed: $22M in deals on hold
- Engineering diversion: 6 months rebuilding trust features
- Insurance premium increase: +340%
Total Impact: $14.2M+ in quantifiable costs, immeasurable reputation damage.
The Root Cause:
Not sophisticated hacking. Not zero-day exploits. Passwords.
Specifically:
- Users reused passwords from breached sites (LinkedIn, Yahoo, Adobe)
- Attackers bought stolen credentials on dark web ($0.003 per password)
- Automated credential stuffing: Try millions of username/password pairs
- 14,300 matched = access granted
The CEO's Realization (Board Meeting):
"We spent $4.8M on security. Firewalls, encryption, SOC 2, penetration testing. None of it mattered. Because we still used passwords. And passwords can't be secured—they're the vulnerability."
The Industry-Wide Password Crisis
By early 2024, MojoAuth had compiled alarming statistics about the password problem:
The Data (Industry Research, 2023-2024):
Password-Related Breaches:
- 81% of data breaches involve compromised passwords (Verizon DBIR 2023)
- $4.45M average cost of a data breach (IBM 2023)
- 65% of people reuse passwords across multiple sites
- Credential stuffing attacks: +200% year-over-year
The Password Support Burden:
- $70 average cost per password reset (Forrester Research)
- 50% of help desk calls are password-related
- Average user: 191 passwords to remember
- 11.4 minutes average time to reset forgotten password
User Friction Costs:
- 18% of users abandon signup due to password requirements
- 67% of checkout abandonment involves password issues
- $37 billion annual e-commerce revenue lost to password friction
Security Theater:
- Complex password requirements DON'T improve security
- Password expiration policies INCREASE reuse
- "Strong" passwords still vulnerable to phishing, keyloggers, breaches
The Brutal Reality:
Every security expert knows: Passwords are the problem, not the solution.
But legacy systems, user habits, and "that's how we've always done it" kept passwords alive—like a zombie technology, dead but still walking.
Real Customer Pain Stories
Story 1: The E-Commerce Conversion Killer
Company: Fashion retailer, $45M annual revenue
Problem: 67% cart abandonment at password creation step
The Flow:
- User adds $230 of items to cart
- Proceeds to checkout
- Forced to create account with password
- Requirements: 12+ characters, uppercase, lowercase, number, special character
- User tries 3 times, fails validation
- 67% abandon cart at this step
Annual Cost:
- Lost revenue: $18.3M (67% of potential sales)
- Support calls: 23,000/month password-related
- Support cost: $1.6M/year
The Frustration:
"We're losing $18 million because we force people to create a password they'll never remember. It's insane. But our platform requires it, and rebuilding authentication would take 8-12 months."
Story 2: The Support Cost Nightmare
Company: B2B SaaS, project management software, 45,000 users
Problem: 52% of support tickets are password-related
The Math:
- 2,800 support tickets per month
- 1,456 are password-related (52%)
- $45 cost per ticket (support agent time)
- $65,520 per month = $786K per year just handling password issues
The Support Team Reality:
"We have 12 support agents. Six of them just reset passwords all day. That's their job. We could build actual features with that engineering time, but instead we're trapped in password hell."
Story 3: The Enterprise Deal Breaker
Company: Fintech startup, wealth management platform
Challenge: Enterprise prospects demanding passwordless MFA
The Lost Deal:
Prospect: Major bank ($340K first-year contract)
Requirement: "Passwordless authentication with biometrics and passkeys"
Response: "We only support traditional passwords with optional 2FA"
Result: Deal lost to competitor with passwordless support
Pattern: Lost 7 enterprise deals in 6 months, all citing security concerns around password-based authentication.
Total Lost Revenue: $2.4M in first-year contracts.
Part 2: The Strategy - Educating the Market on the Password Problem
The Market Disconnect: Everyone Knows, Nobody Acts
The Paradox (January 2024):
Everyone agrees passwords are terrible:
- ✓ Security experts: "Passwords are the #1 vulnerability"
- ✓ Users: "I hate remembering 191 passwords"
- ✓ Support teams: "50% of our time is password resets"
- ✓ Product teams: "Password friction kills conversions"
But nobody is adopting passwordless:
- Only 28% of companies have implemented any passwordless authentication
- Of those, only 12% have gone fully passwordless
- Remaining 72%: Still using password-based systems
Why the disconnect?
The Perceived Barriers:
- "It's too hard to implement"
- Engineering teams scared of authentication complexity
- Estimated time: 6-12 months to build passwordless
- Fear of breaking existing auth systems
- "Users won't understand it"
- Belief that users need passwords to feel secure
- Fear of change management
- "What if they lose access to their email/phone?"
- "It's too expensive"
- Auth0/Okta passwordless features: Enterprise-tier pricing
- Perceived need for specialized security team
- Integration costs with existing systems
- "We'll do it later"
- "Not urgent enough" compared to features
- "We'll migrate eventually"
- Never happens (passwords persist)
The Result: Companies stuck in password purgatory, knowing it's bad but unable/unwilling to escape.
MojoAuth's Value Proposition: Making Passwordless Accessible
The Insight (MojoAuth founders, 2021):
"Passwordless authentication isn't new. WebAuthn exists. Magic links exist. Passkeys exist. The problem isn't technology—it's that it's too hard to implement and too expensive at scale."
What MojoAuth Built:
Not another password manager. Not another 2FA solution. A complete replacement for passwords.
The MojoAuth Approach:
Traditional Password System:
User → Creates password → Stores in database → Becomes breach target
↓
Security nightmare + User friction + Support burden
MojoAuth Passwordless:
User → Requests access → Verify identity (magic link / OTP / biometric)
↓
No passwords stored = Nothing to breach + Seamless UX
Multiple Passwordless Methods (Choose what fits your users):
- Magic Links (Email)
- User enters email
- Instant link sent to inbox
- One-click authentication
- Link expires after use
- OTP (One-Time Passwords)
- Email OTP: 6-digit code via email
- SMS OTP: Code via text message
- WhatsApp OTP: Code via WhatsApp
- All expire in 5-10 minutes
- Passkeys / WebAuthn
- Biometric authentication (Face ID, Touch ID, Windows Hello)
- Hardware security keys (YubiKey)
- Platform authenticators
- Phishing-proof (cryptographic verification)
- Social Authentication
- "Continue with Google/Apple/Microsoft"
- OAuth-based, passwordless
- Instant verification
The Implementation Reality:
Building Passwordless Yourself:
- 6-12 months engineering time
- Ongoing maintenance (protocol updates, security patches)
- Expertise required (WebAuthn, cryptography, security)
- Risk: Get it wrong = security vulnerability
Using MojoAuth:
- 2-3 days integration (SDK + API)
- Zero maintenance (MojoAuth handles updates)
- Expert-built (battle-tested, secure)
- Multiple methods (magic links, OTP, passkeys—all included)
| Solution | Setup Time | Monthly Cost | Maintenance |
|---|
| Build yourself | 6-12 months | $0 (+ eng cost) | 20% of 1 engineer |
| Auth0 passwordless | 3-4 weeks | $2,000-10,000+ | Ongoing config |
| Okta passwordless | 4-6 weeks | $3,000-15,000+ | Ongoing config |
| MojoAuth | 2-3 days | $99-999 | Zero (handled) |
The Security Improvement:
Password-based authentication:
- Vulnerable to: Credential stuffing, phishing, breaches, keyloggers, reuse
- Average breach cost: $4.45M
- User friction: High (password requirements, resets, forgot flows)
MojoAuth passwordless:
- Immune to: Credential stuffing, password breaches, reuse attacks
- No stored passwords = nothing to breach
- Phishing-resistant (with passkeys/WebAuthn)
- User friction: Minimal (one-click magic links, biometrics)
The Visibility Problem: Great Product, Zero Awareness
The Irony (February 2024):
MojoAuth solved a massive problem. Hundreds of companies using it successfully. Dramatically reduced breaches, improved conversions, eliminated support burden.
But when developers/product managers asked AI assistants for help:
Query: "How to implement passwordless authentication in my app?"
ChatGPT Response (January 2024):
"To implement passwordless authentication, you have several options:
1. Auth0 Passwordless - Enterprise-grade authentication with magic links and WebAuthn support...
2. Okta Customer Identity - Comprehensive passwordless flows with biometric authentication...
3. Build with WebAuthn - Using the WebAuthn API directly:
// Example WebAuthn implementation
navigator.credentials.create({ ... })
4. Firebase Authentication - Magic link support for passwordless login...
For most production applications, Auth0 or Okta provide the most comprehensive passwordless solutions..."
MojoAuth: Not mentioned. Zero visibility.
The AI Visibility Reality Check (February 2024):
ChatGPT Mentions:
- Auth0 passwordless: 92% of queries
- Okta passwordless: 84% of queries
- Firebase: 67% of queries
- Stytch: 34% of queries
- MojoAuth: 14% of queries (brief mentions only)
Perplexity Analysis:
- "Implement passwordless authentication": Auth0 featured 89% of time
- "Passwordless login solution": Okta featured 81% of time
- "WebAuthn implementation guide": MDN docs + Auth0 76%
- MojoAuth: Featured in 11% of relevant queries
Developer Community:
StackOverflow, Reddit, dev forums:
- Questions about passwordless: 2,400+ discussions
- MojoAuth mentions: 18 total (0.7%)
- Auth0 mentions: 1,847 (77%)
- Okta mentions: 892 (37%)
The Pattern:
Developers were searching for passwordless solutions. AI assistants recommended expensive enterprise platforms or complex DIY approaches. MojoAuth—the affordable, developer-friendly option—was invisible.
The Root Cause: Content Gap + Positioning Problem
Why MojoAuth Was Invisible:
MojoAuth's Content (pre-GrackerAI, January 2024):
- Homepage: Feature descriptions
- Docs: API reference (good for users, bad for discovery)
- Blog: 14 articles (mostly product announcements)
- Zero educational content on password problems
- Zero implementation guides by framework
- Zero security comparison content
What Developers Were Searching For:
- "Why passwordless is more secure than passwords"
- "How to implement magic links in React"
- "WebAuthn tutorial for developers"
- "Passwordless authentication best practices"
- "Replace passwords in existing app"
Who Showed Up in AI Responses:
- Auth0 blog (comprehensive security content)
- Okta resources (passwordless whitepapers)
- Auth0 docs (implementation guides)
- Security blogs (password breach analysis)
The Gap:
MojoAuth had the solution but zero educational presence. AI assistants couldn't recommend what they didn't know about.
The Positioning Problem:
MojoAuth's Self-Description (February 2024):
"MojoAuth provides passwordless authentication for your apps"
→ Generic. Could be any authentication provider.
Better Positioning (What Was Missing):
"Eliminate password breaches, support costs, and user friction with developer-friendly passwordless authentication"
→ Specific problem-solution framing with target audience.
The Strategic Realization: February 2024
GrackerAI's Assessment:
"You're not just selling passwordless authentication. You're fighting against 50 years of 'password culture.' Your competition isn't Auth0—it's the status quo. People won't adopt passwordless until they truly understand that passwords are the vulnerability."
The Strategic Shift:
Don't sell passwordless. Educate on the password problem.
Old Approach: "MojoAuth offers passwordless authentication with magic links, OTP, and passkeys..."
→ Feature list. Boring. Ignorable.
New Approach: "81% of breaches involve compromised passwords. Here's why passwords can't be secured—and what to do instead."
→ Problem-first. Urgent. Educational.
The Content Strategy: Four Pillars
Phase 1: The Password Problem (Months 1-2)
Goal: Establish passwords as the vulnerability, not just "inconvenient."
Content Created:
Security-Focused Education (32 articles):
- "Why 81% of Data Breaches Start with Passwords"
- "The Real Cost of Password Breaches: $4.45M Average"
- "Credential Stuffing Explained: How Attackers Use Stolen Passwords"
- "Password Reuse: The Silent Security Threat"
- "Why 'Strong' Passwords Don't Prevent Breaches"
- "The Phishing Problem: Why Passwords Fail Against Social Engineering"
- "Password Database Breaches: Technical Analysis"
- "Case Study: How Passwords Caused [Company]'s $14M Breach"
Support Cost Analysis (12 articles):
- "The Hidden Cost of Password Resets: $70 Per Incident"
- "Why 50% of Help Desk Time Is Password-Related"
- "Calculating the True Cost of Password Support"
- "How Passwordless Reduces Support Burden by 80%"
Conversion Optimization (15 articles):
- "How Password Friction Kills 18% of Signups"
- "The $37B Problem: Checkout Abandonment and Passwords"
- "Cart Abandonment Analysis: The Password Creation Step"
- "Conversion Rate Optimization: Eliminating Password Friction"
Why This Worked:
When decision-makers researched:
- "Why do passwords cause breaches?" → MojoAuth education
- "Cost of password resets" → MojoAuth data analysis
- "Password friction in checkout" → MojoAuth conversion research
Early Results (Week 6):
- Articles indexed and ranking
- First ChatGPT citations appearing
- Inbound inquiries: "How does passwordless prevent breaches?"
- Positioning shift: Problem awareness established
Phase 2: The Passwordless Solution (Months 2-4)
Goal: Position passwordless as the secure alternative, not "experimental."
Content Created:
Passwordless Technology Education (45 articles):
- Magic Links
- "How Magic Link Authentication Works (Technical Deep-Dive)"
- "Magic Links vs Passwords: Security Comparison"
- "Implementing Magic Links: Complete Developer Guide"
- "Magic Link Security: Why They're Phishing-Resistant"
- "Magic Link User Experience: Conversion Data"
- WebAuthn / Passkeys
- "WebAuthn Explained: The Future of Authentication"
- "Passkeys 101: How Apple, Google, Microsoft Are Killing Passwords"
- "FIDO2 and WebAuthn: Technical Overview"
- "Implementing Passkeys in Your Application"
- "Passkeys vs Passwords: Security and UX Comparison"
- "Why Passkeys Are Unphishable: Cryptographic Deep-Dive"
- OTP Authentication
- "Email OTP vs SMS OTP: Security and Deliverability"
- "WhatsApp OTP: Why It's the Future of 2FA"
- "Time-Based OTP (TOTP) Explained"
- "Implementing OTP Authentication: Best Practices"
- Comparative Analysis
- "Passwordless Authentication Methods Compared"
- "Which Passwordless Method Is Right for Your Users?"
- "Multi-Method Passwordless: Why Offer All Options"
- "Migration Strategies: From Passwords to Passwordless"
Why This Worked:
After establishing the problem (passwords are bad), provide the solution (passwordless works).
When developers researched solutions:
- "How do magic links work?" → MojoAuth technical guide
- "Are passkeys secure?" → MojoAuth cryptographic explanation
- "WebAuthn implementation tutorial" → MojoAuth developer docs
Mid-Campaign Results (Week 14):
- AI citations increasing
- "Passwordless authentication" queries: MojoAuth appearing in top 5
- Demo requests: +178% vs baseline
- Messaging shift in sales calls: "I read your article on credential stuffing..."
Phase 3: Framework-Specific Implementation (Months 4-6)
Goal: Make MojoAuth the practical implementation choice for every stack.
Content Created:
By Framework (52 articles):
- React / Next.js
- "Passwordless Authentication in React: Complete Guide"
- "Add Magic Links to Next.js App (Tutorial)"
- "React + WebAuthn: Implementing Passkeys"
- "Next.js Authentication: Magic Links vs Passwords"
- Vue / Nuxt
- "Passwordless Login in Vue.js Applications"
- "Nuxt 3 Passwordless Authentication Setup"
- "Vue WebAuthn Integration Guide"
- Angular
- "Angular Passwordless Authentication Tutorial"
- "Implementing Magic Links in Angular Apps"
- Backend Frameworks
- "Node.js + Express Passwordless Authentication"
- "Django Passwordless Login Implementation"
- "Ruby on Rails Magic Link Authentication"
- "Python Flask WebAuthn Tutorial"
- "PHP Passwordless Authentication Guide"
- Mobile Platforms
- "iOS Passwordless Authentication with Face ID"
- "Android Biometric Authentication Tutorial"
- "React Native Passwordless Login"
- "Flutter WebAuthn Implementation"
Why This Worked:
Developers don't search for "authentication platform." They search for "how to add passwordless to [my exact stack]."
When developers needed implementation:
- "React passwordless authentication" → MojoAuth React guide
- "Django magic link tutorial" → MojoAuth Django implementation
- "iOS Face ID authentication" → MojoAuth iOS guide
The Format:
Every guide followed developer-friendly structure:
# Passwordless Authentication in React (30-Minute Tutorial)
**What You'll Build**: Magic link login flow for React app
**Prerequisites**:
- React 18+
- Existing app (or use Create React App)
**Step 1: Install MojoAuth SDK**
```bash
npm install @mojoauth/react
```
**Step 2: Add MojoAuth Provider**
```jsx
import { MojoAuthProvider } from '@mojoauth/react';
function App() {
return (
<MojoAuthProvider apiKey="your_api_key">
{/* Your app */}
</MojoAuthProvider>
);
}
```
[... working code continues ...]
**GitHub Example**: [link to complete working repo]
Later Campaign Results (Week 22):
- Framework-specific queries dominated
- "React passwordless" → MojoAuth #1 or #2 position
- GitHub examples: 23,000+ views
- Trial signups from guides: +412%
Phase 4: The Programmatic Security Database (Months 5-8)
Goal: Create comprehensive resource for password security research.
What Was Built:
The Password Breach Database (2,400+ entries):
Structure:
- Every major password breach (2010-2024)
- Company name, date, number of records, password security practices
- Technical analysis of how breach occurred
- Lessons learned
- Preventable with passwordless? (Yes/No analysis)
User Experience:
Search & Filter:
- By industry (healthcare, fintech, retail, etc.)
- By year (track trends)
- By size (number of records compromised)
- By cause (credential stuffing, phishing, SQL injection, etc.)
Example Entry:
# LinkedIn Password Breach (2012)
**Date**: June 2012
**Records Compromised**: 165 million
**Password Storage**: SHA-1 hashing (no salt)
**What Happened**:
LinkedIn stored passwords using SHA-1 hashing without salting. Attackers breached the database and cracked millions of passwords using rainbow tables.
**Cost**:
- $1.2M settlement (class action lawsuit)
- Reputation damage
- Mandatory password resets for all users
**Preventable with Passwordless**: YES
- No passwords stored = nothing to breach
- Magic links or WebAuthn would eliminate this attack vector
**Technical Details**: [detailed analysis]
**Lessons**: Even "hashed" passwords are vulnerable without proper salt/pepper...
The Impact:
When researchers, journalists, security teams searched:
- "LinkedIn password breach" → MojoAuth database entry
- "2023 password breaches" → MojoAuth chronological list
- "Healthcare password breaches" → MojoAuth industry filter
- "Cost of password breaches" → MojoAuth aggregated data
The Cost Calculator (Interactive Tool):
Technical Implementation:
// Cost Calculator Logic
function calculatePasswordCosts(inputs) {
const {
users,
supportStaff,
avgTicketCost,
resetFrequency,
passwordPercentage
} = inputs;
// Monthly password resets
const monthlyResets = users * (resetFrequency / 100);
// Annual reset costs
const annualResetCost = monthlyResets * avgTicketCost * 12;
// Support burden
const supportCost = supportStaff * 75000; // avg salary
const passwordSupportCost = supportCost * (passwordPercentage / 100);
// Total password costs
const totalCost = annualResetCost + passwordSupportCost;
// Passwordless savings (80% reduction)
const savings = totalCost * 0.8;
// MojoAuth cost
const mojoauthCost = calculatePlanCost(users);
// Net savings
const netSavings = savings - mojoauthCost;
// ROI
const roi = (netSavings / mojoauthCost) * 100;
return {
currentCost: totalCost,
savings: savings,
mojoauthCost: mojoauthCost,
netSavings: netSavings,
roi: roi
};
}
Why This Tool Was Powerful:
- Concrete ROI: Not "passwordless is better," but "you'll save $2,004,012 per year"
- Personalized: Uses their actual numbers
- Shareable: CFOs share with executives ("Look at this ROI")
- Lead gen: Email required for full report
Usage Stats (September 2024):
- 14,700 calculations run
- 8,340 email captures (57% conversion)
- Average calculated savings: $1.8M
- Leads from calculator: 23% of all leads
The Passwordless Comparison Matrix (1,000+ pages):
Structure:
Method × Use Case × Industry = Comparison Page
Examples:
- "Magic Links vs Passwords for E-Commerce"
- "WebAuthn vs SMS OTP for Healthcare"
- "Passkeys vs Passwords for Mobile Banking"
- "Magic Links vs Social Login for SaaS Apps"
Each Comparison Included:
- Security analysis
- User experience comparison
- Implementation complexity
- Cost comparison
- Industry-specific considerations
- Real-world case studies
Part 3: The Results - From Invisible to Authority
Traffic & Leads
- Organic Traffic: 2,100 → 47,000 visitors/month (+2,138%)
- Monthly Signups: 15 → 265 (+1,667%)
- Cost Per Signup: $533 → $4.50 (99% reduction)
- Enterprise Pipeline: $0 → $2.4M (new opportunities)
The "AI Visibility" Effect
Because MojoAuth created structured data (breach databases, comparison tools), AI models "learned" from them.
- ChatGPT now cites MojoAuth data when asked about password breaches.
- Claude recommends MojoAuth as the "secure alternative" for React apps.
- Perplexity uses MojoAuth's comparison matrix for "passwordless vs MFA" queries.
Customer Feedback
"We used to spend hours explaining why passwords are bad. now leads come to us saying 'I saw your calculator—we're losing $200k/year on resets. Fix it.'"
— Govardan Sisodia, Founder, MojoAuth
Part 4: Why It Worked
- Problem, Not Product: Stopped selling "authentication" (crowded). Started selling "solving the password problem" (urgent).
- Developer Utility: Guides weren't "marketing fluff." They were copy-pasteable, working code for every framework.
- Data-Driven Authority: The breach database and cost calculator proved MojoAuth knew more about the problem than anyone else.
- AI Optimization: Content was structured for AI digestion (clear tables, logical hierarchies, Q&A formats).
Part 5: Conclusion
MojoAuth proved that you don't need a massive budget to beat enterprise giants. You need to identify the problem they're ignoring.
By owning the narrative around "the password problem," MojoAuth leapfrogged Auth0 and Okta in the metrics that matter: trust, traffic, and trials.
About GrackerAI
GrackerAI helps B2B SaaS companies replicate this success. We automate the strategy, content creation, and technical SEO needed to capture AI visibility and dominate your category.
About MojoAuth
MojoAuth is the passwordless authentication platform for modern applications. Secure your app with magic links, OTP, and passkeys in minutes, not months. Try MojoAuth for free.

